This post is also available in: 日本語 (Japanese)
In this second part of Unit 42’s Cybercrime Underground blog series, we dive into the cybercrime forum ecosystem and focus on observed cybercriminal roles, as well as prevalent tools and services bought and sold in the underground. The goal of this post is not to provide an exhaustive directory, but rather to provide additional context on the operations and highly prevalent threats observed within this ecosystem.
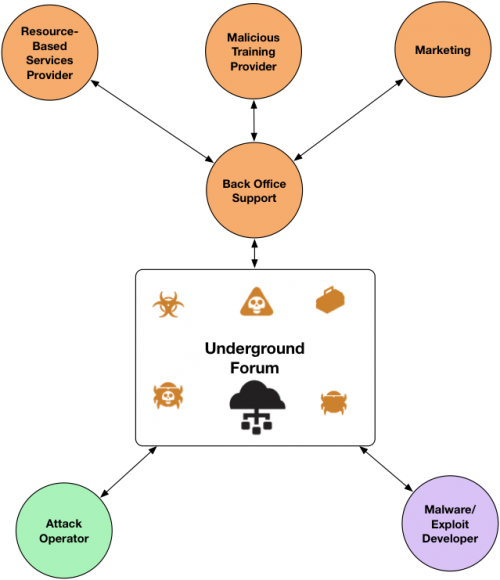
Typical Forum Actor Roles
The cybercrime underground market comprises several important actor roles overall efficient and effective forum operation. The following sections highlight typical key forum roles.
Malware / Exploit Developer
These individuals are the developers of the malicious tools and exploits used to perform cybercriminal activities. Developed tools include Remote Access Trojans / Remote Administration Tools (RATs), Exploit Kits (EKs), Crypters, Keyloggers, and Information Stealers (InfoStealers). Higher-end developers are technically proficient individuals who use their knowledge and skills to create software tools and exploits capable of reliably bypassing common security controls to accomplish attacker objectives.
Though the developers are the brains behind associated products, they don't typically use them to directly target victims. Instead, they sell these offerings in the underground forums for profit. Most developers market their offering with the disclaimer that the product is strictly for educational purposes and should not be used for any illegal activities. This language is typical of malware authors who seek to distance themselves from the likely (and often purpose-built) illegal use of their developed software.
Back Office Support: Marketing
Tools sold in the underground forums are increasingly advertised through attractive, professional-looking marketing layouts. Such advertisement incorporates elements such as features and capabilities of the respective tool or service. The designs and layouts are often created by graphic arts and design specialists who themselves competitively advertise their services on forums. This works out well for the tool developers, as they don't have to spend time on creating marketing materials; instead, developers outsource this work to these specialists. Having an attractive layout for the tools and services sold in the underground has become essential to attract buyers. Similar to a traditional business advertisement / marketing strategy, solid design and branding influence sales numbers.
Back Office Support: Malicious Training Provider
These individuals provide training services, including aspects such as attack techniques, malware infection and spreading methods, and hosting and managing botnet infrastructure. These offerings include well documented, easy to understand, and step-by-step procedures for anyone seeking to learn more about the tips and tricks of successful cybercrime operations.
Back Office Support: Resource-Based Services Provider
This category of malicious actor offers different types of services, such as Bullet Proof Hosting Service (BPHS), Distributed Denial of Service (DDoS), and others. Such offerings are leased at pre-arranged rates, often with guarantees on availability and performance.
Attack Operator: The Cybercriminal
These individuals typically buy the tools, exploits, and services advertised in underground forums. They use these purchases to compromise and steal data from targeted victims and organizations. The technical skillset and expertise of this group can vary greatly, ranging from actors who are experienced cybercriminals to those who are just starting their cybercrime careers.
Figure 1: Typical actor roles found in cybercrime underground forums.
Tools
Some of the most common tools which are being sold in the underground forums are RATs, Crypters, and Infostealers. Some of these tools are sold as malware creation kits, allowing for flexible incorporation of features into discrete builds for deployment, including both security control evasion and operational capabilities. The following sections describe some of the more prominent tools observed in the cybercrime ecosystem.
