The Bucbi ransomware family, which dates back to early 2014, has received a significant update. In a recently observed attack, we also noted new tactics used to infect systems. The malware has historically been delivered via an HTTP download, most likely via an exploit kit or phishing email. However, in recent weeks, Palo Alto Networks researchers have observed attackers brute-forcing RDP accounts on Internet-facing Windows servers to deliver their malware. Additionally, the malware itself has been modified to no longer require an Internet connection.
Recent ransom notes left on infected systems identify the malware as belonging to the “Ukrainian Right Sector,” a far-right Ukrainian nationalist political party with paramilitary operations that opposes Russia but operate outside of the Ukrainian government’s authority. However, there are a number of Russian identifiers in the recent attacks. Consequently, it is unclear if the claims of responsibility by the “Ukrainian Right Sector” are accurate, and if so, what the reason behind and significance of the Russian identifiers.
Infiltration
Unlike many other ransomware families, this particular variant of Bucbi was delivered via a RDP brute force attack. The following five IP addresses were observed attacking the victim machine starting in late March 2016:
- 31.184.197.69
- 31.44.191.251
- 79.117.151.236
- 46.161.40.11
- 191.101.31.126
Many common usernames were used in attempted logins in this brute force attack, including a number of point of sale (PoS) specific usernames. It is likely that this attack originally began with the attackers seeking out PoS devices, and after a successful compromise, changed their tactics once they discovered that the compromised device did not process financial transactions. A truncated list of the usernames used in attempted logins can be found below.
- Administrator
- Aloha
- Admin
- BPOS
- FuturePos
- HelpAssistant
- KahalaPOS
- Oracle
- POS
- SALES
- SERVER
- Sqladmin
- Staff
- Администратор [‘Administrator’ in Russian]
Once the attackers successfully compromised this specific machine, they dropped an executable file that contains the following PDB string:
C:\inetpub\restartprm\Present\Перед запуском софта\dotNetFx45_Full_setup.exe
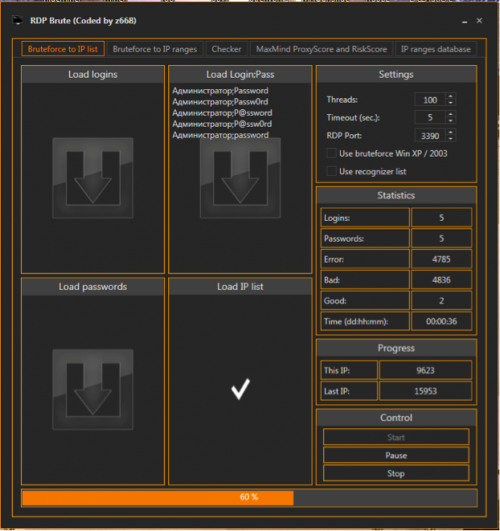
The Russian string above roughly translates to ‘Before running software’. Researching the filename above leads us to a number of Russian language forums that are discussing an RDP brute force utility named ‘RDP Brute (Coded by z668)’. While not confirmed, there is a possibility that this tool was used to gain access to the victim machine originally. A screenshot of this utility can be found below:
Figure 1 RDP brute force utility
Malware Analysis
The following sample was discovered on an attempted breach in early April 2016:
MD5: 410E395600C291C59D8C9B93FA82A7F3
SHA1: 2E385E8B8CEB01C9E638F8A95889B571D31AEF41
SHA256: 26F2BF1FC3EE321D48DCE649FAE9951220F0F640C69D5433850B469115C144FE
Timestamp: 2016-04-02 16:40:13 UTC
This particular sample is configured to take one of the following two command-line (CLI) arguments. Should no argument be provided, it will attempt to start a service it expects to exist, named 'FileService'.
- /install
- /uninstall
When provided a CLI argument of '/install', the malware will proceed to create a service with the following properties.
