On April 11th 2017, we saw a new malicious spam campaign using United States Postal Service (USPS)-themed emails with links that redirected to fake Microsoft Word online sites. These fake Word sites asked victims to install malware disguised as a Microsoft Office plugin.
This campaign introduced a new ransomware called Mole, because names for any encrypted files by this ransomware end with .MOLE. Mole appears to be part of the CryptoMix family of ransomware since it shares many characteristics with the Revenge and CryptoShield variants of CryptoMix.
The campaign quickly changed tactics and increased complexity.
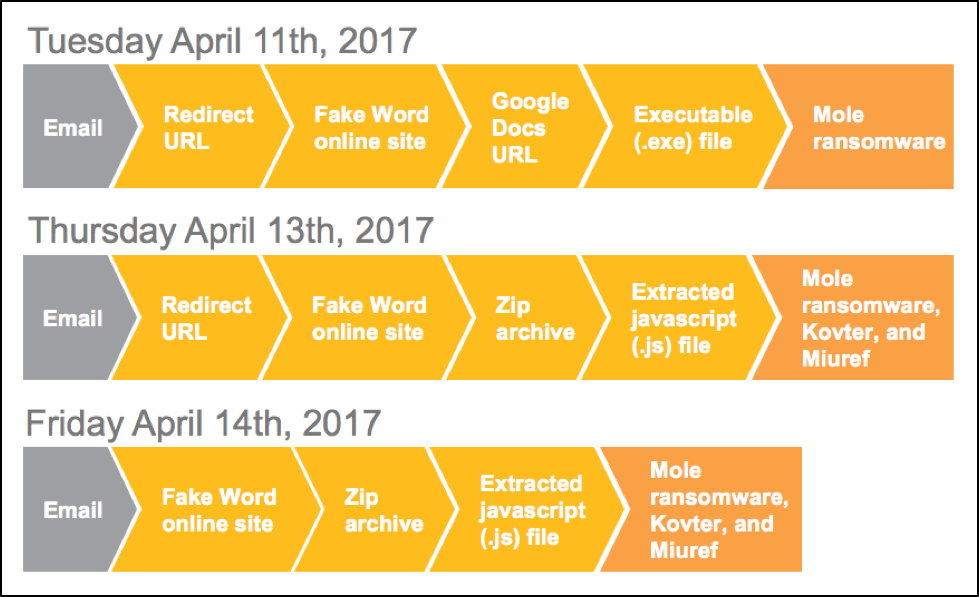
After two days on April 13, 2017, the attackers behind these fake office plugins changed the format and began including additional malware. Along with Mole ransomware, victims would be infected with both Kovter and Miuref. Then, on the following day, April 14, 2017, the attackers stopped using a redirect link in the malicious spam and instead linked directly to a fake Word online site. Figure 1 shows the attackers' changing tactics from Tuesday April 11, 2017 through Friday April 14, 2017.
Figure 1: Changing tactics April 11 - April 14, 2017
April 11th - Introducing Mole Ransomware
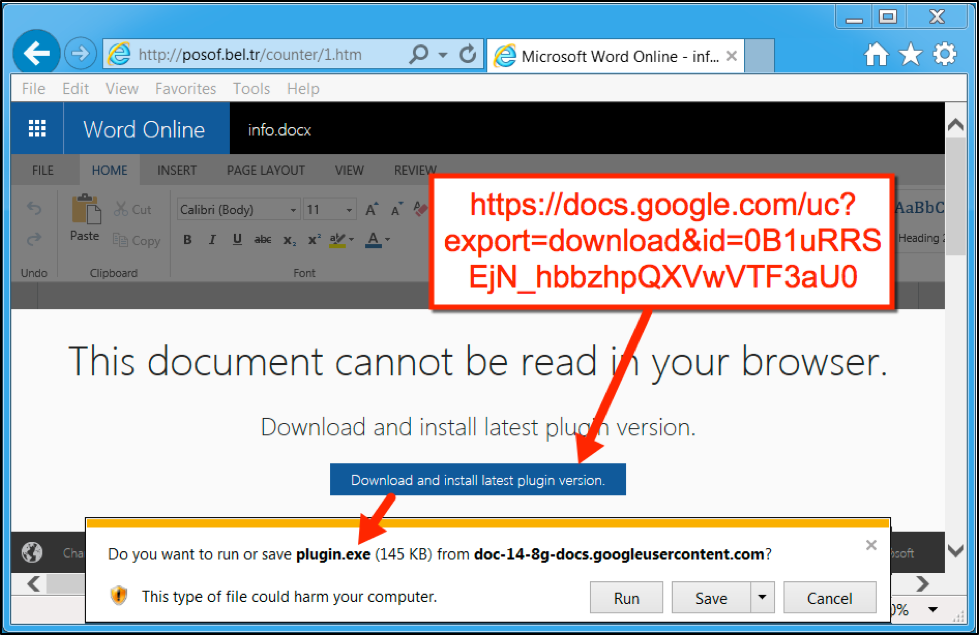
From Tuesday April 11th to the early hours of Wednesday April 12th, the fake Word Online used Google Docs links to provide Mole ransomware disguised as an Office plugin. Criminals behind this campaign abused Google Docs to provide a link for an executable file. File names were plug-in.exe or plugin.exe. Figure 2 shows how these fake Microsoft Word Online documents would attempt to lure users into downloading the Mole ransomware.