RATs
Remote Administration Tools, or alternatively Remote Access Trojans, enable a malicious actor to assume control over a victim’s computer. Modern-day RATs are a reliable and versatile class of tool used by actors across a number of motivations.
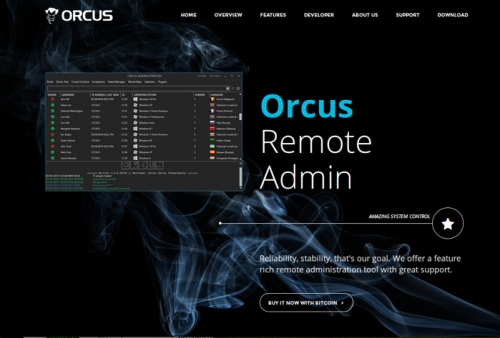
LuminosityLink
At just $40 USD, LuminosityLink is a full featured RAT with keylogging capability that injects its code into almost every running process on a target computer. This malware can also download additional payloads, increasing its flexibility in use by attack operators. Unit 42 previously reported on configuration extraction for this family of malware in July 2016. LuminosityLink’s author openly advertises and sells this malware through a commercial website on the indexed web, under the guise of an administrative utility; however, it has gained in popularity across a number of malicious actors.
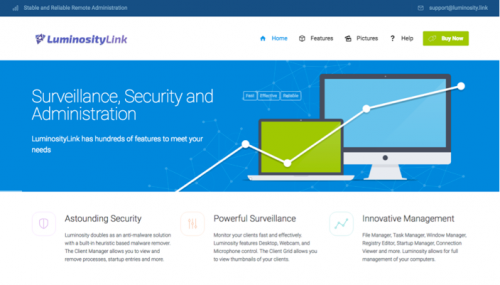
Figure 2: LuminosityLink website
Ozone
Ozone RAT is a commercially-available tool, popular for its feature-rich capabilities, ease-of-use, and low cost. It is available from a website on the indexed web at $20 USD for a “Standard Package” and $50 USD for a “Platinum Package”.

Figure 3: Ozone remote control program website
Netwire
Netwire is commercially available and used by a wide range of malicious actors to remotely take control of a compromised victim system. Its website offers a trial version for free, as well as support / update versions: Lite ($50 USD semi-annually), Basic ($90 USD annually), and Pro ($160 USD biennially). Unit 42 first highlighted this threat’s use by a malicious actor in our 419 Evolution Report.
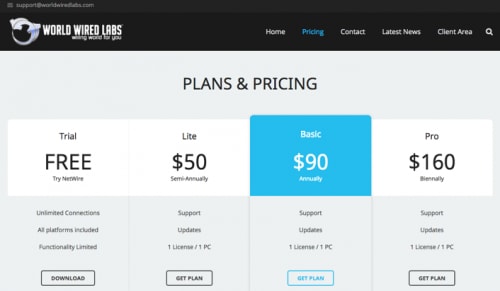
Figure 4: Netwire plans and pricing
Orcus
Orcus is a new RAT that has been on the market since April 2016. This RAT costs $40 USD, comparably priced in the range of many other popular RATs. However, this RAT provides some distinguishing features, such as plugin support and development with well documented guides. This allows buyers with knowledge of at least one supported programming language (e.g., Visual Basic .NET, Visual C# or C++), to extend Orcus features. We anticipate a number of threat actors will integrate this RAT into their toolset, given its rich feature set and flexibility. Unit 42 recently reported on the capabilities and the impact observed from this malware family.
Figure 5: Orcus website
InfoStealers
InfoStealers are a sub-class of surveillance malware that capture elements such as keystrokes, screen state, and files or data stores of interest from a victim’s computer to then send to an attacker. This class of malware offers both immediate benefits for an attack and can also serve as input for integrated, progressive adversary operations.
Keybase
Keybase is a family of keylogger malware that Unit 42 has been tracking since June 2015, at which time it was sold for $50 USD directly from the author’s commercial website. We also followed up with a blog on its increased malicious actor usage in February 2016, despite its initial author shutting down the corresponding commercial website and discontinuing development. As it turned out, the source code for this malware’s builder was leaked around that time, making this malware family accessible and customizable to a number of malicious actors who possess or can afford requisite technical proficiency.