Service Name: FileService
Display Name: File Service
Startup: Auto
Path: [path of malware]
After the service has been successfully created, the malware outputs a printf statement of 'Installation OK'.
When give a CLI argument of '/uninstall', the malware will remove the previously created service and output a printf statement of 'Uninstallation OK'.
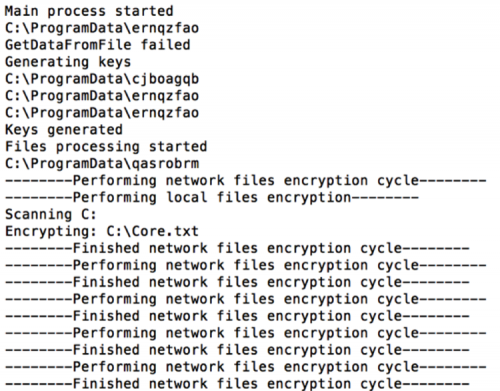
When the service is run, the malware will generate a number of debugging statements that are written to a randomly named file with an extension of '.log' in the %ALLUSERSPROFILE% directory. An example of this log file is below.
Figure 2 Log file written by malware
The malware begins by seeking out a file in the victim's %ALLUSERSPROFILE% directory. The filename is generated by a unique algorithm that uses the victim's volume serial number in conjunction with two 4-byte seeds provided to generate a unique 8-byte sequence. This sequence then has a search/replace performed on it in order to convert it into an alphabetic string. This function is represented below.
The algorithm above makes use of the GOST block cipher to generate a unique filename. GOST is fairly obscure, as it was developed in the 1970s by the Soviet government. It was declassified to the public in 1994. This particular technique for generating a unique filename looks to be specific to Bucbi, as no other malware families have been discovered using it.
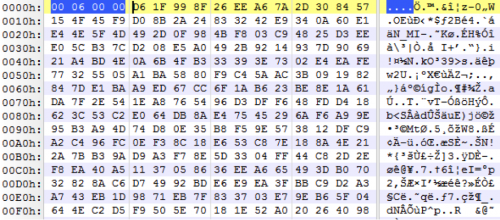
The algorithm is used to determine if a key file is present on the victim. If this particular file is not present, the malware proceeds to generate one. Two files are created—one 580 bytes in size, and one 1060 bytes in size. Both files begin with a DWORD of 0x60000, as shown in the screenshot below.
Figure 3 Example key file written by malware
The cryptography used by Bucbi is still being researched by Palo Alto Networks. After the key files are generated, the malware will spawn a new thread that is responsible for encrypting network resources.
A call to WNetOpenEnum is made to enumerate all network disk resources available. Should a network disk be identified, the encryption routine will be run against this resource. The malware will ignore the following directories, but otherwise will encrypt every file it encounters.
- C:\WINDOWS
- C:\Windows
- C:\Program Files
- C:\Program Files (x86)
No file type denylisting results in this particular malware being very inefficient, often taking several minutes before encryption is complete.
Files are overwritten, leaving them with the same filename that was originally present. Unlike other more popular ransomware families, Bucbi does not use a specific file extension for files that are encrypted.
It’s also important to note that the key files that were originally created are not removed. Additionally, the malware includes a decryption routine, which, while never called by the malware, exists and can be used with a simple binary modification to the sample. This would allow victims to recover their files without resorting to paying the ransom.
