Session Traversal Utilities for NAT (STUN) is a network protocol with standardized methods that enables an internal network address space host employing Network Address Translation (NAT) to determine its Internet-facing/public IP address.
STUN has several legitimate uses, including enablement of NAT traversal for voice over IP (VOIP), messaging, video, and other IP-based interactive communication. As an example, Palo Alto Networks wrote a blog post back in 2010 covering how STUN works with VOIP. The standard ports for STUN include 3478 for TCP and UDP, as well as 5349 for TLS. In the information security tradition of turning things on their side and looking for interesting findings, this post focuses on the misuse of STUN by malware and associated trending.
The impetus for closer inspection of malware’s use of this protocol was a Stop Malvertising report on Dyreza, which noted how the banking trojan employed STUN to determine an infected host’s public IP behind a NAT. While the variant analyzed included a fallback mechanism of reaching out to icanhazip.com in the event STUN didn’t work, its inclusion of STUN functionality still caught our attention.
To start our investigation we searched the Palo Alto Networks WildFire platform for samples flagged as malware that had communicated with the STUN servers listed in the Stop Malvertising report:
- callwithus.com
- voiceeclipse.net
- sipgate.net
- ekiga.net
- ideasip.com
- internetcalls.com
- noc.ams-ix.net
- phonepower.com
- voip.aebc.com
- voipbuster.com
- voxgratia.org
- ipshka.com
- faktortel.com.au
- iptel.org
- voipstunt.com
- org
- taraba.net
- taraba.net
- l.google.com
- l.google.com
- l.google.com
- l.google.com
- l.google.com
- schlund.de
- rixtelecom.se
- voiparound.com
- viagenie.ca
- stunprotocol.org
- 2talk.co.nz
Figure 1 displays these results, showing a notable spike in July 2014 that remains elevated through September 2014.
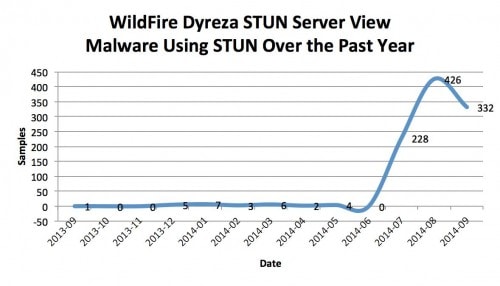
Figure 1: Malware leveraging STUN servers listed in Stop Malvertising report on Dyreza
It also became clear that Dyzera is just one of the malware families that employed STUN capabilities. This raised two additional questions:
- What would an expanded STUN server list search show from a trending perspective?
- Which are the most popular STUN servers for WildFire observed malware samples?
Based on an extended STUN server list found here, we searched WildFire again for associated samples that were flagged as malware. Figure 2 reveals generally higher numbers over the year with two very interesting peaks, one in January 2014 and the other in March 2014. Notably, these peaks are 3.0 to 3.3 times larger than peak ranges found in the Dyreza report subset.
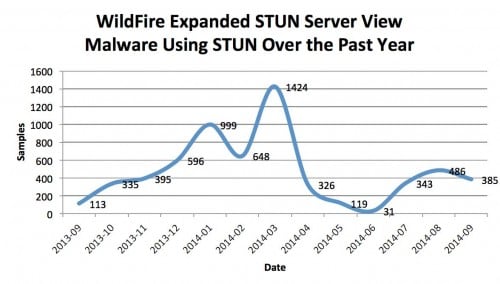
Figure 2: Malware leveraging extended STUN server list
Analysis of STUN servers listed in the Stop Malvertising report that were employed by malware over the past year revealed that the most popular was stunserver.org, which held the greatest lead at 69 samples (6%), with the immediate runner up at 56 samples (5%). Table 1 summarizes the malware counts associated respective STUN server usage.
| STUN Server | Count |
| stunserver.org | 69 |
| stun.noc.ams-ix.net | 56 |
| stun.ekiga.net | 53 |
| stun.voxgratia.org | 49 |
| stun.phonepower.com | 47 |
| stun.internetcalls.com | 45 |
| stun.voipbuster.com | 44 |
| stun.callwithus.com | 42 |
| stun.l.google.com | 42 |
| stun.ipshka.com | 41 |
| stun.sipgate.net | 40 |
| stun4.l.google.com | 40 |
| stun.voip.aebc.com | 39 |
| stun.voiparound.com | 39 |
| stun.ideasip.com | 37 |
| stun.iptel.org | 37 |
| stun.schlund.de | 36 |
| stun.faktortel.com.au | 33 |
| stun2.l.google.com | 33 |
| stun.rixtelecom.se | 32 |
| stun.voipstunt.com | 32 |
| numb.viagenie.ca | 30 |
| stun.stunprotocol.org | 30 |
| stun3.l.google.com | 29 |
| s1.taraba.net | 28 |
| s2.taraba.net | 24 |
| stun1.l.google.com | 24 |
| stun1.voiceeclipse.net | 20 |
| stun.2talk.co.nz | 17 |
Table 1: Malware usage over one year per STUN server listed in Stop Malvertising report on Dyreza
We performed similar analysis on the extended list of STUN servers, where we found a much larger lead for the number one server, stun.qvod.com, at 4705 samples (75%), with its next runner up being stun.qq.com at only 489 samples (8%). Table 2 summarizes the malware counts associated respective STUN server usage.