Predator Pain / HawkEye
Both Predator Pain and its derivative, HawkEye, are primarily considered keyloggers, but they also include additional features, such as web browser and e-mail client credential dumping, display capture, and captured information exfiltration. Both are usually acquired through underground forums, although HawkEye was formerly offered for some time through a commercial website on the indexed web. Unit 42 previously described active use of this tool set by a cybercrime actor in 2014, as well as observed trends in October 2015.
iSpy
This off-the-shelf keylogger is marketed to unsophisticated actors, with both a low technical proficiency required of its user and price point. Marketed as a way to monitor family members and employees, this infostealer is fully functional “out-of-box” for approximately $20 USD.
Crypters
Crypters play an important role in the overall malware creation cycle. They enable cybercriminals to create malware that can bypass legacy security solutions without raising any alarms. As discussed in a prior Unit 42 blog, crypters are software that use a combination of obfuscation, encryption, and code manipulation to make malware FUD (Fully Undetectable). After malware binaries are created, they can then be passed through a crypter to increase their likelihood of successfully bypassing security measures protecting their target.
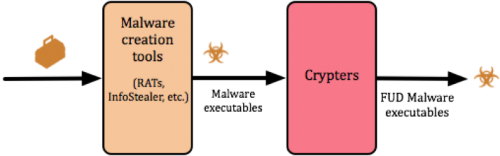
Figure 6: Applying a crypter to malware
Kazy Crypter
Kazy Crypter has been sold in the underground market since 2014, with version 5 currently available. The cost of this crypter can range from $13 USD for 30 days to $35 USD for a 180-day package. This tool provides various evasion techniques and advertises that it is fully compatible and tested with most well-known RATs, such as LuminosityLink, NanoCore, and many others.

Figure 7: Kazy Crypter features
Ghost Crypter
Another widely adopted crypter on the market is Ghost Crypter, which is distributed without any dependencies. This is uncommon with such tools; for comparison, Kazy Crypter has a dependency on .NET 2.0, without which the files will fail to execute. As shown in the image below, this crypter is available through three package offerings: 1 month at $12 USD, 3 months at $25 USD, and a lifetime access for $50 USD, respectively.

Figure 8: Ghost Crypter packages
Services
The cyber underground marketplace not only provides buying and selling of tools, but also services that range across malware spreading, hacking / exploitation, DDoS/ Stress testing, marketing / graphics design, hosting, currency exchange, and much more. We will discuss some of the prevalent services advertised explicitly or implicitly through forums, which are commonly used by cybercriminals to achieve their malicious objectives.
Malware Spreading Services
Malware Spreading services provide step-by-step tutorials to conduct malicious campaigns. They typically provide guides and procedures to conduct campaigns to exploit, infect computer systems with malware, exfiltrate information using various tools, techniques and procedures.
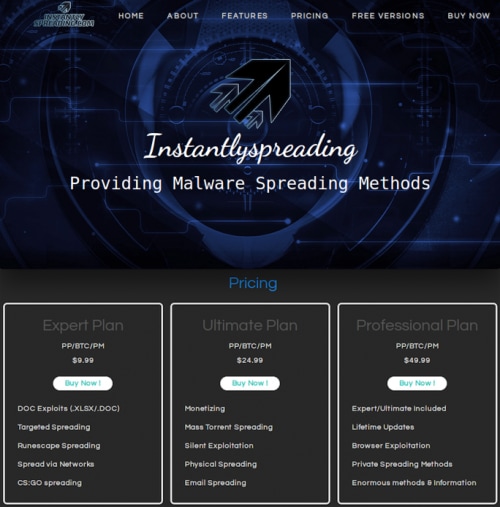
Instantlyspreading
“Instantlyspreading” is one such malware spreading services, which is being sold in the underground market with three different pricing plans as shown in Figure 9 below.
