This post is the first in a new series titled Examining the Cybercrime Underground. Each post will delve into different aspects of how cybercriminals operate, using current examples of tools and techniques. What are their tools of the trade? How do they get them? How do they overcome challenges posed by security and anti-fraud systems? How do criminals profit from scams and turn stolen data into cash? Answering these questions will help readers better understand one of their primary cyberadversaries and use that knowledge to better protect their networks.
What is a crypter?
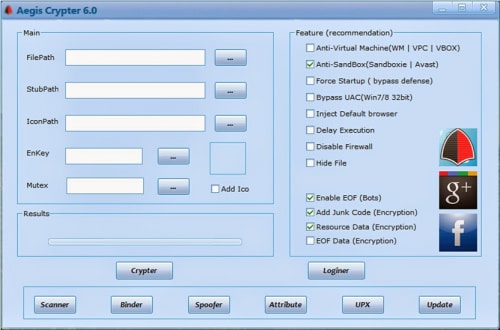
Crypters are software tools that use a combination of encryption, obfuscation, and code manipulation of malware to make them FUD (Fully Undetectable) by legacy security products.
Why do attackers use crypters?
To understand the role that crypters play in cybercrime, it’s helpful to try to understand the cybercriminal mindset. The Holy Grail for cybercriminals is fully undetectable malware that would allow them to use the same malware repeatedly without being detected by a security solution. They also want their attacks randomized to make sure that the failure of one attack won't affect the outcome of attacks against other victims.
Knowing this, let's look at a common attack scenario used by cybercriminals. Cybercriminals often use Remote Administration Tools (RAT) to steal online banking credentials, credit card numbers, personal data, or other valuable pieces of information. One of the oldest and and most widely used RAT is DarkComet. This tool lets criminals perform a variety of functions including:
- Steal passwords and credit card numbers
- Download, upload, delete, and rename files
- Install viruses and worms
- Edit a computer’s registry
- Silently install applications
- Log keystrokes or install keystroke capture software
- Open a CD-ROM tray
- Control the mouse or keyboard
- Record sound with a connected microphone
- Record video with a connected webcam
- Shutdown, restart, or log-off the computer
- Record and control a victim's screen remotely
- View, kill, and start tasks in task manager
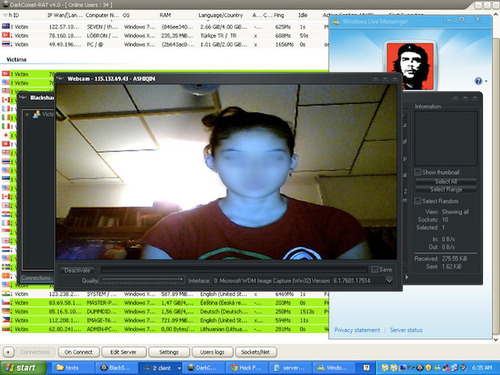
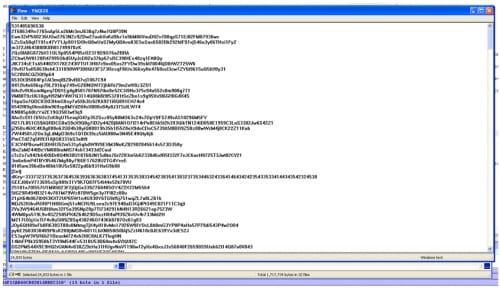
This screen shot, for example, shows an attacker eavesdropping on a webcam session using a RAT on the attacker's CNC server:
But using DarkComet is a problem for the attacker's perspective, because almost any legacy security solution can detect it.
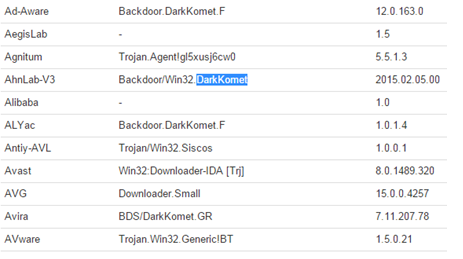
For example, this DarkComet sample has 47/56 detection rate from VirusTotal.com
sha256 - 2e93eb3e3266cf53280ba7314eefb5727fbe0277fe7ccba53d2e5355417a76f0
However, using crypters will allow the cybercriminal to bypass legacy security solutions and use the DarkComet tool undetected.
