Less than a week after the publication of a thorough report by the Cyber Threat Alliance on the CryptoWall version 3 malware family, it appears that the actors behind the malware have updated the underlying code.
Beginning on October 30, 2015, Palo Alto Networks began seeing instances of this new version of CryptoWall, which some researchers have begun calling version 4. This new version of CryptoWall includes multiple updates, such as a more streamlined network communication channel, modified ransom message, and the encryption of filenames. These changes not only make it more difficult for the victim to identify what files have been encrypted, but also may thwart security protections currently in place for the CryptoWall threat.
CryptoWall is a type of malware known as ransomware, which encrypts a victim’s files and subsequently demands payment in exchange for the decryption key. The ransom payment is typically collected using a form of crypto-currency, such as Bitcoin. Ransomware has been responsible for many millions of dollars in damages, and CryptoWall is one of the most lucrative ransomware families in use today.
CryptoWall Infections
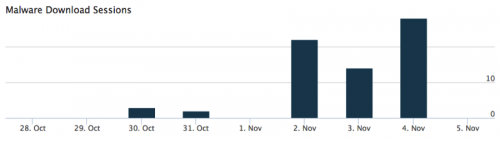
To date, Palo Alto Networks has identified 10 unique instances of CryptoWall version 4. In total, 57 attempted infections have been witnessed.
Figure 1 CryptoWall v4 attempted infections
The samples have reportedly originated from phishing emails; however, this has yet to be confirmed. The following two URLs have been witnessed delivering this new version of CryptoWall:
- http://46.30.43[.]183/syria.exe
- http://46.30.45[.]110/analitics.exe
Both of the above IP addresses are located in Moscow, Russia, and are hosted by Eurobyte VPS hosting provider.
CryptoWall Modifications
The CryptoWall authors have made multiple modifications to the malware in this version. Fortunately, the majority of the code base has remained consistent with version 3. As such, reverse engineers may use structures and decryption scripts that worked on previous samples. One of the more noticeable changes in the newest revision of CryptoWall is the updated ransom notification. As we can see below, it appears that the actors behind this threat have gotten a bit snarky with their verbiage.
Figure 2 New CryptoWall ransom message (HTML)
Readers might also notice a change in the color scheme, as the actors are now using a red, yellow, and grey combination. Previously, this color scheme used blue, green, and grey. It doesn’t appear as though this change has made its way to the PNG file provided to victims, which still has the same appearance as the previous CryptoWall version. Additionally, version information was removed from these messages, as previous notices specifically called the malware ‘CryptoWall 3.0’. This revision simply calls it ‘CryptoWall’.
Figure 3 New CryptoWall ransom message (PNG)
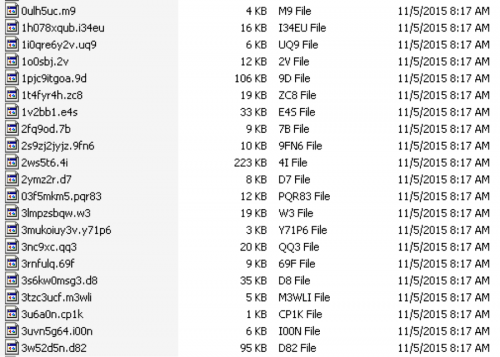
Another noticeable change is the fact that the malware will now encrypt not only the contents of targeted files, but the names of these files as well, as we can see in the screenshot below.
Figure 4 CryptoWall v4 encryption of filenames
Encryption of the filenames makes it much more difficult for victims to identify what files exactly were encrypted.
On the network communications side, the CryptoWall authors have streamlined the process a bit to minimize the number of HTTP requests made. Network encryption appears to remain consistent with previous versions, using RC4 with a key provided in the GET request (note that the key is sorted prior to decryption). However, the outbound requests to the following URLs are no longer present:
- http://ip-addr.es
- http://myexternalip.com/raw
- http://curlmyip.com
Additionally, the PNG file hosted by the C2 server is no longer provided in a separate response. Instead, it is included when the C2 server provides the RSA public key.
These changes limit the network-based exposure of the malware, making it more difficult for network-based security solutions to detect it.
Conclusion
As of this writing, it appears that this new version of CryptoWall is still in early use by attackers. Palo Alto Networks has witnessed 10 unique samples being used to conduct 57 attempted infections. The malware itself includes multiple modifications, including how files are encrypted as well as how network communications occur. Additionally, the content as well as the look and feel of the ransom notification have changed and appear to still be in development based on the discrepancies between the HTML files and PNG files shown to victims.
CryptoWall has been responsible for many millions of dollars in damages worldwide. The threat of ransomware has remained active for a number of years now, and shows no signs of stopping in the future. Individuals should remain vigilant about ensuring that suspicious emails are not opened and skeptical about navigating to unknown websites that are not trusted.
Palo Alto Networks WildFire customers are protected against this threat. Additionally, the latest version of CryptoWall is identified via the ‘CryptoWall’ tag in AutoFocus.
Appendix
The following SHA256 hashes of CryptoWall version 4 have been identified.
4ae64579fa0efd0be978c6797efe05d31517985b28ebd95dcadfacf3bb551f56
2d04d2a43e1d5a6920a806d8086da9c47f90e1cd25aa99b95af182ee9e1960b3
4c2d28a7ed5cf44b3641a9f6a5dfedd97b420e720376cb986062580cbda5ad3d
41fa6b1f25ae106a1a1c1734e6018e7c10efb4e31e4851d8fdc1a028d0249d63
bf352825a70685039401abde5daf1712fd968d6eee233ea72393cbc6faffe5a2
3a73bb154506d8a9a3f4f658bac9a8b38d7590d296496e843503323d5f9b7801
3509700469dfe290fa10f67490d763d14443ba7e571c974132bac0b385e69667
9bd0e36a9cc6a0754d695b27433fafba4f6c8ef82b71ccf20903d3d109e8e804
299b298b433d1cc130f699e2b5c2d1cb3c7e5eb6dd8a5c494a8c5022eafa9223
dd64fb6df49a21bfc3f59ac25346beec05f1f9414de6584b4469a6085e7efdd2
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.