
This post is also available in: 日本語 (Japanese)
In most cases, fake Flash updates pushing malware are not very stealthy. In recent years, such imposters have often been poorly-disguised malware executables or script-based downloaders designed to install cryptocurrency miners, information stealers, or ransomware. If a victim runs such poorly-disguised malware on a vulnerable Windows host, no visible activity happens, unless the fake updater is pushing ransomware.
However, a recent type of fake Flash update has implemented additional deception. As early as August 2018, some samples impersonating Flash updates have borrowed pop-up notifications from the official Adobe installer. These fake Flash updates install unwanted programs like an XMRig cryptocurrency miner, but this malware can also update a victim's Flash Player to the latest version.
Because of the legitimate Flash update, a potential victim may not notice anything out of the ordinary. Meanwhile, an XMRig cryptocurrency miner or other unwanted program is quietly running in the background of the victim's Windows computer.

Figure 1: Flow chart for this activity
Trends
While searching for these particular fake Flash updates, we noticed Windows executables file names starting with AdobeFlashPlayer__ from non-Adobe, cloud-based web servers. These downloads always contained the string flashplayer_down.php?clickid= in the URL. We found 113 examples of malware meeting these criteria since March 2018 in AutoFocus. 77 of these malware samples are identified with a CoinMiner tag in AutoFocus. The remaining 36 samples share other tags with those 77 CoinMiner-related executables. See Appendix A for the full list of the file hashes.
Appendix B lists 473 file names and URLs for these fake Flash updates from March 25th, 2018 through September 10th, 2018.
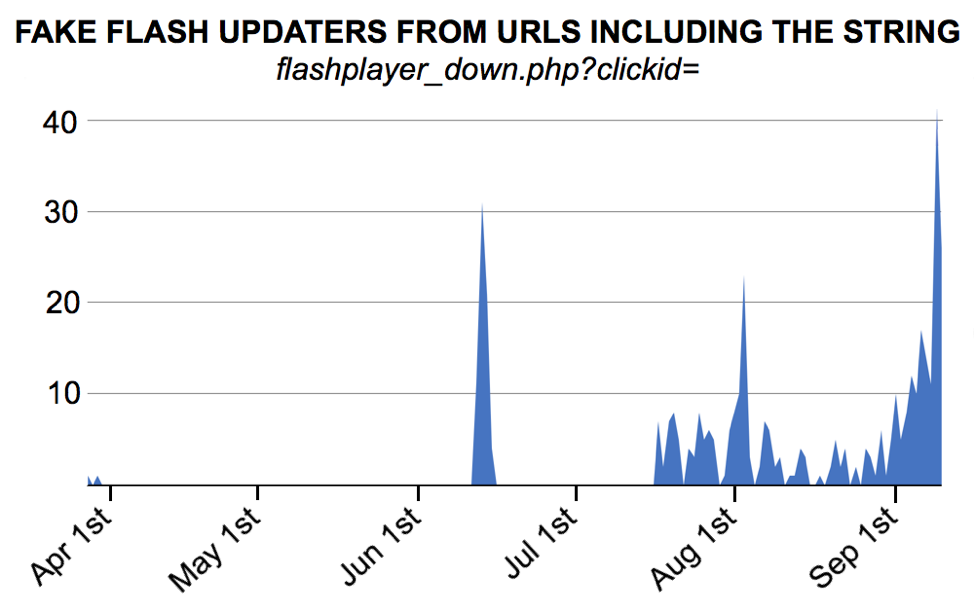
Figure 2: Number of fake Flash updaters from this campaign.
Details
Based solely on AutoFocus data, I could not determine how potential victims were arriving at these URLs delivering fake Flash updates. However, I tested a sample on August 24th, 2018 with the SHA256 hash 485352a3985bce69a020dc49e970fde337279eb1986ea699ca6bec1f5a8068ac. This sample generated Adobe Flash installer popup windows and a Flash Player installation. An XMRig Cryptocurrency miner then worked in the background of my infected Windows host. Potential victims will receive warnings about running such downloaded files on their Windows computer. On a host in my test environment running Windows 7 Service Pack 1, I double-clicked one of the samples. Windows provided a typical warning about an unknown publisher that victims can easily click through on vulnerable Windows hosts.
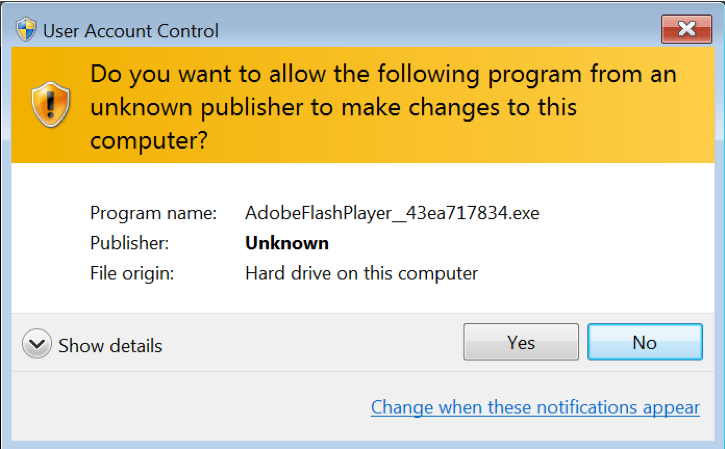
Figure 3: A warning when running the fake Flash updater.