Figure 2: Fake Microsoft Word Online site with link to a Google Documents URL with the ransomware.
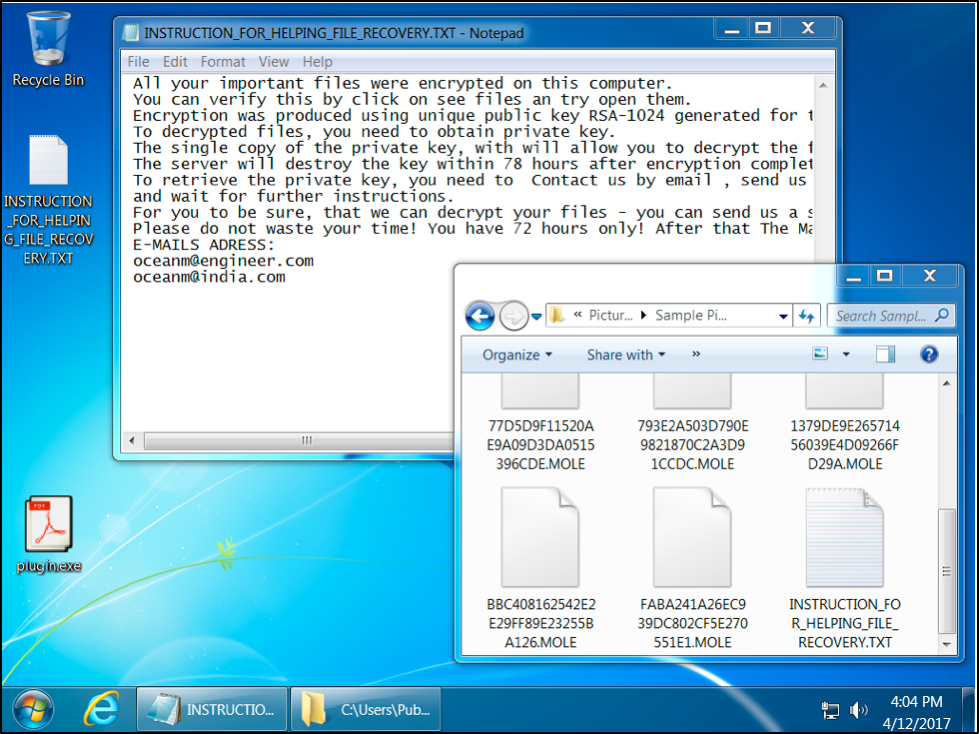
After downloading the executable, the infection chain is straight-forward. The victim executes the ransomware and infects his or her Windows computer. The mechanics behind a Mole ransomware infection have already been covered at the Internet Storm Center (ISC) and Bleeping Computer. Figure 3 shows the April 12 Mole ransomware in action.
