PAN-OS 8.0: Cover Your SaaS By Securing Your Applications
The adoption of software-as-a-service (SaaS) applications in the enterprise continues to rapidly accelerate, given the collaboration and productivity benefits. However, ungoverned use of SaaS creates new risks for data misuse and information leakage that must be addressed. The fact remains that it’s very difficult to gain visibility into and control over SaaS applications with a traditional security implementation composed of layered, “bolted-on” point products.
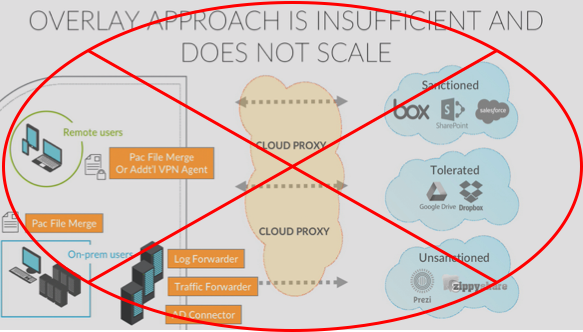
![cover_saas_1]() The Overlay Approach Is Insufficient
The Overlay Approach Is Insufficient
In a bolt-on approach, enterprises keep adding products, one on top of another, just to get insight into the traffic that has been moved to or deployed in SaaS applications in the cloud. Some of those moves include:
- Placing a proxy in the cloud (e.g., forward proxy or reverse proxy)
- Deploying a device on premises, perhaps a log forwarder, to gain some basic, limited visibility from the existing firewall
- Using a traffic forwarder to redirect traffic to the cloud
- Adding an active directory (AD) connector to understand who users are
- Deploying VPN agents or PAC files onto the endpoints
This process is extremely complicated, insufficient in terms of security, and doesn’t scale. If you are an enterprise with several sites, you must repeat this process for each of your individual sites. And even with all components in place, there are still plenty of malicious tools available to criminals that are specifically designed to bypass proxy-based models, such as Tor or UltraSurf.
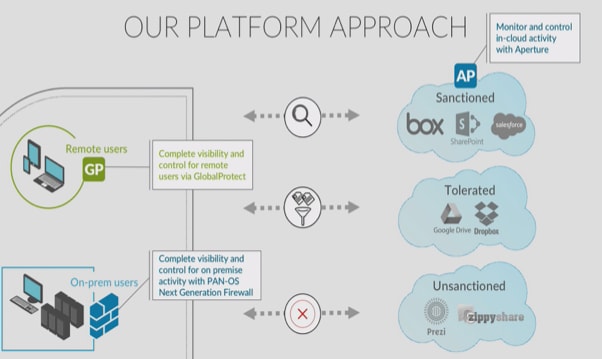
![cover_saas_2]() It’s Time to Get Serious About Securing Your SaaS
It’s Time to Get Serious About Securing Your SaaS
At Palo Alto Networks we’re addressing the SaaS security dilemma from an entirely new perspective – the platform perspective, to provide an integrated, comprehensive approach to SaaS security. Here’s how:
- Our Next-Generation Firewall (NGFW) already provides visibility and control of all applications within the network perimeter. Insights gained from the combination of App-ID, User-ID and Content-ID technologies enables security for content and data going into SaaS applications from the enterprise network.
- GlobalProtect network security for endpoints extends the visibility, control and protection of next-generation network security to the mobile workforce by connecting a user’s device to the closest NGFW, virtualized form factors included, so that full network security can be performed, regardless of physical location. This enables organizations to apply consistent security policy.
- Aperture, our SaaS security service – essentially a SaaS application itself – connects directly to sanctioned SaaS applications via APIs to provide granular visibility and control within the applications to prevent data exposure and threat risks.
- WildFire, our cloud-based threat analysis service, prevents new insertion points for malware and threats by identifying known and unknown malware across the network, the cloud and the endpoints.
Learn more by visiting our resources page, Securely Enabling SaaS Adoption. You’ll find a host of SaaS security–focused materials, ranging from informational videos and in-depth demos to detailed spec sheets and user guides.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.