Famous Crypters
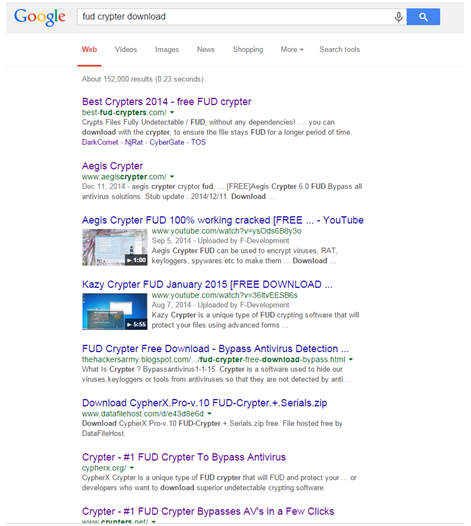
How does a newbie cybercriminal find himself a crypter? It’s surprisingly easy. A Google search for “fud crypter download” yielded 152,000 results, including places where crypter software can be purchased just as easily as a legitimate software download.
Palo Alto Networks researchers recently detected a new cybercrime campaign using the notorious DataScrambler crypter, previously disclosed and analyzed in the Unit 42 research paper 419 Evolution.
Data scrambler updates
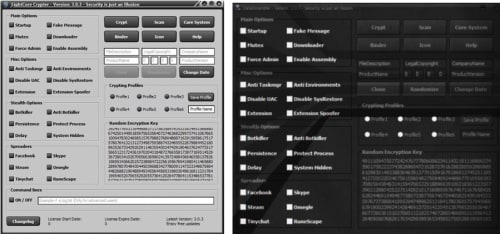
It seems that since the publication of our report the crypter developer/seller rebranded the crypter “LightCore" as "DataScrambler."
LightCore crypter GUI on the left compared to DataScrambler GUI on the right.
Features comparison
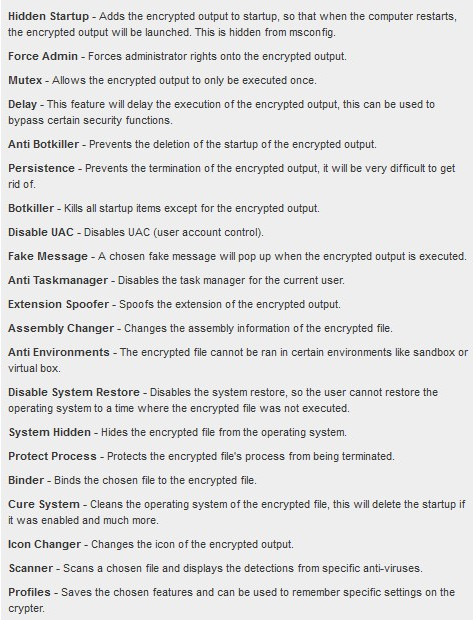
LightCore feature list is identical to the DataScrambler's feature list mentioned in the 419 Evolution paper. Even the order in which the features are listed order remained the same:
This is the promotions website page content:
"Welcome to DataScrambler!”
DataScrambler is the most advanced crypter on the market and has tons of features for a cheap price. You cannot go wrong with our product and on top of the cheap prices, you get free support and updates.
Full support for “customers”
The "semi-commercial" seller offers full support services, and the following is one attacker’s instructions for his "customers":
"I want to make it clear to all customers, in case the crypted file should become detected, it will be updated within 48 hours. Please do not post your issues or detections in the sales thread. For help with DataScrambler, click on the help button, Please read the guide before contacting me."
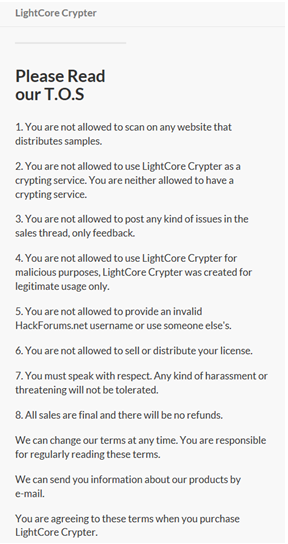
Terms of service comparison
Original Crypter developer/seller identity
As it seems that the original DataScrambler developer/seller has changed, there are two different scenarios:
- The original developer is using a new identity, or
- The original developer sold the crypter code/copyrights to another developer/seller
Based on publicly available data, the original identity behind DataScrambler is:
Name: Mace Michael
Street: 1807 Frederiksberg C
Postal Code: 1529
City: Koebenhavn
Country: DK
Phone: +4523702947
Email: macekings@gmail.com
MSN: theheadmaster151@live.com
Skype: supporter747
We also connected him to other Crypters that he apparently sold. TITANCRYPTER.COM is written in his name.