Figure 3: Desktop of a Windows host infected with Mole ransomware on April 12th
April 13th - Introducing .js Files and Additional Malware
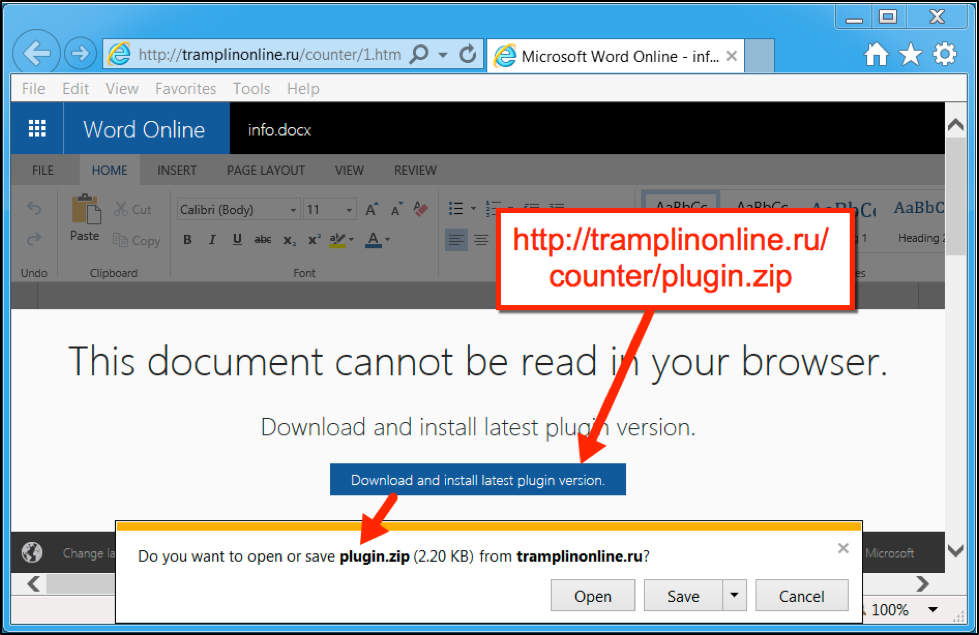
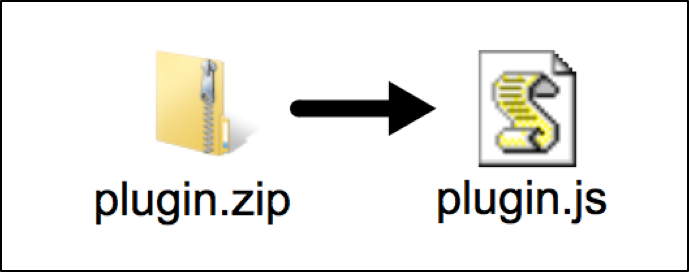
By Thursday April 13, 2017, this campaign changed tactics. The fake Microsoft Word Online sites no longer used a Google Docs URL to provide their malware. Instead, the malware was sent as a zip archive directly from the compromised site being used as a fake Microsoft Word Online page. The zip archives contained JavaScript (.js) files designed to infect Windows computers with Mole ransomware and additional malware.
The Figures 4 and 5 below illustrate the newer format used for malware infections by this campaign, where the new file is a zip archive named plugin.zip that contains a .js-based downloader named plugin.js.
Figure 4: Fake Microsoft Word Online site later on April 13th with link to a zip archive instead of an executable
Figure 5: The zip archive contains a .js file
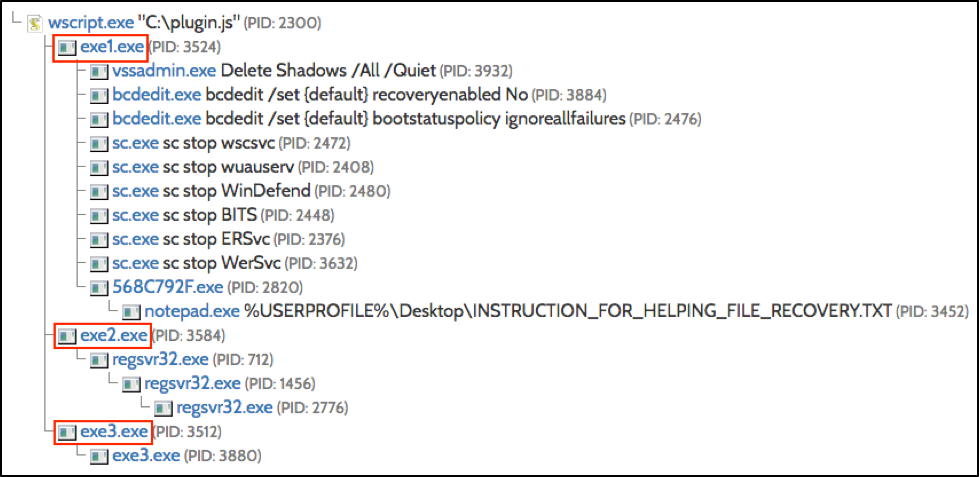
The plugin.js is a type of file downloader commonly called a Nemucod. This .js file downloads and installs three Windows executable files named exe1.exe, exe2.exe, and exe3.exe as shown below in Figure 6.
