Recently, we found email accounts from top universities across the world being sold on Taobao, the largest consumer-to-consumer (C2C) e-commerce platform in China. Advertised uses for these accounts included registering for special accounts under software developer programs, receiving student discounts or coupons from retailers, and obtaining access to academic databases. This post describes the scope, associated risks, and implications of this activity.
Our investigation began with a Chinese language search for "edu mailbox" in Taobao, which returned 99 results related to stolen university email accounts. The most expensive account was listed at ¥2400 RMB ($390.80 USD), while the cheapest was only ¥0.98 RMB ($0.16 USD).
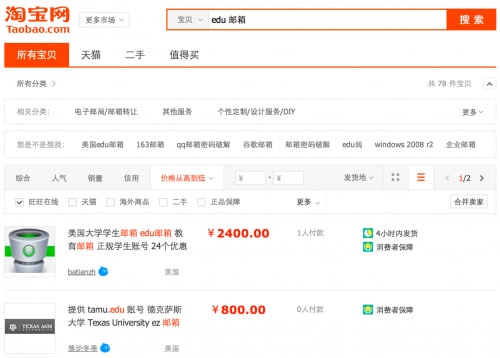
Figure 1: Results for Chinese language "edu mailbox" search on Taobao.
These accounts, which include an education (EDU) top-level domain email address with valid password, represent 42 of the world’s top universities, across 10 countries:
Australia:
- The University of Melbourne
Canada:
- Toronto University
China:
- South East University
- Peking University
- Tsinghua University
- Fudan University
- Nanjing University
- Shanghai Jiao Tong University
- Hong Kong Polytechnic University
- Hong Kong University
- Nanjing University of Finance & Economics
- Hunan University
- Tongji University
- China University of Geosciences
- China University of Petroleum
- Northwest University
Denmark:
- Aarhus Universitet
Italy:
- Università di Bologna
Singapore:
- Nanyang Technological University
- NUS Singapore University
Sweden:
- Karolinska Institutet
Switzerland:
- ETH Zürich
United Kingdom:
- Imperial College London
United States:
- Massachusetts Institute of Technology
- Stanford University
- Yale University
- Princeton University
- Harvard University
- Purdue University
- Columbia University
- Cornell University
- The University of Texas, Austin
- New York University
- University of California, Merced
- Texas A & M University
- University of Michigan
- Southern Illinois University
- George Washington University
- Duke University
- University of Illinois at Chicago
- University of New Hampshire
- The University of Chicago
The sellers guaranteed that all email accounts were valid, accessible, and active. The descriptions for these items proposed three main uses for buyers:
1. Registering for special accounts under software developer programs: For example, the most popular account type, which has been bought at least 569 times, was advertised as a Microsoft’s student Windows Phone 7 and 8 developer account. By using this kind of account, a user can perform a developer unlock on their Windows Phone devices without incurring a fee. Most reviews of this package were favorable, with comments like "very good to use" or "with seller’s help I can unlock my phone now."
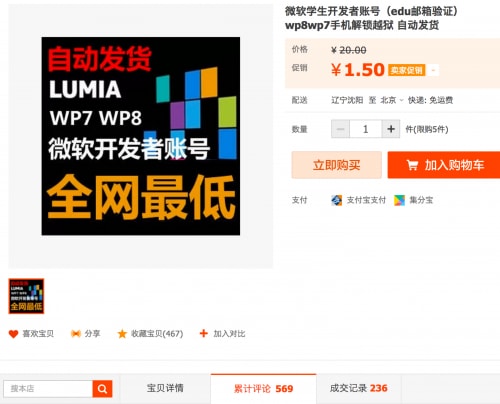
Figure 2: The most popular account type has sold at least 569 times.
2. Receiving student discounts or coupons from retailers: Some accounts advertised candidacy towards registration for student discount at retailers such as Amazon, BestBuy, Apple, and Dell. For example, the standard annual fee for Amazon Prime is $99 USD; however, with the student discount, a buyer could enjoy it for free the first six months and then renew at half price for subsequent years.
Figure 3: The seller showed how to register for student discount accounts.
3. Obtaining access to academic databases: Accounts for big universities (e.g., MIT, Stanford, etc.) are mainly used to access respective library services and resources, "including research help, study spaces, print and electronic books/journals and more."
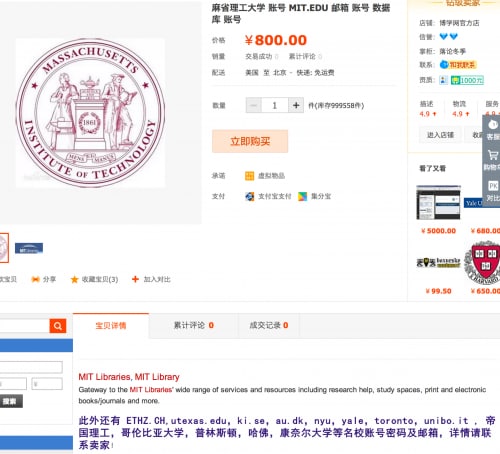
Figure 4: A seller advertises how an MIT account can be used to access online library resources.