ADDAM`S FUD CRYPTER | FUD More Than 1 Month | BYPASS KIS-AVG | Extension Changer
Information:
Kaspersky Test (DarkComet bypass kis2012)
Sonar Test
Avg Test
Extension Changer
MSN : theheadmaster151@live.com
Skype : supporter747 - the same as the contact of Data Scrambler
Client Mesh RAT
"I am Reseller on Client Mesh RAT also
TO GET SPECIAL DISCOUNT USE THE COUPON CODE 'head2015' WHEN CHECKING OUT TO BUY IT FOR $35 ONLY!
https://www.sinister.ly/Thread-ClientMesh-RAT-In-Built-FUD-Crypter-Stable-DDoSer-No-PortForwading-40-Lifetime
this market is managed by unverified@hotmail.com
Contact Information:
MSN : theheadmaster151@live.com
Skype : supporter747" - the same as the contact of Data Scrambler
The current Crypter developer/seller identity
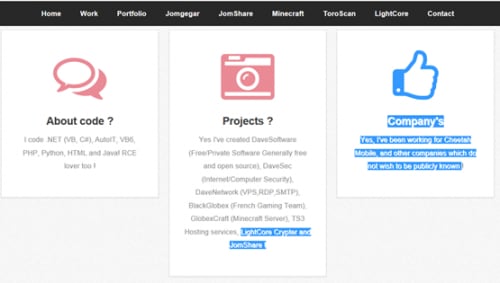
This person mentioned that in the past he worked for Cheetah Mobile (the number two Internet and mobile security company in China which is not related to this crypter in any way). But we can assume the developer's security knowledge and experience was to develop this crypter.
Case study: the saga continues
A recent attack using advanced crypter starts by spear phishing with RAR attachment:
Inquiry No: QP #1400358.1 URGENT INQUIRIES
Expand Messages
Jason Clerk
Apr 23, 2014
1 Attachment 1.8 MB
1.8 MB
New Purchase Order.rar
Dear,
Please quote us your best price for the following items, if this order
will be possible to be moves up in one week? Buyer wants them urgent!
You will find the Artwork and the new purchase order at this LINK:
See attached on the LINK you will find the new order:
LINK: https://app.box.com/s/xxxxxxxxxxxxxxxxxxxxxx
Please state of the following:
Price Validity
Price Term
…….
Yours Faithfully
for DENAI SUPPLY & SERVICES LTD
Jason Clerk
Sourcing Procurement Clerk
E-mail :jason.clerk@...; sales@...
H/P : 011-15762383
DENAI SUPPLY & SERVICES LTD ….
Exposing the attacker
In another attack, the attacker sent the spear phishing mail under a stolen identity, "GPS Trading" company founder and CEO, Mr. Panos Dimitriadis. The attachment name is Quotation_inquiry.scr (also sent to import[at]gpstrading.com).
Please note that GPSTrading Company is not connected to this attack and the attacker used their CEO’s identity in an effort to exploit the victim’s trust and to increase the infection’s probability of success.
We have discovered the following new attacks, publicly unknown so far, using those sha256 hashes:
a3cedb916a21c89b6c17bf1a816d5e9dcbf0fd3ce5a7d42b449758d45788165a
02c80443fb49915b1943b44ab8ec4dce5b1ca53f3fcdb84fae23abcf45d34a66
f2991b653686dee801b1fb4163cc46343aa8cfdcc601b9a9acc31399e7548af5
38ccb84bfc5899317926b7384904c1987dcd6cf70397850050fafa34b1c85134
2b66b0aadabc85736226382a47972bfb950861ec0d218d7c5c45fd8ca6594717
623815f40ffceaec8eb08294750c89ad94a54694414fd8a70a965a71e122fc69
The CNC Server address won’t be published here because it’s still active. It is a Windows based server with FTP, cifs and Windows terminal server interfaces.
In-depth analysis
The file attached to the email “New Purchase Order.rar” contains: first stage SFX infector - sample.exe
sha256 - 02c80443fb49915b1943b44ab8ec4dce5b1ca53f3fcdb84fae23abcf45d34a66 unknown to VirusTotal.com
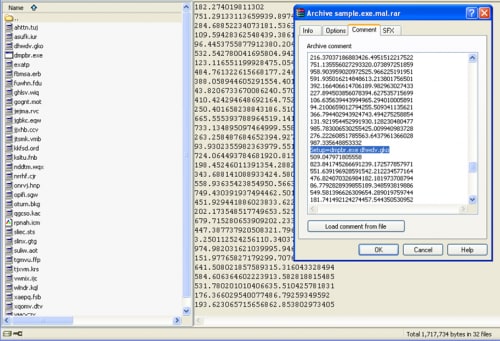
sample.exe is SFX (self-executable) with a fake pdf icon that contains one executable file and many others with random extensions:
The SFX contains a lot of junk commands (for bypassing legacy security solutions) but in the in the middle it hides the command to auto-execute dmpbr.exe with parameter dhwdv.gko. This is one of the files in the SFX.