Figure 6: Plugin.js installing 3 items of malware as shown in a reverse.it analysis
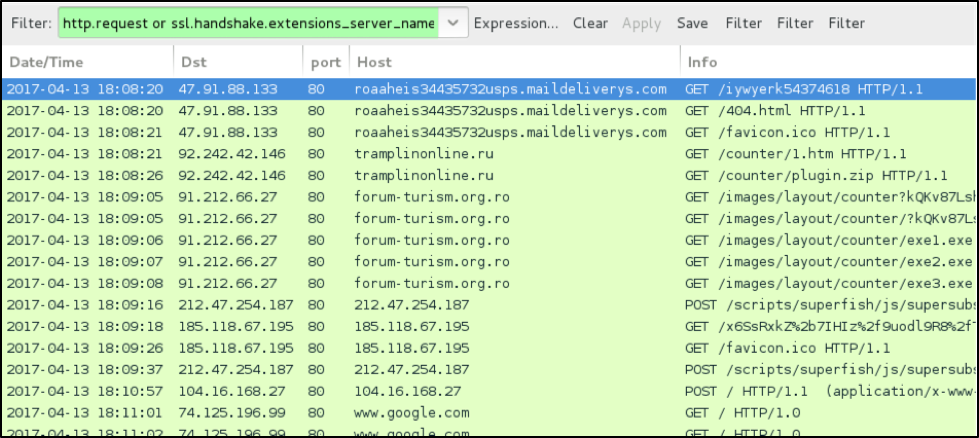
Network traffic generated by this infection is similar to Nemucod downloaders we have seen from other campaigns. In Figure 7 below, you can see URLs for exe1.exe, exe2.exe, and exe3.exe from forum-turism.org.ro.
Figure 7: Traffic from an infection filtered in Wireshark
The three items of follow-up malware are named exe1.exe, exe2.exe, and exe3.exe. In the early days of this campaign, they have been Mole ransomware, Kovter, and Miuref, respectively.
The Emails
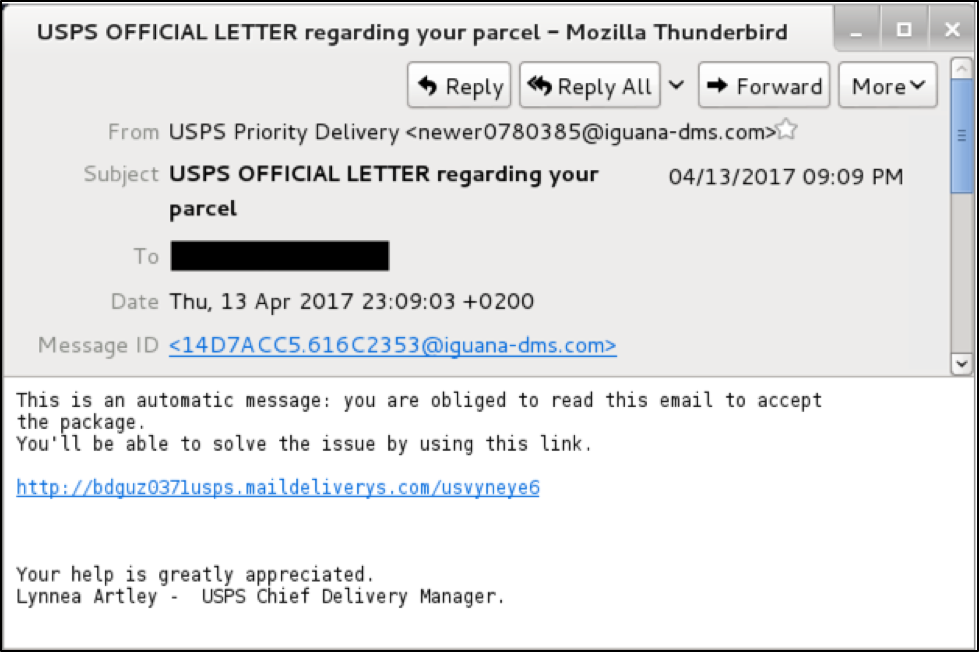
Figure 8: An example of the malicious spam from Thursday April 13th
Emails from this campaign follow the same format as originally reported from Tuesday April 11, 2017. Figure 8 above shows an example email. They have a variety of subject lines, spoofed sending email addresses, and message text. Through Thursday April 13, 2017, the URLs were different for each message. By Friday April 14th, these emails were linking directly to the fake Microsoft Word Online pages, so the URLs for that day were the same.