We talked with some sellers through AliWangWang, an instant message (IM) system developed by Taobao for online trading. A well-stocked seller told us that every account he sold belonged to an active student at the respective university. He claimed that once the account was sold, only the one buyer and the legitimate user would have access. He recommended not changing the account password to avoid detection by the legitimate user. Another seller offered to provide real identity information for a stolen account so the buyer could change the corresponding password and security questions. This type of account access was the most expensive and least flexible in terms of customization (i.e., username, institution, etc.). Additionally, it should be noted that there is value beyond the EDU account itself for password and security question information, in the event they are shared across other online accounts for the legitimate user.
Other sellers were also able to offer customizable email accounts from a specific domain/institution.
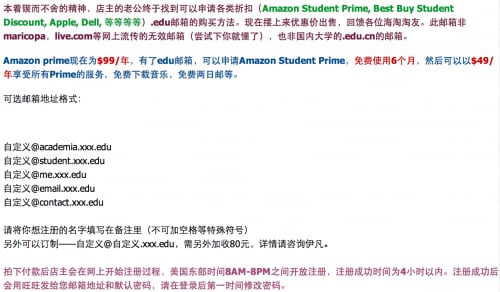
Figure 5: A seller advertising a customizable “xxx.edu” email account.
In the above advertisement, the seller describes the ability to choose an account under a subdomain (academia, student, me, email, or contact) of the requested domain. The price for this custom account was only ¥27 RMB ($4.40 USD); for an extra ¥13 RMB ($2.12 USD), the buyer can request a custom username at any subdomain for the given institution.
To further assess this threat, we purchased a customized, new account from a seller on Taobao. Four hours later, we received confirmation that the custom email address "claud@student.cnri.edu" was active. Navigating to CNRI’s webmail page, we were then able to successfully access and send an email from that account.
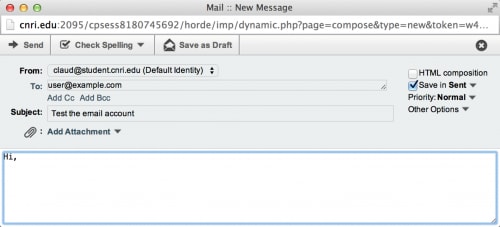
Figure 6: Sending an email through a newly bought customized EDU account.
Another noteworthy trend we observed was that some sellers provided email addresses with customizable usernames at "californiacolleges.edu". In fact, anyone can do the same by visiting the California Colleges Create an Account page. Accounts made through this site "can be used to apply [for] related memberships of Amazon Prime, Microsoft Developer, Adobe and Apple by some secret ways," one seller said.
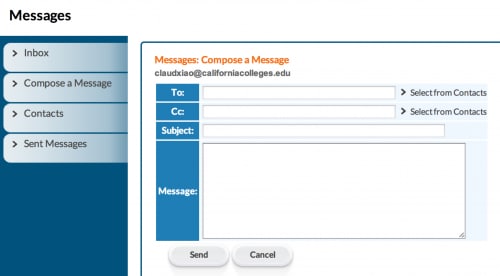
Figure 7: Using a newly created California Colleges account.
As with most criminal enterprises, not all sellers on Taobao use their real identity, presenting a challenge in tracking down the individuals behind this activity. In order to sell anything on Taobao, a seller must at least create a valid Alipay account (similar to PayPal) linked to a valid Chinese citizen ID number (similar to a U.S. Social Security number), and then associate it with a valid Chinese bank account under the same citizen ID. However, identity theft is a global concern and the Chinese citizen ID is no exception, allowing for potential sellers to simply purchase a usable identity online.
Based on our investigation, we believe that stolen accounts for these universities are actively selling on Taobao. On August 27, we reported our findings to Taobao. Their response was that they were addressing this issue and have already removed a number of these items, with the remainder requiring further investigation. However, this malicious seller activity may also reveal a larger scale problem within university systems. Through the types of accounts advertised on Taobao, an attacker can steal a student or staff account, assume their identity, and gain unauthorized access to standard university resources. More sophisticated and nefarious uses include leveraging accounts in social engineering/phishing attacks or exploiting access to high-value university systems (e.g., personnel, financial, research) to steal information. Fortunately, a number of the institutions impacted by this activity have already implemented two-factor authentication for high-value resources, reducing the risk of the latter. Yet, we believe the residual risk and exposure call for further action.
The following are our suggestions for discovering and mitigating risks associated with this activity:
- Anomaly detection: Search for anomalous login sessions, focusing on country/location disparities in near timeline proximity.
- Remediation: Depending on the findings from subsequent investigation, prepare for the timely correction of the root cause for account information leakage and the potential need to reset all existing account passwords.
- Mitigation: Advise account holders against sharing passwords and/or security question information across multiple online systems. This limits the scope of a single set of compromised credentials to one system/environment, versus potentially exposing multiple online accounts. On the technical side, increasing adversarial effort/cost and reducing the impact of advanced attacks can be achieved through network segmentation and two-factor authentication (at a minimum for high-value computing and information resources).
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