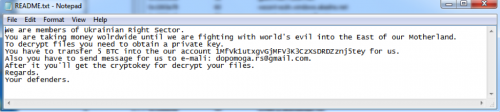
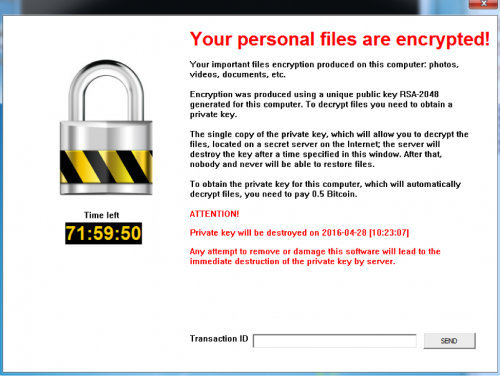
Once encryption completes, a README.txt file is placed on the victim's desktop. This file contains the following information:
Figure 4 Ransom message dropped by malware
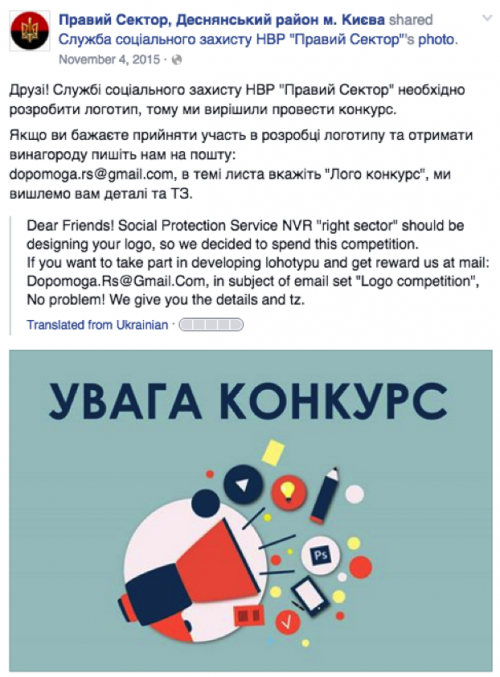
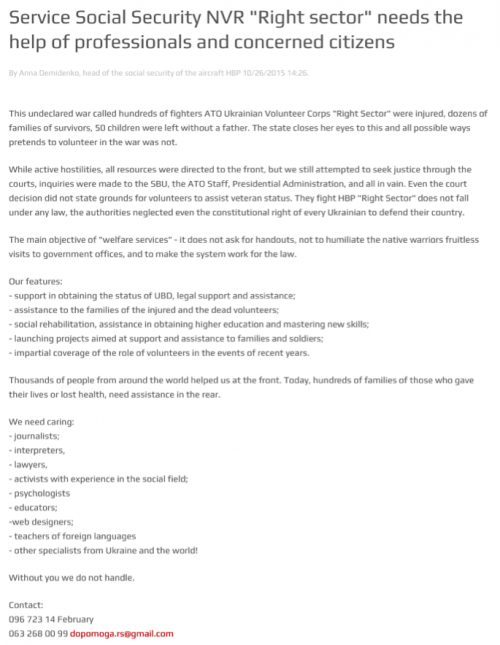
The BitCoin address mentioned in the above screenshot has a single payment of 0.00896 BTC at the time of writing. This payment, being so low in value, was likely a test transaction used. The email address of ‘dopomoga.rs@gmail.com’ has ties with the Ukrainian Right Sector in a number of external publications, as noted in the following examples.
Figure 5 Facebook post from November 4, 2015
Figure 6 Translated post from sectorpravdy.com
However, as mentioned earlier, there are a number of indications that the actor is of Russian origin or speaks the Russian language, such as the existence of Russian PE resources within the malware executable, as well as the Russian-related files discovered in the attack.
Similarities and Differences With Older Versions of Bucbi
As mentioned earlier, the Bucbi malware family is quite old, dating back to January 2014. Very little public information about Bucbi is available, other than an entry by Microsoft in mid-2014.
When comparing the newly discovered Ukrainian variant of Bucbi to an older sample, we see a number of similarities. Certainly one of the most noticeable similarities comes in the form of a debug string present in both samples:
Ukrainian Variant: C:\Users\admin\Desktop\FileService\FileCrypt\Release\payload.pdb
Older Bucbi Sample: C:\FileCrypt\Release\FileCrypt.pdb
The original filename of ‘FileCrypt’ is present in all observed Bucbi samples. Another glaring similarity comes in the form of how filenames are generated. All samples observed use the same GOST block cipher function mentioned in the malware analysis section. This function has only been observed in Bucbi samples to date.