Conclusion
Most large-scale malicious spam campaigns tend to stick with operating patterns that are much easier to identify and track. This particular campaign has evolved more quickly than we usually see. Such changing tactics are likely a way to avoid detection.
And this campaign continues to evolve. By Tuesday April 18, 2017, it stopped distributing Mole ransomware, and it began pushing the KINS banking Trojan with Kovter and Miuref. By Friday April 21, 2017, this campaign moved from USPS-themed emails to messages about speeding tickets, and it began utilizing a fake parking services website.
Why did we stop seeing Mole ransomware? Because families of ransomware are constantly changing. CryptoMix variants like Mole rarely stay around for more than a few weeks before being repackaged and distributed as a new variant. The samples of Mole ransomware we have identified so far are tagged in AutoFocus using the MoleRansomware tag.
We will continue to investigate this activity for applicable indicators to inform the community and further enhance our threat prevention platform.
Indicators from this campaign
Subject lines:
- ATTENTION REQUIRED: INFO ON YOUR IMPENDING REFUND
- ATTENTION REQUIRED: INFORMATION ON YOUR LATEST REFUND
- ATTENTION REQUIRED: you are legally obliged to review the status of your shipment
- AUTOMATED letter: refund information
- AUTOMATED notice in regards to your item's status
- AUTOMATED notification: refund information
- AUTOMATED notification: refund information
- AUTOMATED USPS notification: your shipment has been postponed
- AUTOMATED USPS OFFICIAL LETTER CONCERNING YOUR SHIPMENT
- AUTOMATED USPS statement: your package has been delayed
- AUTOMATIC letter: moneyback information
- AUTOMATIC notice concerning your package's location
- AUTOMATIC notice: refund information
- AUTOMATIC notification in regards to your package's status
- AUTOMATIC notification regarding your order's location
- IMMEDIATE ATTENTION NEEDED: your parcel's been delayed
- IMMEDIATE ATTENTION REQUIRED: your parcel's been delayed
- IMPORTANT USPS customer support letter
- IMPORTANT USPS REFUND INFO
- IMPORTANT USPS REFUND INFORMATION
- IMPORTANT USPS system notice
- Major problems reported to the USPS support team
- Major trouble reported to the USPS customer support
- Official letter from USPS support team
- Official letter in regards to your parcel
- Official notice from USPS support team
- Official notification concerning your package
- Official notification from USPS
- Official notification from USPS customer support team
- OFFICIAL USPS MONEYBACK INFO REGARDING YOUR ITEM
- OFFICIAL USPS MONEYBACK INFORMATION
- Official USPS notification concerning your package
- PROMPT ACTION NEEDED: your order's been delayed
- PROMPT ATTENTION NEEDED: your item's been delayed
- There has been an issue with your package
- There's been an issue with your package
- URGENT USPS customer support letter
- URGENT USPS customer support notification
- URGENT USPS MONEYBACK INFORMATION REGARDING YOUR ITEM
- URGENT: notice of postponement of your order
- USPS CLIENT IMPORANT NEW DETAILS REGARDING YOUR PACKAGE
- USPS CLIENT IMPORANT NEW INFORMATION REGARDING YOUR ITEM