| STUN Server | Count |
| stun.qvod.com | 4705 |
| stun.qq.com | 489 |
| stunserver.org | 69 |
| stun.noc.ams-ix.net | 56 |
| stun.ekiga.net | 53 |
| stun.voxgratia.org | 49 |
| stun.phonepower.com | 47 |
| stun.internetcalls.com | 45 |
| stun.voipbuster.com | 44 |
| stun.callwithus.com | 42 |
| stun.l.google.com | 42 |
| stun.ipshka.com | 41 |
| stun.sipgate.net | 40 |
| stun4.l.google.com | 40 |
| stun.voip.aebc.com | 39 |
| stun.voiparound.com | 39 |
| stun.ideasip.com | 37 |
| stun.iptel.org | 37 |
| stun.schlund.de | 36 |
| stun.faktortel.com.au | 33 |
| stun2.l.google.com | 33 |
| stun.rixtelecom.se | 32 |
| stun.voipstunt.com | 32 |
| numb.viagenie.ca | 30 |
| stun.stunprotocol.org | 30 |
| stun3.l.google.com | 29 |
| s1.taraba.net | 28 |
| s2.taraba.net | 24 |
| stun1.l.google.com | 24 |
| stun1.voiceeclipse.net | 20 |
| stun.2talk.co.nz | 17 |
| stun.softjoys.com | 2 |
| stun.veoh.com | 2 |
Table 2: Malware usage over one year per extended STUN server list
These listings show that there are only four additional non-Dyreza-associated STUN servers that have been observed by WildFire with relation to malware: the first two (stun.qvod.com and stun.qq.com) and last two (stun.softjoys.com and stun.veoh.com). This remains significant considering that the first two servers account for approximately 83% of malicious STUN traffic observed by WildFire.
Figure 3 presents a combined view of QVOD, QQ, and Dyreza-associated STUN server usage. This figure accounts for over 99% of malicious STUN traffic observed by WildFire over the past year.
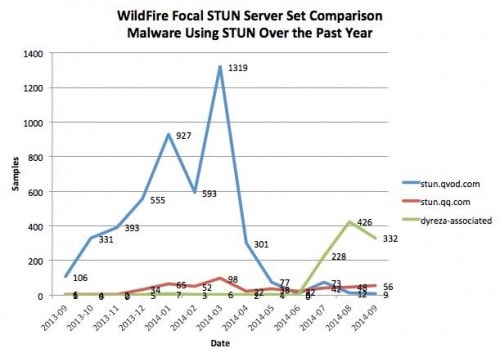
Figure 3: Comparison counts of malware leveraging QVOD, QQ, and Dyreza-associated STUN servers.
There are at least two points of interest in this figure. The first is the sharp decline in QVOD STUN server traffic around April 2014. Our research leads us to believe these this event correlates with the shutdown of the QVOD video streaming and downloading service due to piracy concerns. The second point of interest is the sudden rise in Dyreza-associated STUN server usage starting around July 2014. This is at least in part due to the incorporation of STUN capability into Dyreza, although other families of malware were also observed communicating with those servers.
It is our belief that this trending of STUN capabilities in malware supports two goals for attackers:
- Leverage innovation: As new protocols gain traction and malicious actors rediscover older ones, it shouldn’t be a surprise that the benefit of legitimate use is eventually tested and incorporated for malicious purposes.
- Hide in plain sight: Given a popular service and/or protocol, there is a higher likelihood that malware that utilizes similar communications can achieve equivalent success in its misuse, as it is allowed through the same security controls.
While the inclusion of STUN capability in software is not in itself indicative of malware, it remains interesting from a trending perspective towards characterizing and managing threats. This can include extrapolating potential attacker sophistication and objectives/motivations, as well as determining the best course of action for detection, mitigation and response. For example, STUN has its shortfalls, mainly when employed with a symmetric/bi-directional NAT. Symmetric NAT is most often found in large businesses, which could also explain the use of fallback techniques towards maximizing the target space for an attack. Ultimately, this highlights the importance of visibility on and control of network traffic as two major weapons in the arsenal of modern incident response teams.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