Additionally, the key files used across samples is consistent, in both size and the leading 0x60000 DWORD value. Coding style between samples is consistent as well between all observed instances of Bucbi.
While these similarities are present, a number of changes have been observed as well. Most notably is the service installation method, as well as the command-line arguments of ‘/install’ and ‘/uninstall’. While the older Bucbi sample also took a command-line argument, it instead searched for the existence of the ‘-e’ parameter.
The implementation of a network-resource encrypt function looks to be new in the Ukrainian variant of Bucbi. Conversely, the use of an HTTP command and control (C2) channel looks to have been removed from this variant. Previous versions of Bucbi, seen as recently as June 2015, made use of a remote server, where victim information and the generated key information was uploaded.
Finally, we also observe a change in ransom notes. The following ransom page is presented to the victim in this older version of Bucbi:
Figure 7 Original Bucbi ransom page
Conclusion
Overall, this proved to be a curious attack, as the attackers originally gained access using techniques common to those of attacks seen against point of sale devices. It appears that once access was acquired, the attackers shifted gears to deploy a new variant of the fairly old Bucbi ransomware family. This particular variant purports to belong to the ‘Ukrainian Right Sector’, a far-right Ukrainian national political party. If true, this would indicate that this particular national political party has entered the ransomware space, potentially to fund their cause. However, various Russian-related strings and references leave doubt as to who exactly is behind this attack. Attribution of this particular attack is difficult as there simply isn’t enough evidence to conclusively determine who is behind it. Various conflicting evidence make it impossible to say for sure. However, what is clear is that attackers are shifting tactics in how ransomware is deployed, and ensuring their malware is constantly being updated to deter defenders.
Palo Alto Networks customers are protected against this threat in the following ways:
- WildFire correctly identifies all Bucbi samples as malicious
- A Bucbi AutoFocus tag has been created in order to track this malware family has been created in order to track this malware family
- All domains/IPs used in this attack have been flagged as malicious.
Indicators of Compromise
SHA256 Hashes – Ukrainian Variant
26f2bf1fc3ee321d48dce649fae9951220f0f640c69d5433850b469115c144fe
4c698f5a005a74570a10a69a82317b0c87207934fe82907ee7df3348096cd66c
SHA256 Hashes – Original Bucbi
ad16c5246675b807cd04c33f5186f26c1c677e7b2f3baea3305b23e7cac34f8e
be63b6a01e57a7a409647bdf221a37a0be0d470d488136228a4c1d1defbd05f4
98e901f362641ae1fc6527215f496c9fd5de2d7f69b136ac610e453469831d07
2f8597a18c24d9c7ee4442f607b518c065bfef376c554ea80b303875bb0f5c4f
713413ee1a008b91a6afb29c52d2beda829778b8072c5ba5171bb50277104ebc