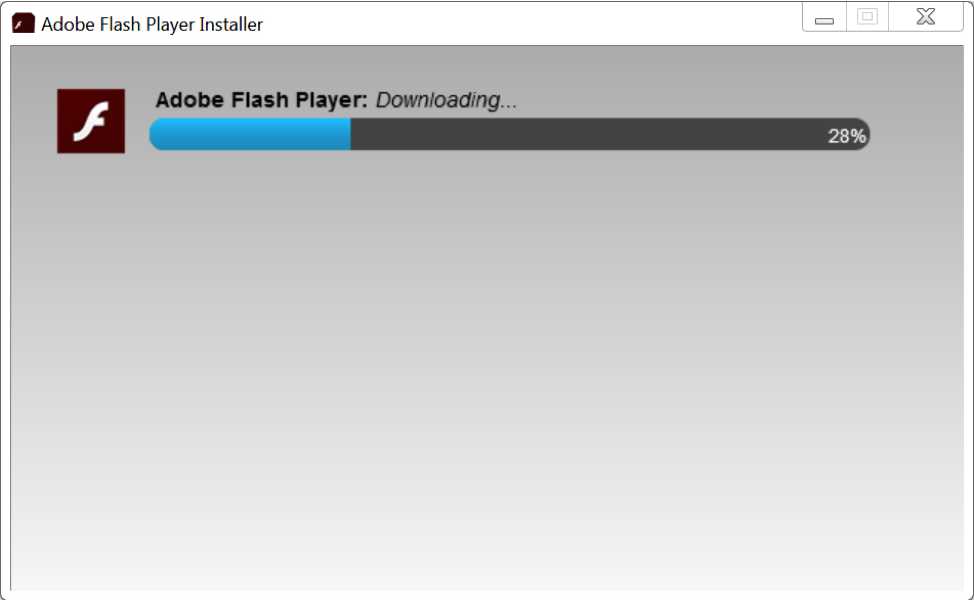
Figure 4: After running the program, it downloads an actual Flash Player from Adobe.
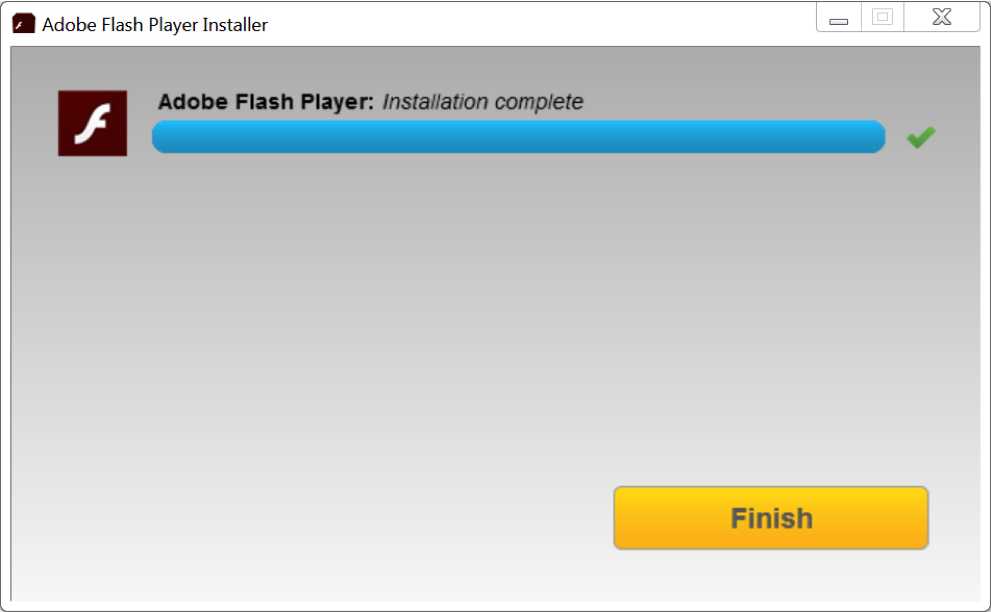
Figure 5: These windows are part of a real Flash Player installation.
Figure 6: The installation process finally asks you about Flash updates.
Figure 7: Page from Adobe thanking you for installing Flash Player.
Figure 8: Flash Player was updated to the latest version on my lab host.