AutoIt application - Dmpbr.exe
This is a verified and signed AutoIt application:
sha256 - fb73a819b37523126c7708a1d06f3b8825fa60c926154ab2d511ba668f49dc4b
It’s a benign file although on Virus Total it scores 2/56 (2 false positive from VirusTotal.com).
Crypter's first stage - dhwdv.gko
AutoIt script – this is the crypter's first stage.
sha256 - f8dc0013a94017cc19b8f865948daf83b64692db47199a994efab032d8b737f3 unknown to VirusTotal.
The file contains a lot of junk data to bypass legacy security solutions by using obfuscated commands (like raw 435)
The script reads data from the other scripts (extracted from the SFX file) which in turn read data from another script and so on. In the end, a final obfuscated crypter script is built.
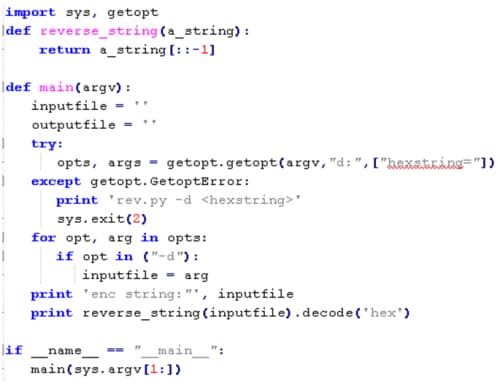
We successfully de-obfuscated the final script. For example, all strings internal AutoIt functions and Windows API functions used by the crypter are obfuscated with a simple but working algorithm (reverse hex bytes and decode them to ASCII strings).
This is a simple python tool we scripted to DE-obfuscate the strings:
Final Crypter file
sha256- 082b41f71cc5a5118e1f70f49e059763d48fc072e7fc28f8efb11076537461f3 is 3/52 from VirusTotal (but it is textual so can be changed without much effort by the attacker).
This crypter supports:
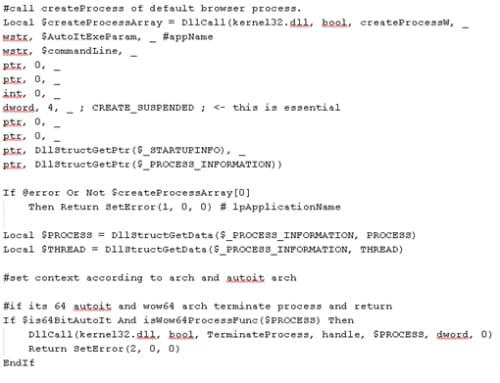
Decrypt DarkComet with RC2 decryption algorithm in memory, check the registry for the default browser, creates browser process suspended, write DarkComet to verified signed browser process, uses setThreadContext to change the execution flow to the injected code and resume the process and delete itself.
The result is signed browser executable (in our case it is Chrome and signed by Google
1c9e1a3aef25e34ea0fda67d3840c53a5449d63db6e9070f6dfc66f2fef92b15 0/55) that connects to DarkComet CNC execute attackers command.
No unsigned file is written to disk beside the AutoIt obfuscated textual files and signed trusted AutoIt.
The crypter adds its own capabilities (beside DarkComet) by reading the commands from YMQGIX, an INI file:
Commands include:
- Anti-sandbox
- Facebook password stealing
- Disable task manager (not working on the analyzed sample, because of attackers misspellings, (check wrong process name instead of taskmgr.exe)
- Disable system restore
- Anti-Emulator
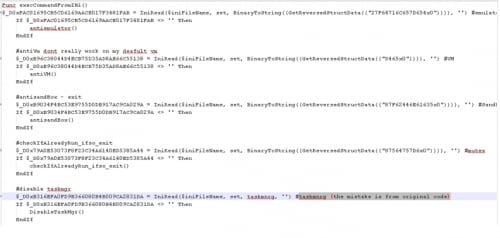
We suspect we found a bug in the anti-emulator code. It works by opening mshta.exe seven times and killing it and then loops until those processes are killed, but it is unclear why the author assumes that will protect him from emulators.
See crypter's code of anti-emulator function:
Anti-VM, download and execute of another malware
INI config file - YMQGIX
INI commands and settings for crypter
sha256 - c547ad05ebed04bad9e5509cb979413fb05c88bfab6313ef110a00b035de9aad is unknown to VirusTotal.
rc2 encrypted malware extap
rc2 encrypted malware decrypted by the crypter on runtime
sha256-7f88d9a894da7b2ccfb331d223307cc0c94730849f4b58a8fa43513ba98c4b63 unknown to VirusTotal.
Conclusion
The cybercrime underground is evolving, and enterprises using legacy security solutions won’t be protected without a next-generation enterprise security platform. Our next post on the cybercrime underground will be focused on the after-attack phases, including how attackers use victims’ credit card data to steal money, and the current state of the phishing market underground.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.