- USPS customer support notification: your order has been postponed
- USPS OFFICIAL LETTER regarding your parcel
- USPS official letter: big problems with your shipment
- USPS official letter: serious issues with your order
- USPS official letter: serious problems with your shipment
- USPS official notice: serious trouble with your parcel
- USPS official notification: serious issues with your package
- USPS system notice: your package has been delayed
- USPS system notification: your package has been delayed
- USPS URGENT LETTER concerning your item
- USPS USER URGENT NEW INFO IN REGARDS TO YOUR PARCEL
- WARNING: DETAILS ON YOUR IMPENDING REFUND
- WARNING: INFORMATION ON YOUR LATEST REFUND
- WARNING: ISSUES WITH YOUR SHIPMENT
- WARNING: PROBLEMS WITH YOUR PACKAGE
- WARNING: TROUBLE WITH YOUR ITEM
- WARNING: TROUBLE WITH YOUR SHIPMENT
- WARNING: you are legally obliged to check the status of your order
Spoofed sending addresses (not from the actual domains listed):
- "USPS Delivery" <gyjkzau603@abramarketing.com>
- "USPS Express Delivery" <ebosuey27523@westusa.com>
- "USPS Ground Support" <sa67117644@bibik.com.sg>
- "USPS Ground Support" <tijcucey17858440@thefringesalonandspa.net>
- "USPS Ground Support" <wucyieal26@laurencehart.com>
- "USPS Ground" <awfeoq42111421@theartofsmiles.com>
- "USPS Ground" <emcijizu43@lornalloyd.co.uk>
- "USPS Ground" <geavpet531656@travis-com.com>
- "USPS Ground" <gelerina3705@shubhammetals.com>
- "USPS Ground" <oe60568@laxsun.co.in>
- "USPS Ground" <qwc6826628@symbionpharmacy.com>
- "USPS Ground" <ranrays1371636@methowvalleynews.com>
- "USPS Ground" <sosarrij87661705@intergsa.com.my>
- "USPS Ground" <syapota57504662@simon-reid.co.uk>
- "USPS Ground" <ymuzjmwy22030784@dvs.net>
- "USPS Home Delivery" <ddixnuty272104@helendowsley.com.au>
- "USPS Home Delivery" <ebeyzhmo3057833@premiereeye.com>
- "USPS Home Delivery" <iix61312867@briarcliffstables.com>
- "USPS Home Delivery" <ksacugo02105401@korabl-love.ru>
- "USPS Home Delivery" <lzaikja068473@vintwine.com>
- "USPS Home Delivery" <pfne3616038@heavyrods.com>
- "USPS Home Delivery" <waj74534@rebeccasturdy.com>
- "USPS Home Delivery" <xasa31221@nsksofia.eu>
- "USPS Home Delivery" <xxgap86162407@sharethinkact.co.uk>
- "USPS Home Delivery" <yuovior03871347@triplecores.com>
- "USPS International" <kihuw88@rcoverdale.co.uk>
- "USPS International" <oxioyo5221364@apazen.ro>
- "USPS International" <tffmu810@egoldentriangle.com>
- "USPS Parcels Delivery" <aawuprug810545@kylegbrown.com>
- "USPS Parcels Delivery" <atza2045685@gsb.columbia.edu>
- "USPS Parcels Delivery" <diaam8408270@isiamerica.com>
- "USPS Parcels Delivery" <eabzs1@leonardgray.co.uk>
- "USPS Parcels Delivery" <fyzojuxo46014074@kelleysindia.com>
- "USPS Parcels Delivery" <iytkd87@svbbed.com>
- "USPS Parcels Delivery" <uino7757@kentschool.cl>
- "USPS Parcels Delivery" <vuijpyf0607532@o4icolombia.com>
- "USPS Priority Delivery" <a53@websealinc.com>
- "USPS Priority Delivery" <newer0780385@iguana-dms.com>
- "USPS Priority Delivery" <vdymoi2584835@solind.com.au>
- "USPS Priority Parcels" <r4448011@lovethatsmile.net>
- "USPS Priority" <coy5@uchiyamagroup.com>
- "USPS Priority" <huroim3@rickone.com>
- "USPS Priority" <mau4087171@ask-sevgi.net>
- "USPS Priority" <o57678@ibiza-real-estate.ru>
