This post is also available in: 日本語 (Japanese)
This is the second part of a two-part blog post for understanding Angler exploit kit (EK). The first part covered EKs in general. This blog focuses on the Angler EK.
Angler is currently one of the most advanced, effective, and popular exploit kits in the cyber criminal market. It generally uses the most recent exploits based on the latest vulnerabilities. Like most leading EKs, the authors behind Angler use Software as a Service (SaaS) as their business model, and Angler can be rented in the cyber underground for a few thousand dollars a month.
History
Angler EK was discovered in 2013, and it began appearing more frequently later that year. Angler grew in popularity sometime after Russian authorities arrested malware kingpin "Paunch", the alleged creator and distributor of Blackhole EK. As Blackhole EK disappeared, other EKs like Angler began filling the void.
However, Angler is not the criminal's name for this EK. Security researchers used the term "Angler" because of a picture of an Anglerfish in advertisements from late 2013.
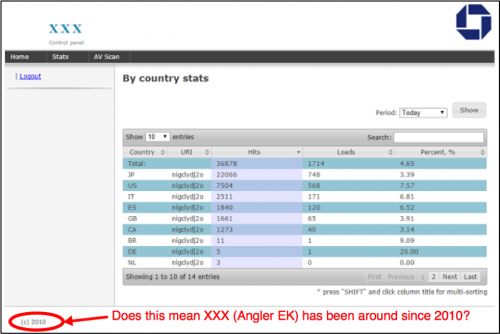
Based on control panels found on Angler EK servers in 2015, the author's name for Angler is "XXX". Based on the copyright date in the control panel, Angler EK might have been around in some form as early as 2010.
Figure 1: Control panel for Angler EK with "XXX" from the Malware Don't Need Coffee Blog.
Growth in Angler EK Traffic
Security researchers saw an increase Angler EK-related traffic during 2014. After a short lull, Angler EK has been relatively prominent since March 2015. Today, Angler accounts for the majority of EK traffic we find.
Angler EK Exploits
In 2015, Angler EK began focusing on exploits targeting three applications: Flash player, Internet Explorer, and Silverlight. Angler is often one of the first EKs to use new exploits targeting these applications.
For example, in June 2015 a previously unknown Flash vulnerability (later identified as CVE-2015-5119) was part of some 400 gigabytes of data dumped on the Internet as part of the infamous Hacking Team breach. A Flash exploit based on CVE-2015-5119 was integrated into Angler EK hours after the data dump was publicly available. It was a zero-day exploit at least 24 hours in the wild before Adobe issued a patch for it.
By August 2015, Angler EK implemented an exploit for Internet Explorer (IE) vulnerability CVE-2015-2419 that Microsoft had patched the previous month.
In February 2016, exploits for Silverlight based on CVE-2016-0034 found their way into Angler EK a little more than a month after Microsoft issued a patch for the vulnerability.
Angler EK Payloads
Different campaigns use Angler EK to distribute different types of malware.
The most prominent type of payload from campaigns using Angler EK appears to be ransomware. In 2015, the ransomware was most often CryptoWall. By the start of 2016, it was primarily TeslaCrypt. In mid-April 2016, the usual ransomware changed from TeslaCrypt to CryptXXX ransomware. We have seen CryptXXX primarily from actors behind the pseudo-Darkleech campaign.
But ransomware is not the only payload sent by Angler EK. EITest is another campaign that uses Angler EK to distribute other types of malware. In addition to ransomware, EITest Angler EK includes banking Trojans like Tinba, information stealers like Vawtrak, and other malware families including Andromeda, Ursnif, or Zeus.
Fileless Infection to Avoid Detection
In August 2014, Angler EK introduced a "fileless" infection technique to avoid detection by executing the payload from memory instead of storing it to disk. This technique is most often associated with Bedep payloads. Such fileless infections leave no artifacts from Bedep on the infected system's disk. Fortunately, any post-infection activity usually leaves clues, since follow-up malware must be stored somewhere on the system in order to stay persistent and survive a reboot.
Angler EK and CryptXXX
In April 2016, the pseudo-Darkleech campaign started using Angler EK to send Bedep, and Bedep followed up with CryptXXX ransomware. Bedep also downloads click-fraud malware that generates web traffic behind-the-scenes (click-fraud is a fraudulent method used by criminal groups to increase advertising revenue). This click-fraud traffic is invisible to the end user, but it is noticeable when monitoring network traffic generated by the infected host.
Proofpoint and others reported details of CryptXXX and Bedep when this particular combination first appeared. Sometime during the second week of May 2016, the pseudo-Darkleech campaign stopped using Bedep and began sending CryptXXX only.
Figure 2: An example of Angler EK sending Bedep then Bedep sending CryptXXX on 2016-04-22.
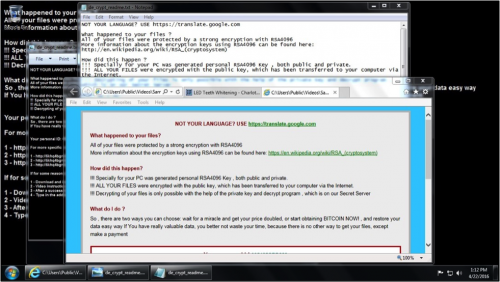
Figure 3: An infected Windows desktop after Angler EK sent CryptXXX.
Conclusion
Angler EK will no doubt continue to evolve. We expect the EK to continue implementing improvements to avoid detection. As a payload of Angler EK, Bedep malware has recently changed and is much more capable of detecting virtual environments used by security researchers. CryptXXX ransomware is a growing menace that also has information stealing capabilities, and it appears to be moving to other campaigns that formerly spread TeslaCrypt ransomware.
How can people protect themselves against Angler EK? As stated in part 1 of this blog post, use a layered defense. First, make sure your operating system and applications are patched and up-to-date. Like any other EK, Angler takes advantage of outdated browser-based applications to infect vulnerable Windows hosts.
Network monitoring and endpoint protection are additional components of a layered defense. Palo Alto Networks Next-Generation Security Platform can help security teams monitor their network to detect the constantly changing indicators of Angler EK. Endpoint solutions like Palo Alto Networks Traps can help protect an organization’s assets against malicious executables, data files or network-based exploits before any malicious activity can successfully run.
Domains, IP addresses, and other indicators associated with Angler EK and its associated payloads are constantly changing. We continue to investigate this activity for applicable indicators to inform the community and further enhance our threat prevention platform.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.