Network traffic during the infection consisted mainly of the Flash update. But my infected lab host soon generated traffic associated with XMRig cryptocurrency mining over TCP port 14444. The Monero wallet used for this miner was 41ompKc8rx9eEXtAAm6RJTTm6jg8p6v3y33UqLMsUJS3gdUh739yf7ThiSVzsU4me7hbtVB61rf7EAVsJeRJKGQH4LFi3hR.
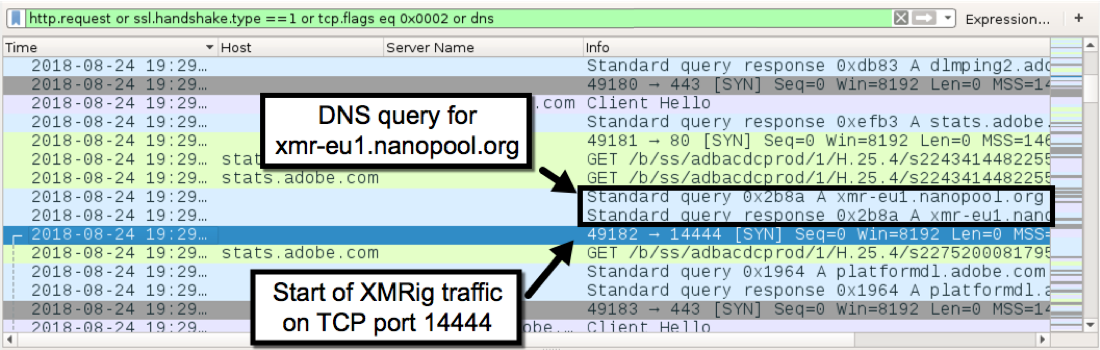
Figure 9: Infection traffic filtered in Wireshark, showing start of XMRig traffic.
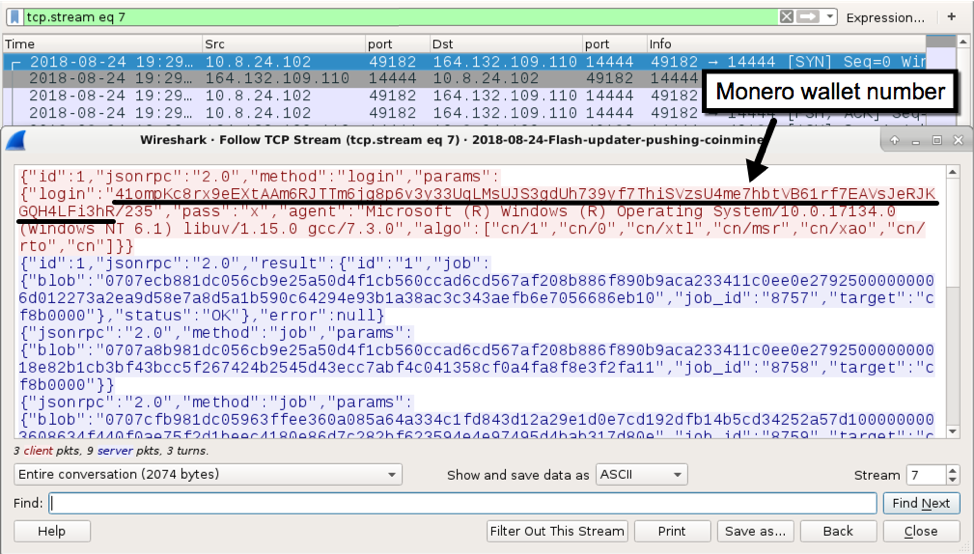
Figure 10: XMRig traffic with the Monero wallet number.
Near the beginning of the traffic, my infected Windows host generated an HTTP POST request to osdsoft[.]com. This domain is associated with updaters or installers pushing cryptocurrency miners and other unwanted software. One such example from December 2017 named free-mod-menu-download-ps3.exe also shows osdsoft[.]com followed by XMRig traffic on TCP port 14444 like the example used in this blog. However, other malware samples reveal osdsoft[.]com is associated with other unwanted programs usually classified as malware.
Conclusion
This campaign uses legitimate activity to hide distribution of cryptocurrency miners and other unwanted programs. Organizations with decent web filtering and educated users have a much lower risk of infection by these fake updates.
Palo Alto Networks customers are further protected from this threat. Our threat prevention platform detects this type of malware. And AutoFocus users can track this activity by combining the CoinMiner tag with the appropriate search parameters.
Appendix A
113 malware examples for these fake Flash updaters found in AutoFocus. Information is available at https://github.com/pan-unit42/iocs/blob/master/fake_Flash_updates/2018-09-fake-Flash-updates-APPENDIX-A.txt
Appendix B
473 file names and associated URLs for fake Flash updates found in AutoFocus. Information is available at https://github.com/pan-unit42/iocs/blob/master/fake_Flash_updates/2018-09-fake-Flash-updates-APPENDIX-B.txt
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