- "USPS Priority" <oheeruak05250@nexusv.com>
- "USPS Priority" <qoeq285@cottageindustriesinc.com>
- "USPS Priority" <saayota4044706@garrett-hedlund.com>
- "USPS SameDay" <rnoqoi60870482@bantenhosting.net>
- "USPS Station Management" <jyee528@luciq.com>
- "USPS Station Management" <xejmooa55752638@gayson.co.in>
- "USPS Station Management" <zuealee038700@jacobsens.com>
- "USPS Support Management" <cihiawru116425@raltrad.net>
- "USPS Support Management" <fx7061835@coep.ufrj.br>
- "USPS Support Management" <yenxee27@stela.org.br>
- "USPS Support" <aumvic36@ariainsaat.com>
- "USPS Support" <eetuwusj402634@e-senzaz.com>
- "USPS Support" <i610245@baayadesign.com>
- "USPS Support" <ifizy41225574@brianseger.com>
- "USPS Support" <iqeyqozo35540355@wesleyvillagemacomb.com>
- "USPS TechConnect" <vodiybwi72734156@hira.or.kr>
Links from the emails on Wednesday, April 12:
- uspsaeyyuia158140.ideliverys[.]com/ioxoory254772
- uspsbhusisoz75.ideliverys[.]com/aagupto83
- uspsboodud3731016.ideliverys[.]com/rzgyjotv3883685
- uspsekakozq20701607.ideliverys[.]com/ciyjfm1453247
- uspsfeu3245443.ideliverys[.]com/aivio24273
- uspsgcoez80061682.ideliverys[.]com/ipeetol5862
- uspsieibh26357.ideliverys[.]com/yey40177
- uspsirokgouu81321536.ideliverys[.]com/wokivy5257
- uspskposiuo204.ideliverys[.]com/ffauemyi1162
- uspslycoddja50715724.ideliverys[.]com/mnqnoh53682573
- uspsnarkk75185.ideliverys[.]com/syf11145060
- uspsrekeky57218225.ideliverys[.]com/qi72870401
- uspssenluefc87752667.ideliverys[.]com/pukooe40275334
- uspstucaej4570.ideliverys[.]com/pbpylye22012283
- uspsuhz63110412.ideliverys[.]com/t48844775
- uspsuuesylmz2162311.ideliverys[.]com/yorixaig28
- uspswmeeeny3538455.ideliverys[.]com/fgyzi77
- uspsyhiwejug182483.ideliverys[.]com/gjesul74180
- uspszovuoody3241005.ideliverys[.]com/deoa382
- uspszujoea26262.ideliverys[.]com/vzy575324
Links from the emails on Thursday, April 13:
- aexhnneq102342usps.maildeliverys[.]com/kovcemaw707572
- bdguz0371usps.maildeliverys[.]com/usvyneye6
- ebzizebk4124157usps.maildeliverys[.]com/uotajyax507
- eccov13346821usps.maildeliverys[.]com/natyxr51034320
- finupriw75037usps.maildeliverys[.]com/qaqabxei76122420
- hoemurha6838215usps.maildeliverys[.]com/becevo581082
- hwyrztkj8023435usps.maildeliverys[.]com/lyiaf13610344
- ibaoe40687236usps.maildeliverys[.]com/vevroyo40678322
- juo635usps.maildeliverys[.]com/hijxe7411
- pehoaki1160481usps.maildeliverys[.]com/mvaklhma54511567
- pfinyryf551041usps.maildeliverys[.]com/gsr58503
- poyjsofq7716usps.maildeliverys[.]com/irirorcq3818
- py18usps.maildeliverys[.]com/ou0453
- rafoyky41usps.maildeliverys[.]com/ke244
- roaaheis34435732usps.maildeliverys[.]com/iywyerk54374618
- tenyti58325153usps.maildeliverys[.]com/mogfulep66534
- ucasucu5264usps.maildeliverys[.]com/irwoqoqy563108
- xicyw707845usps.maildeliverys[.]com/kyzupyi74721211
- yfypus7588300usps.maildeliverys[.]com/n807837
- zfsiqyjh4508687usps.maildeliverys[.]com/woorutu63408454
Links from the emails on Friday, April 14:
- anilstone[.]ir/libraries/joomla/string/wrapper/counter/1.htm
Associated file hashes:
SHA256 hash: 8e210658f17a265f0c595b4f63ee7ba3db4c83f64c93f522e74e57e6fc547b11
- File name: plugin.exe
- File size: 149,346 bytes