8577216183fc19767788e3d078eaeb754d18141c80c2554f9c3c359cc470c4f6
feb6eccc9d254fb0e1c818be50ec183a472ed064d4071f380ac131c262da0689
0ed72a28ba5bac7f44f9e4519db5f8c8d94076d85a929c2004da1cba99559610
ea7896c06595a261b140f1ce192230e0fc0bdb9213023db0a5d1b07eb91f7af3
27ba82a72339fef306ef6ce83c055c35caa7bf7116eea0edad22966d297661f3
70d59a3f1f508668b1ae214022a140fb96f90c221a192443b87a1fbe621cee0b
feecc0baccecabeddc8f0e07b3a7aa54d7f13d60e232b7a538b10cd773b4c5e5
766b3a58b5ff86b1070c186b72854c69fff6fc11ce384d70c71db66f6c18a8c8
a65293abd10e7c4a306ddfae94c67df2db411c4a29ca71a1ca8169ee640a8ed3
62f199dedfffef4eb71c33bdf22f4a9b3276f8a831999788059163fae43db48e
8988f592efb88b4998b54c9736898339811bda3578b27e0a4a03ed9a4c5ca363
60fb4c67f4fade5b00d1f57810ec379df3c39b546ead0865296a077e6a8b2f42
ce122be2e52159c3e441c43b81a334b49b7763cf6a2265768d8e2df45478fc6a
30645cdf85546f51862c7dc4750016f872683bc060cc34e4b462e01445a8abfd
9b1b25ab5a6e5291a509c4ad94ab16c25925feaf9e6e8b217494596f76888202
558d32c77167d08ab8594c5df99dd162ae975d8ceb1d169108fe0d70ac8df11a
6e279ea746bc4692ff32acb697da0147ec056700fc095f8ff248317548bcbdcb
56da464cd45f17bacf52b6497396e2c801625bd4068790d9d9515a087584f630
14ff3948a11b7469882bda4e8fcf89600aaaf84d5d5b4bfcea1896acc4ed2ca5
63492d05b5bd0fd132dbb92142f6c8911325899c7a1cd9a462edf720ce27d47c
697266cac58ba555fb3d7dd6e0afd08ecfc57702f3e3a9df96e9e4eef8b722d6
b561b91cce444e9dc768bd93e0404e67f79900598ef03f175a10887c7b94c30c
06fee4e154ad90945be70aae671aeefd103fa0947d957fdc973848221ada635c
b497c79c027bab2b9a30c613b2c603296bcb29d63c8f30c27864c860955b3ebd
a1dc73eaaaa11ef3585bf389fcc3301c20c0636a144778d3ffb657110d911d1b
d65593e94ef433a2597cf01591e96067180e548cd418327476931c642e01bdff
4ec6ee80323c2365dfd4cfeba9a64f043df026a98b026ecb1e757c9df532f064
cc7c24dd062e8538984a9d640600b91ff6c3a0404a5caf4f174c513c7f16fba4
5d753520b6c97bace23dbbece93ecd9eb9ac3cea1d8c9b4ccf6dfca43dc47556
f51719dfeac4f52a90d52188c3b3e9145d77f612da784510c968564aa0d46e9e
907d245b8854a8277379fb59d65102c2fd440c0bf850939e2a775a3bebb4cb1d
0957912344ff93cba65088c4aed2bd2631e8a5788604520955104e05dcfb4b0c
7cc35bbd4327a4212069eab5747944c5e8dedb82f02f695b0248d026a733f0c6
56485d996b50610b3c0ab86d7136bde215401c2f30154e818b4b18d3a4457eea
11cc17e5e06f7d5e7c52979b5e7b75ea083e46a59e73ea245872e72084f44099
dfb355d874db6f2d141c2789a041ccfa91775508fae2fedd86c48f0089abe00a
15608834007b61eb4426bf034e8923733100fccf872ffebe2e05aea3d9f63fef
26f2bf1fc3ee321d48dce649fae9951220f0f640c69d5433850b469115c144fe
6edf7c043348efe02d94c97a4d06ec735fb90a77ea290509e03991edadb24716
4c5a0fd976f04c63faa32e1a74edd59c5c39ce0e143e69d464f95872b8357e8e
59e06b077b8ac0472cb95401bf5d99301e0e807ed74d698a3953bc96c0eb568e
Command and Control Servers – Original Bucbi
bbb.bth.in[.]ua
shalunishka12[.]org
ceckiforeftukreksyxomoa[.]org
87.249.215[.]196
chultolsylrytseewooketh[.]biz
Attacker IP Addresses
31.184.197.69
31.44.191.251
79.117.151.236
46.161.40.11
191.101.31.126











 Get updates from Unit 42
Get updates from Unit 42