Note: This post was updated on November 18, 2015 to reflect new information about the initial discovery of the injected code.
On November 3, 2015, ZScaler reported that a Chinese government website hosting the Chuxiong Archives, www.cxda[.]gov.cn, had been compromised and contained injected code leading to the Angler Exploit Kit. The compromise was apparently remediated within 24 hours of discovery, but is once again exhibiting signs of infection.
After ZScaler revealed the compromise, we began continuously scanning the website, as well as other popular websites and potentially related suspicious targets. We discovered that the Angler Exploit kit on the website had the ability to be placed in an “Active’ or “Dormant” state. Many other websites were infected with this exploit kit and contained the same functionality.
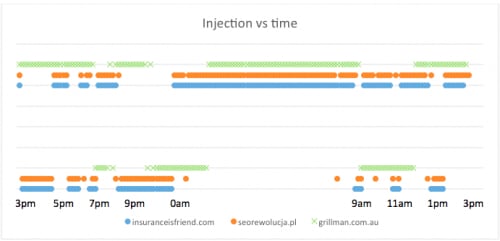
For this article, we chose a few of the additionally discovered compromised sites found by our malicious web content detection system and continued to scan them in high frequency. The following diagram shows the vulnerability status of three of these sites over the duration of a day. The markings of the top portion indicate that the site’s malicious code was active during that time slot while the markings on the bottom portion indicate the site was benign, or dormant, during that time slot.
Figure 1
In what appears to be a technique to evade detection or analysis, the injected malicious code has the ability to hides itself when the user-agent or IP address of the request does not meet specific criteria. Attempts to launch requests from different combinations of IP addresses and user agent strings consistently produced different behaviors (benign vs malicious) depending on what was sent.
During our continuous monitoring for a 24-hour period from November 11, 2015 to November 12, 2015, eight days after the initial disclover, the Chuxiong Archives website consistently presented malicious content injected by an attacker depending on the source IP and user agent. We believe that if a user were to visit the compromised website a second time following the initial exposure to the malicious code, the site would recognize the source IP and user-agent and simply remain dormant, not exhibiting any malicious behavior. Because of this anti-analysis/evasion technique, it may easily cause the belief that a website no longer poses a threat, when it remains infected.
At the time of this report, using our malicious web content scanning system, we have already discovered more than four thousands additional, similarly compromised websites globally exhibiting the same ability of being able to be dormant or active depending on source IP and user agent. Investigations regarding this campaign on a larger scale are ongoing and a second report detailing the similarly compromised websites will be published in the near future.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.