- File description: Mole ransomware from thru Google Docs URL on April 12th
SHA256 hash: b36a3a9e2b9129cbe7385c97fa24666d2d086f7bb8a3c9c4e019f14a41538be0
- File name: plugin.js
- File size: 1,369 bytes
- File description: Contents of plugin.zip from tramplin.online[.]ru on April 13th
SHA256 hash: a1670db6204f7666ad246cc11736b052713a4413663f5cbe6aec90ab299431a7
- File name: plugin.js
- File size: 1,537 bytes
- File description: Contents of plugin.zip from mattsfotoalbum[.]de on April 13th
SHA256 hash: 40e8dc147f189baf4660d5db8e0cd1c647c7f167f7176c5d8ee03b6cac26fed2
- File name: plugin.js
- File size: 1,382 bytes
- File description: Contents of plugin.zip from anilstone[.]ir on April 14th
SHA256 hash: 3b5b19ebe8d8b6c7e5b2ffd2cc194fad1ae6c9eade7646f48c595bd154f4b1e1
- File name: exe1.exe
- File size: 85,504 bytes
- File description: Mole ransomware (follow-up malware retrieved by plugin.js on April 13th)
SHA256 hash: 50117ce3fe5dba572cf23584dc7541a7cfd4026d4316e69d29cdf536873fdf20
- File name: exe1.exe
- File size: 91,136 bytes
- File description: Mole ransomware (follow-up malware retrieved by plugin.js on April 14th)
SHA256 hash: d9189f6df89acf8e2f0d689ab73429cde37f974ed423f91d1bcabfe5dda700fa
- File name: exe2.exe
- File size: 366,249 bytes
- File description: Kovter malware (follow-up malware retrieved by plugin.js on April 13th)
SHA256 hash: 41f171eb916d555dc7771ce71013572c498b8d620d2f72872c4b2f3b50c7ccb1
- File name: exe2.exe
- File size: 363,728 bytes
- File description: Kovter malware (follow-up malware retrieved by plugin.js on April 13th)
SHA256 hash: b2dfa063fa605d942822cc84ef90419e26cfa0030444751fc2b87f1456b72e30
- File name: exe2.exe
- File size: 363,922 bytes
- File description: Kovter malware (follow-up malware retrieved by plugin.js on April 14th)
SHA256 hash: ba1327106fa0bf82050cf1a1b9c0c119eb0ded63931af4127e5d541dfa2c6850
- File name: exe3.exe
- File size: 221,974 bytes
- File description: Miuref malware (follow-up malware retrieved by plugin.js on April 13th)
SHA256 hash: 5459be968e2296a759dcafa7107ef06d02331b5291c9f3056077bcf38ce37d9e
- File name: exe3.exe
- File size: 117,561 bytes
- File description: Miuref malware (follow-up malware retrieved by plugin.js on April 14th)
Other URLs associated with this activity:
Examples of fake Microsoft Microsoft Word Online pages:
- posof.bel[.]tr/counter/1.htm
- tramplinonline[.]ru/counter/1.htm
- mattsfotoalbum[.]de/cache/counter/1.htm
- anilstone[.]ir/libraries/joomla/string/wrapper/counter/1.htm
Examples of malware URLs disguised as Microsoft Office plugin:
- posof.bel[.]tr/counter/plugin.exe
- posof.bel[.]tr/counter/plugin.zip
- mattsfotoalbum[.]de/cache/counter/plugin.zip
- tramplinonline[.]ru/counter/plugin.zip
Examples for start of URLs generated by plugin.js:
- alita[.]kz/tmp/installation/language/cs-CZ/counter/
- avtotur.com/libraries/fof/utils/ip/counter/
- circus-stroy.ru/counter/
- boorsemsport[.]be/templates/yoo_aurora/less/uikit/counter/
- eurostandard[.]ro/pics/size1/counter/
- forum-turism.org[.]ro/images/layout/counter/
- glochemindia[.]com/modules/mod_roknavmenu/lib/librokmenu/counter/
- sportbelijning[.]be/libraries/joomla/application/web/counter/
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.