Figure 9: Instantlyspreading service plans
Bullet Proof Hosting Service Providers
Bullet Proof Hosting Service (BPHS) service providers enable cyber criminals to host malicious contents without the risk of being taken down. There are several BPHS providers that offer services under the banner of legitimate business services. However, there are also some BPHS providers that openly advertise their services to malicious actors, highlighting their lack of enforcement on most types of content hosted on their servers and dedicated packages for hosting different kinds of malicious hosting services.
One example of this latter class of BPHS provider is ‘hostmy.su’, a popular choice amongst malicious actors that uses a custom made Fast Flux system to ensure high availability. The cost of their services can start from $39.99 USD to $700 USD per month for dedicated pre-configured packages.
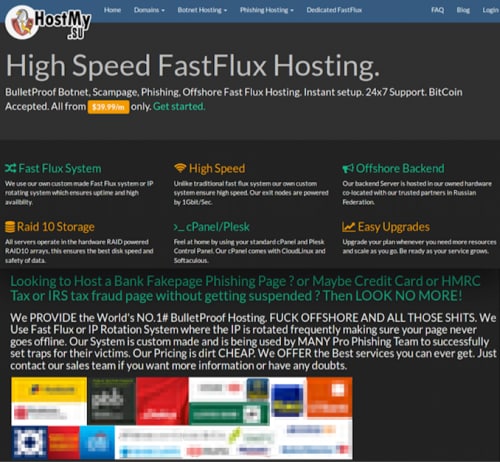
Figure 10: ‘Host.my’ website selling BPHS
DDoS Services
Distributed Denial of Service (DDoS), also known as Booter or Stress Testing services, are online resources primarily used to test the resilience of websites. Malicious actors use these services to bring down websites and individual online Internet users. Typically, these services provide Layer - 4 (transport) and Layer -7 (application) volumetric attacks that consume the resources of the target and make it unresponsive to legitimate requests, ultimately bringing the service down. Though these DDoS services may not impact large and / or well-funded enterprises that employ DDoS prevention technologies, they can be very effective when used against medium size enterprises. These services usually cost between $10 USD to $200 USD per month, depending on the level of package bought.

Figure 11: Sample advertisement for a DDoS service
Marketing Services
Marketing services such as graphic design, brand management, and advertisements play a part in communicating the professionalism and longevity of associated cybercrime underground offerings. These efforts strive to recreate a community perception and “feel” for products and services that rivals the planning and quality of those achieved by conventional businesses for corresponding real world public consumers.
Figure 12: Sample advertisement for malware marketing
Payment Services
Methods for processing underground marketplace payments vary based on factors such as the plausible legality of offerings and the segment of the cybercrime underground through which that offering is available (e.g., Indexed Web versus Dark Web).
BitCoin
BitCoin (BTC) is the premier cryptocurrency of the day. BTC is used for lawful financial transactions every day; however, it is also preferred by most malicious actors due to its built-in model of anonymity. This reduces the likelihood of payments being tracked to or from associated parties. This anonymity extends to funds pilfered through digital heists of BitCoin wallets either using BTC-targeting malware or direct actor activity, which can further conflate the exercise of determining at which point transactions are applied towards illegal endeavors.
Conventional Payment Cards
Some tools and services may be purchased using conventional payment cards and methods, such as commercial bank and credit card company accounts, or generally legitimate intermediary broker services such as those available through PayPal. This happens at at least in part to support the argument that there are legal or educational uses for those offerings, and therefore associated purchases should not be perceived as illegal. On the other hand, cybercriminals of sufficient means can just as easily use stolen payment card information for such purchases, whether stolen directly or obtained through bundles of such information available on carder forums.
Core Takeaways: Underground Forums
Tools and services used by malicious actors are constantly developed and sold in the cybercrime underground (some of which have been discussed in this post). These ever-evolving offerings pose a significant threat to organizations and individuals alike. The ease of availability, simplicity of usage, and low cost of these tools and services allow cybercrime to grow and thrive in this digital world Awareness and deeper understanding of these tools, services, and how individuals within the cybercrime underground ecosystem collaborate and operate to enable financial gains are essential inputs into defending both organizations and individuals and preventing threats.
Coming Up…
The next installment in this blog series will focus on the impacts observed from some of the type of tools discussed so far.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.