Healthcare Organizations: How to Get Ahead of Unapproved Cloud-Based File-Sharing Tools
Cloud-based file-sharing tools such as Box, Dropbox, SugarSync and Google Drive can cause major security issues for healthcare organizations. And as a former security lead for a hospital, I found that, even if you have an approved cloud file-sharing website, unless you block access to non-approved file-sharing sites, medical practitioners will use whatever they personally prefer to share protected health information (PHI) with colleagues. Your organization may be deploying Box for internal hospital use, for example, but some doctors will still prefer to use Dropbox to store and share PHI – it’s not enough to deploy one approved tool and then hope for the best.
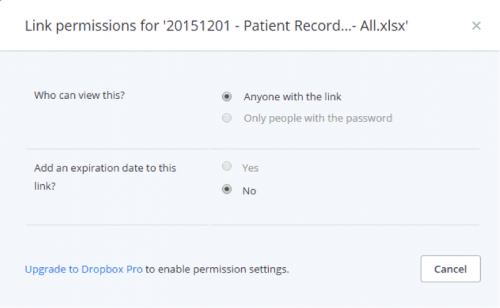
Once you upload PHI data to a popular cloud file-sharing sites, it’s very easy to (mistakenly) configure it to be accessible to everyone on the Internet. As you can see in this screenshot of the free version of Dropbox, users do not have the ability to restrict access to specific users. The only option for controlling view access to their file is to select “Anyone with the link” as shown below. This means that if the link is posted to a Reddit conversation or another public forum, anyone would be able to download the files.
Palo Alto Networks is often asked to perform free proof-of-concept exercises at hospitals and other healthcare organizations, and I have found that it is quite common to find web access is enabled to unapproved cloud file-sharing sites.
When I led the effort to disable access to cloud file-sharing sites in my former role, I knew that I couldn’t simply block all access without a careful plan. If I had done so, I would have been inundated with tickets from angry doctors wondering what was going on. The reality is that there are likely to be business processes that impact patient care that rely on access to these sites. For this reason I recommend the following high-level plan to decommission access to unapproved cloud file-sharing sites while making sure that clinical processes are not impacted:
- Confirm CISO/CIO support of your effort to block cloud file-sharing sites.
- Verify that you have approved alternatives to commonly used, but insecure cloud file-sharing sites. Users will need help to migrate their processes to the approved solution.
- Determine the users who are accessing cloud file-sharing sites (if you have the capability).
- Email users a warning that access to cloud file-sharing sites will be blocked on such and such a date.
- Instruct users to open a ticket with the IT Security team to understand approved file-sharing alternatives.
- Document a process for approving exceptions, and ensure that exceptions are revisited at least every six months. Require CISO approval for exceptions.
Healthcare organizations can safely enable access to sanctioned cloud file-sharing sites with careful planning and the right security tools, but any such website that is not explicitly approved by the organization should be blocked to avoid HIPAA-reportable incidents – as soon as possible.
Learn more about Palo Alto Networks solutions for sanctioned SaaS applications and next generation security in healthcare organizations.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.