Threat Actors Target Government of Belarus Using CMSTAR Trojan
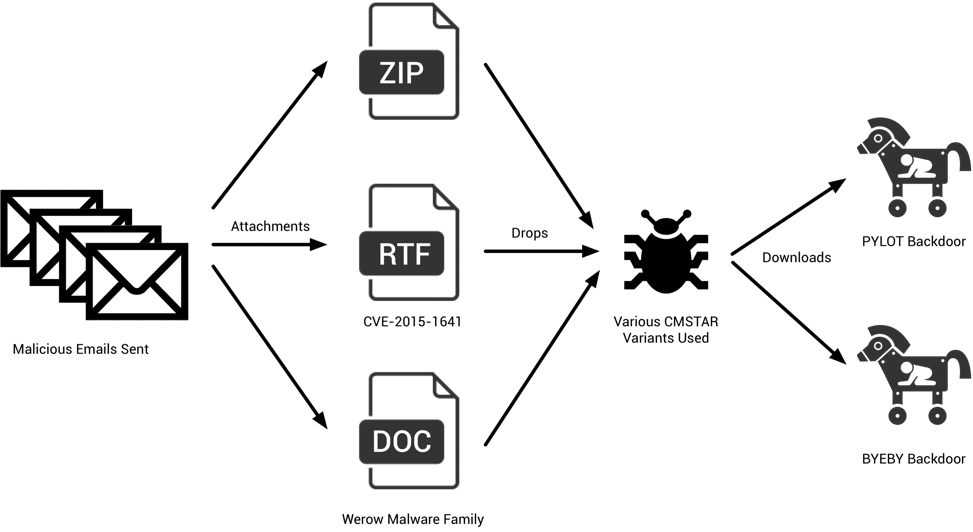
Palo Alto Networks Unit 42 has identified a series of phishing emails containing updated versions of the previously discussed CMSTAR malware family targeting various government entities in the country of Belarus.